Proactive Measures for Enhanced Security
Proactive defense strategies are crucial for mitigating potential threats and vulnerabilities. Implementing these strategies involves a shift from a reactive approach to a preventative one. This proactive stance allows organizations to anticipate and address security risks before they can cause significant damage. By identifying potential weaknesses in systems and processes, organizations can implement safeguards to reduce the likelihood of breaches and attacks. This approach fosters a more secure environment by strengthening defenses and reducing the overall risk profile.
A key component of proactive defense is the continuous assessment of existing security measures. Regular security audits and penetration testing help identify vulnerabilities that may not be immediately apparent. These evaluations are essential for maintaining a robust security posture, as threats and attack methods are constantly evolving. Proactive measures also encompass employee training and awareness programs, enabling personnel to recognize and respond appropriately to potential security incidents.
Identifying and Addressing Potential Threats
A crucial aspect of proactive defense is the identification and assessment of potential threats. Understanding the evolving landscape of cyber threats is paramount, as attackers are constantly innovating their tactics. This requires a deep understanding of the various attack vectors, including phishing, malware, and social engineering. Thorough research and analysis of current threat intelligence are essential for identifying emerging risks and adapting security measures accordingly.
Organizations must develop robust incident response plans to effectively manage and mitigate any security breaches that may occur. This involves having clear protocols for containing the incident, investigating its cause, and implementing necessary remediation steps. Proactive threat identification allows organizations to anticipate potential problems and develop strategies to mitigate their impact. Implementing these strategies in advance of a breach can significantly reduce the long-term consequences.
Implementing Robust Security Protocols
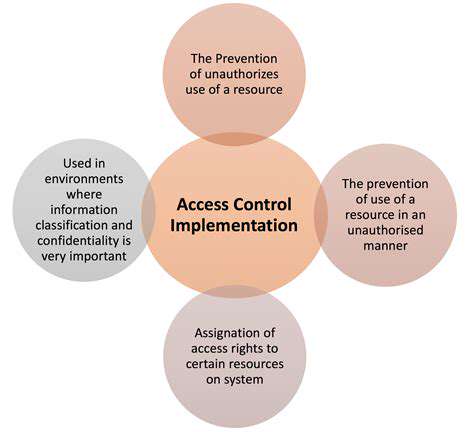
Implementing strong security protocols across all systems and processes is vital for maintaining a robust security posture. This includes implementing strong access controls, regularly updating software and hardware, and employing multi-factor authentication. These measures directly reduce the attack surface and significantly limit the potential for unauthorized access and data breaches. Implementing these protocols can be complex, but the investment in time and resources pays off in the long run.
Regular security awareness training for employees is also a cornerstone of proactive defense. Educating staff about common threats and best practices for avoiding them can significantly reduce the risk of successful attacks. This training should be ongoing and adaptable to the evolving threat landscape. Security awareness training is an invaluable investment that fosters a culture of security within the organization.
Furthermore, data encryption and secure data storage practices are critical components of a proactive security strategy. Protecting sensitive information from unauthorized access and disclosure is paramount. Implementing these protocols minimizes the risk of data breaches and the potential for reputational damage or financial loss.
Comprehensive security protocols also include regular vulnerability assessments and patching of known software flaws. Regularly reviewing and updating these protocols is essential for maintaining effectiveness. This proactive approach minimizes the likelihood of an attack and ensures the confidentiality, integrity, and availability of sensitive data.
Employee Education and Awareness Programs
Employee Education Programs
Comprehensive employee education programs are crucial for fostering a strong and productive workforce. These programs should not only cover essential company policies and procedures, but also provide opportunities for professional development and skill enhancement. Investing in employee education demonstrates a commitment to their growth and career advancement, ultimately boosting morale and productivity. This investment can also help employees feel valued and appreciated, contributing to a more positive work environment.
Effective education programs should be tailored to the specific needs of the employees and the company. This includes identifying skill gaps and providing training to address them. Regularly assessing the effectiveness of these programs is essential for continuous improvement and ensuring they remain relevant and impactful.
Importance of Awareness Campaigns
Raising employee awareness about critical issues, such as workplace safety, ethical conduct, and company values, is paramount for a thriving work environment. Awareness campaigns can significantly reduce the likelihood of accidents, improve ethical decision-making, and strengthen company culture. These campaigns should be interactive and engaging, using various methods like workshops, presentations, and online resources.
By promoting awareness about important topics, companies can empower their employees to make informed decisions and contribute to a more positive and productive work environment. This approach fosters a sense of shared responsibility and promotes a commitment to company values.
Understanding Compliance Regulations
Staying abreast of and ensuring compliance with relevant laws and regulations is critical for any organization. Employees need a clear understanding of the company's compliance policies and procedures, as well as the legal frameworks that govern their work. This knowledge is essential for preventing legal issues and maintaining a strong ethical foundation within the company.
Effective Communication Strategies
Clear and effective communication channels are vital for disseminating important information to employees. This includes regular updates on company performance, policy changes, and industry trends. Transparent communication fosters trust and understanding, enabling employees to feel more connected to the company's goals and objectives. Furthermore, open communication channels allow for feedback and engagement, which can lead to innovative ideas and improved problem-solving.
Promoting a Culture of Continuous Learning
A culture of continuous learning encourages employees to develop new skills and knowledge throughout their careers. This can involve offering access to online courses, workshops, or mentorship programs. Promoting a culture of continuous learning fosters employee engagement and innovation, while also preparing them for future challenges and opportunities. It also demonstrates that the company values their growth and development, ultimately leading to a stronger and more capable workforce.
Understanding the underlying reasons behind problematic situations is crucial for effective intervention and resolution. Pinpointing the specific factors contributing to a problem, whether it's a malfunctioning machine, a decline in sales, or a breakdown in communication, allows for a targeted approach to fixing the issue. Thorough investigation is key to identifying the root causes, rather than merely treating symptoms. Often, addressing the root cause prevents the problem from recurring, leading to long-term solutions.
Robust Data Backup and Recovery Strategies
Understanding the Importance of Data Backup
Robust data backup and recovery strategies are crucial for mitigating the impact of ransomware attacks. Without a recent and reliable backup of your critical data, the repercussions of a successful ransomware attack can be catastrophic, ranging from significant financial losses to severe operational disruptions. Implementing a comprehensive backup plan is a proactive measure to safeguard your business's valuable information and ensure business continuity in the event of a cyberattack.
Regular backups, stored in a secure offsite location, provide a critical lifeline. This allows for swift restoration of data and systems, minimizing downtime and the potential for irreversible data loss. A well-defined backup strategy is not just a reactive measure, but a proactive investment in your organization's resilience and ability to bounce back from cyber threats.
Implementing a Multi-Layered Backup Strategy
A single backup solution is often insufficient. A robust multi-layered backup strategy employs various methods to ensure data redundancy and protection. This could involve using cloud-based backup solutions for offsite storage, combined with regular on-site backups to the local hard drive. This approach minimizes the risk of data loss from a single point of failure, whether it's a ransomware attack, hardware malfunction, or natural disaster.
Furthermore, consider incorporating versioning in your backup strategy. This allows for restoring previous versions of files, crucial in cases where a ransomware attack modifies or encrypts data. Employing a multi-layered approach significantly enhances the resilience of your data backup and recovery process.
Choosing the Right Backup Technology
Selecting the appropriate backup technology is paramount for efficient and effective data protection. Consider factors such as the volume of data, the frequency of backups needed, and the level of security required. Different technologies, like cloud-based storage, dedicated backup appliances, or hybrid solutions, cater to varying needs and budgets. Thorough research and evaluation are essential for identifying the backup technology that aligns with your organization's specific requirements.
Prioritize the security protocols of the chosen technology. Look for solutions that incorporate encryption, access controls, and robust security measures to protect your backups from unauthorized access. Security should be a core consideration in your selection process.
Regular Testing and Validation of Backups
Regularly testing and validating your backups is critical to ensuring their effectiveness. Simulated ransomware attacks or planned system failures provide valuable insights into the backup process's efficiency. This proactive approach allows you to identify vulnerabilities and weaknesses in your backup strategy well before a real incident occurs.
Testing the restoration process is equally important. Verify that you can quickly and reliably restore data from backups to ensure that the backups are usable in a real-world disaster scenario. Regular testing helps to fine-tune your backup procedures and instill confidence in your ability to recover from a ransomware event.
Data Recovery Plan and Procedures
A comprehensive data recovery plan outlines the steps to be taken in the event of a ransomware attack or other data loss incident. This plan should detail the roles and responsibilities of each team member, the communication protocols, and the specific steps for restoring data from backups. A well-defined data recovery plan is a crucial aspect of your overall ransomware mitigation strategy.
Develop a clear escalation path for reporting incidents and coordinating the recovery process. This will ensure a coordinated and efficient response, minimizing downtime and potential further damage. A structured plan can significantly reduce the impact of a ransomware attack, both in terms of financial loss and operational disruption.
Security Awareness Training for Employees
Employee training on ransomware awareness is vital. Educate your staff about the various tactics employed by ransomware attackers, such as phishing emails or malicious websites. This will empower employees to identify and avoid potential threats, reducing the risk of successful ransomware attacks. Empowering employees to recognize and report suspicious activities is a critical first line of defense.
Regular security awareness training, combined with clear policies and procedures, creates a robust security culture within your organization. This proactive approach significantly reduces the likelihood of an attack and enhances your overall data security posture.