Leveraging AI for Dynamic Risk Assessment
Understanding the Scope of Dynamic Risk Assessment
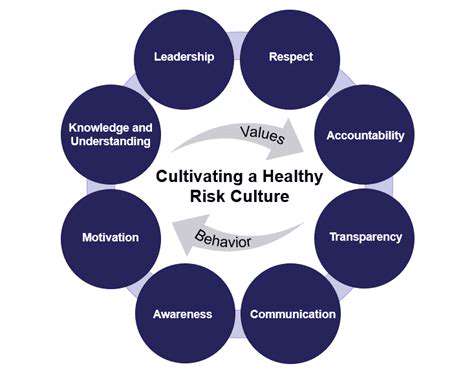
Dynamic risk assessment represents a paradigm shift in how organizations evaluate threats, moving away from static, periodic reviews toward continuous, adaptive analysis. This methodology recognizes the fluid nature of risks across sectors, including cybersecurity and financial markets. The capacity to adapt in real-time proves indispensable for neutralizing emerging threats before they escalate. Artificial intelligence empowers organizations with a panoramic view of risk landscapes and their evolutionary trajectories.
AI's Role in Data Collection and Processing
Machine learning systems demonstrate unparalleled proficiency in handling enormous datasets, aggregating critical information from disparate sources ranging from IoT sensors to digital media streams. This data-processing prowess enables organizations to conduct exceptionally detailed risk evaluations, yielding precise forecasts and preemptive countermeasures. Conventional approaches frequently falter when confronted with today's data deluge and its relentless velocity.
Predictive Modeling for Anticipating Risks
Advanced predictive analytics tools scrutinize historical patterns and current indicators to forecast potential hazards. This foresight permits organizations to implement protective measures proactively. The synthesis of longitudinal data with real-time signals empowers AI systems to detect nascent threats with remarkable precision and timeliness. Such anticipatory strategies prove vital for maintaining business continuity amidst unpredictable circumstances.
Automated Risk Response Mechanisms
Artificial intelligence facilitates instantaneous reactions to identified threats through programmed protocols. These may include automated alerts, security measure activation, or autonomous decision-making within predefined boundaries. The immediacy of automated systems proves crucial when combating rapidly evolving threats that demand split-second responses. This technological capability dramatically shrinks reaction windows and prevents minor issues from snowballing into crises.
Integrating Human Expertise with AI Capabilities
While AI demonstrates superior analytical capabilities, human judgment remains essential for contextual interpretation and ethical decision-making. Effective risk management strategies necessitate seamless collaboration between artificial and human intelligence. The incorporation of human oversight guarantees that AI-generated insights align with organizational ethics and practical realities. This symbiotic relationship ensures technology serves strategic objectives rather than dictating them.
Ensuring Data Privacy and Security in AI Systems
Deploying AI for risk analysis mandates stringent data protection protocols. Safeguarding confidential information against breaches or misuse constitutes a fundamental requirement. AI implementations must embed privacy-by-design principles while adhering to regulatory frameworks. Comprehensive security measures not only preserve institutional credibility but also foster stakeholder confidence in technological solutions. Transparent data governance practices reinforce system integrity and user trust.
Predictive Modeling for Proactive Security

Predictive Modeling Techniques
Modern predictive methodologies form the backbone of anticipatory security postures, employing sophisticated machine learning algorithms to project future scenarios. These analytical models examine historical patterns and correlations, enabling enterprises to foresee developing trends and formulate data-driven strategies. Foreknowledge of probable events permits the implementation of preventative measures that neutralize risks while capitalizing on emerging opportunities.
Data Collection and Preparation
The efficacy of predictive analytics depends fundamentally on data quality and comprehensiveness. Meticulous attention must be devoted to selecting pertinent variables and conditioning them for analysis, including addressing data gaps, anomalies, and format standardization. Proper data preprocessing establishes the foundation for accurate forecasting, whereas deficient preparation inevitably produces misleading results and ineffective countermeasures.
Model Selection and Training
The predictive analytics toolkit encompasses diverse methodologies, each with specific applications and limitations. Optimal model selection depends on problem characteristics and available data attributes. Techniques including multivariate regression, pattern classification, and temporal analysis offer distinct approaches to scenario forecasting. Choosing the appropriate analytical framework represents a critical success factor for generating dependable predictions.
Evaluation and Validation
Post-development assessment of predictive models requires rigorous performance measurement using standardized metrics. This phase evaluates the model's predictive accuracy, specificity, sensitivity, and other relevant indicators. Independent verification using fresh datasets prevents overfitting and confirms generalization capability. Thorough validation processes establish confidence in the model's capacity to generate reliable forecasts beyond the training dataset.
Deployment and Monitoring
Operationalizing predictive models demands strategic implementation planning. Successful integration involves embedding analytics within existing workflows and effectively communicating outputs to decision-makers. Continuous performance tracking and periodic model recalibration ensure sustained accuracy as conditions evolve. Maintaining predictive relevance requires perpetual refinement to accommodate shifting operational landscapes and emerging threat vectors.
Business Applications and Benefits
Predictive analytics delivers tangible value across industry verticals. Applications range from customer retention optimization in service sectors to predictive maintenance in industrial operations, significantly enhancing strategic planning and asset allocation. Potential advantages include cost reduction, operational streamlining, and revenue enhancement. Organizations harnessing predictive capabilities gain strategic advantages by preemptively addressing challenges before they materialize. This forward-looking approach promotes sustainable operations and optimal resource utilization.
Improving Incident Response with AI-Driven Insights
Prioritizing Vulnerabilities with Machine Learning
AI-enhanced incident management platforms process enormous security datasets—including vulnerability disclosures, network telemetry, and user activity logs—to rank threats by exploit probability and potential damage. This intelligent prioritization enables security personnel to concentrate on high-risk vulnerabilities, accelerating response times and reducing attack success rates. Machine learning systems continuously improve by analyzing historical incidents, detecting subtle anomalies that conventional signature-based systems might overlook.
Predictive Threat Modeling for Proactive Defense
Beyond reactive measures, AI enables anticipatory security postures through comprehensive threat modeling. By synthesizing historical attack data, current system weaknesses, and emerging threat intelligence, AI systems identify probable attack pathways and recommend preemptive hardening measures. This prognostic capability allows enterprises to reinforce defenses proactively, substantially decreasing breach probabilities.
The anticipatory methodology not only reduces operational disruptions and financial exposure but also cultivates more robust and flexible security architectures capable of evolving with the threat landscape.
Automated Incident Triage and Root Cause Analysis
Artificial intelligence streamlines initial incident handling by automatically classifying alerts and sorting incidents by severity and business impact. This automation liberates security analysts to focus on complex investigations, enabling thorough causal analysis and effective remediation planning. The optimized workflow accelerates incident resolution while simultaneously improving diagnostic accuracy and solution effectiveness.
Enhanced Security Monitoring and Threat Detection
AI-powered surveillance systems analyze security telemetry in real-time, identifying subtle indicators of compromise that evade traditional detection mechanisms. These intelligent platforms demonstrate adaptive learning capabilities, continuously refining their detection parameters as they encounter novel attack methodologies. The self-improving nature of these systems ensures security postures remain effective against constantly evolving cyber threats.
Improved Collaboration and Communication During Incidents
AI facilitates seamless coordination among security teams, executives, and first responders during critical events. By synthesizing real-time intelligence, analytical insights, and response recommendations, AI platforms enhance information sharing among stakeholders. This optimized communication framework enables synchronized response efforts, accelerating incident containment while minimizing operational disruption. Effective coordination ensures all participants operate from identical situational awareness, facilitating prompt and decisive action.