Ransomware's Evolving Tactics
Cybercriminals have transformed ransomware from simple file encryption to a multi-faceted threat. Today's attacks often involve data theft before encryption occurs, creating a double jeopardy for victims. This escalation in tactics leaves businesses facing not just locked files but potential public exposure of sensitive information.
Attack methodologies have grown increasingly sophisticated, targeting specific vulnerabilities while exploiting human psychology. Social engineering schemes have become more convincing, often bypassing traditional security measures through carefully crafted deception. This evolution demands comprehensive security strategies that address both technological weaknesses and human factors.
Impact on Business Operations
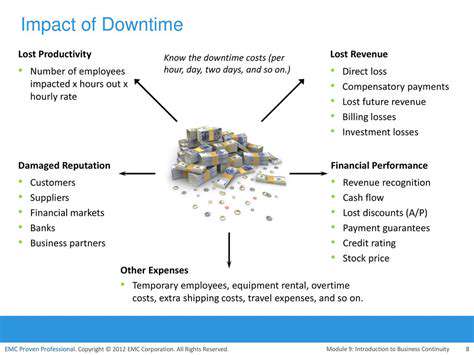
The financial toll of ransomware extends far beyond any ransom demand. Organizations experience substantial operational disruptions, with system downtime creating cascading effects across all business functions. The recovery timeline often stretches weeks or months, during which customer service and production capabilities remain impaired.
Secondary consequences frequently prove more damaging than the initial attack. Data reconstruction efforts, legal consultations, and public relations campaigns generate substantial unexpected expenses. Many organizations underestimate the lasting operational impacts that persist long after systems come back online.
Regulatory compliance becomes exponentially more challenging post-attack. Various industries face specific reporting requirements and potential penalties that demand immediate attention and resources.
Protective Measures and Response Planning
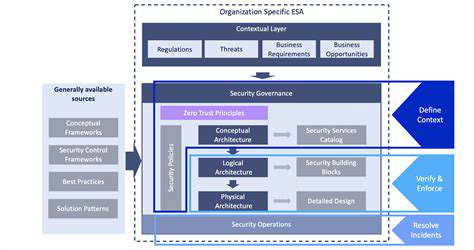
Effective ransomware defense requires layered security measures. Regular system updates, complex credential management, and multi-factor authentication form essential baselines. Comprehensive, isolated data backups represent the most reliable safeguard against encryption attacks.
Employee education plays a pivotal role in prevention. Training programs should focus on identifying sophisticated phishing attempts and establishing clear reporting protocols for suspicious communications. Technological solutions alone cannot compensate for human vigilance.
Advanced monitoring systems can detect anomalous network activity before full-scale encryption occurs. Network segmentation and properly configured firewalls help contain any breaches that do occur. Regular security evaluations identify vulnerabilities before attackers can exploit them.
The Human Factor in Cybersecurity
While technical controls are necessary, employee awareness determines overall security effectiveness. Staff members frequently serve as the initial attack vector through unintentional actions. Continuous security education programs help personnel recognize and resist increasingly sophisticated social engineering tactics.
Fostering an organizational culture that prioritizes security encourages proactive threat reporting. Employees should feel empowered to question suspicious communications without fear of reprisal. Establishing clear incident response protocols ensures timely reaction to potential threats.
The Erosion of Reputation: Long-Term Damage
The Ripple Effect of Data Loss
Ransomware consequences extend well beyond financial demands, triggering cascading reputational damage. Compromised customer data, financial records, or proprietary information creates lasting operational and trust issues. Organizations often face intense media scrutiny and public backlash during recovery efforts, compounding the initial damage.
This trust deficit manifests in tangible business impacts, from customer attrition to investor hesitancy. Market position can erode as concerns about future vulnerabilities influence consumer and partner decisions.
Financial Strain and Recovery Costs
Ransomware incidents generate substantial unplanned expenses beyond any ransom payment. Data recovery specialists, legal teams, and public relations firms all contribute to mounting costs. The financial impact often extends through multiple fiscal periods as organizations address secondary consequences.
Operational disruptions frequently lead to missed opportunities and contractual penalties. The cumulative effect can threaten financial stability, particularly for small and medium-sized enterprises.
Damage to Customer Relationships
Consumer trust suffers significantly following data breaches. Customers may abandon services or products due to security concerns, creating lasting revenue impacts. Businesses handling sensitive information face particularly severe trust challenges.
Rebuilding customer confidence requires transparent communication and demonstrable security improvements. Some organizations find offering additional protections or compensation necessary to retain client relationships.
Reputational Risk and Brand Image
Public perception often suffers long-term damage following high-profile attacks. Media coverage emphasizing security failures can overshadow years of positive brand building. The perception of vulnerability may persist even after implementing robust security upgrades.
Reputation rehabilitation requires sustained effort and often exceeds the timeframe of technical recovery. Some brands never fully regain their pre-incident standing.
Impact on Employee Morale and Productivity
Workforce disruptions extend beyond technical systems. Employees face stress and uncertainty during extended recovery periods, often while managing increased workloads. This environment frequently leads to decreased productivity and increased turnover.
Legal and Regulatory Implications
Data protection regulations impose specific requirements following breaches. Non-compliance with standards like GDPR or CCPA can result in substantial penalties. Legal proceedings may continue long after technical recovery completes.
Specialized legal counsel becomes essential for navigating post-incident regulatory requirements and potential litigation.
Long-Term Recovery and Resilience
Complete recovery from ransomware requires rebuilding both systems and trust. Implementing advanced security measures demonstrates commitment to prevention. Organizations that prioritize comprehensive security often emerge stronger, though the path requires significant time and resource investment.
Proactive Measures to Mitigate the Risk

Proactive Risk Assessment
Effective risk management begins with thorough evaluation of potential vulnerabilities. Organizations should analyze threats ranging from internal process gaps to external cyber threats. Regular assessment updates ensure alignment with evolving threat landscapes.
Impact analysis helps prioritize risks based on potential operational and financial consequences. This structured approach enables efficient resource allocation toward the most critical vulnerabilities.
Implementing Preventive Controls
Security measures should directly address identified risks through tailored solutions. Technology solutions, policy updates, and training programs all contribute to comprehensive protection. Preventive measures require ongoing evaluation to maintain effectiveness against new threats.
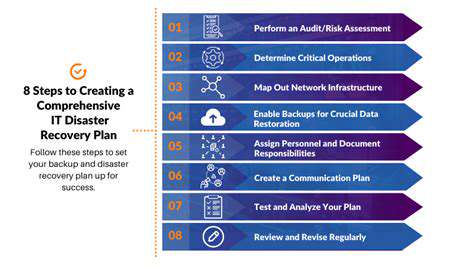
Developing Contingency Plans
Despite best efforts, incidents may still occur. Detailed response plans outline specific actions for various breach scenarios. Regular testing ensures plans remain practical and effective when needed.
Well-prepared organizations minimize disruption through established response protocols and clear communication channels.
Building a Culture of Safety and Responsibility
Security-conscious organizational culture enhances all technical measures. Employees who understand their role in protection become active participants in risk mitigation. Encouraging open discussion of security concerns fosters collective responsibility.
Ongoing training reinforces security awareness and maintains vigilance against evolving social engineering tactics.