Proactive Strategies for Enhanced Safety
Taking initiative in safety measures isn't just beneficial—it's essential for creating workplaces where risks are minimized before they escalate. Unlike reactive approaches that address problems after they occur, forward-thinking strategies concentrate on spotting potential dangers early. This shift from reaction to prevention marks a fundamental change in how organizations approach workplace safety. At its core, this method involves establishing thorough safety protocols and conducting detailed risk evaluations.
Building a culture where safety is everyone's responsibility transforms how organizations operate. When leadership and staff at all levels prioritize safety, it creates an environment where potential hazards are identified and addressed promptly. Regular training sessions, clear reporting channels, and well-defined safety procedures form the backbone of this cultural shift. Encouraging team members to voice concerns about potential dangers fosters a workplace where safety becomes second nature.
Developing a Robust Risk Assessment Process
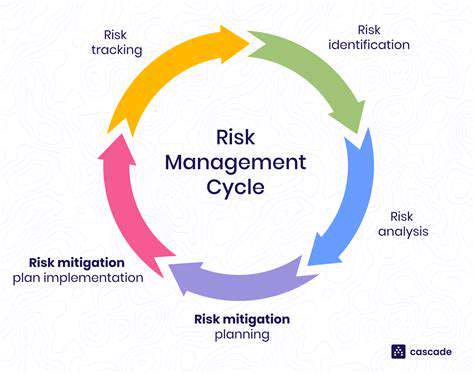
Effective hazard management begins with a meticulous evaluation process that examines every aspect of operations. This systematic approach requires identifying potential risks, assessing their probability and possible consequences, then creating appropriate countermeasures. Maintaining detailed records of these assessments proves invaluable for continuous improvement and future reference. Such thoroughness ensures minor concerns don't evolve into major incidents.
Spotting potential dangers demands careful analysis of work environments, equipment usage, and operational procedures. It requires deep understanding of daily tasks, potential error points, and environmental factors that could create hazards. This level of scrutiny allows organizations to implement targeted preventative actions that significantly reduce workplace risks.
Implementing Effective Prevention Strategies
The foundation of proactive safety lies in developing and executing comprehensive prevention plans. After identifying potential hazards, organizations must create tailored solutions ranging from safety equipment upgrades to process modifications and enhanced training programs. This forward-looking methodology creates safer work environments while dramatically decreasing accident rates.
Conducting regular safety evaluations ensures prevention measures remain effective over time. These assessments highlight areas needing improvement and allow for timely adjustments as conditions change. Continual refinement of safety protocols represents a critical component of any successful prevention strategy. The most effective safety programs view improvement as an ongoing journey rather than a destination.
Implementing Advanced Threat Detection and Response Mechanisms

Advanced Threat Detection Strategies
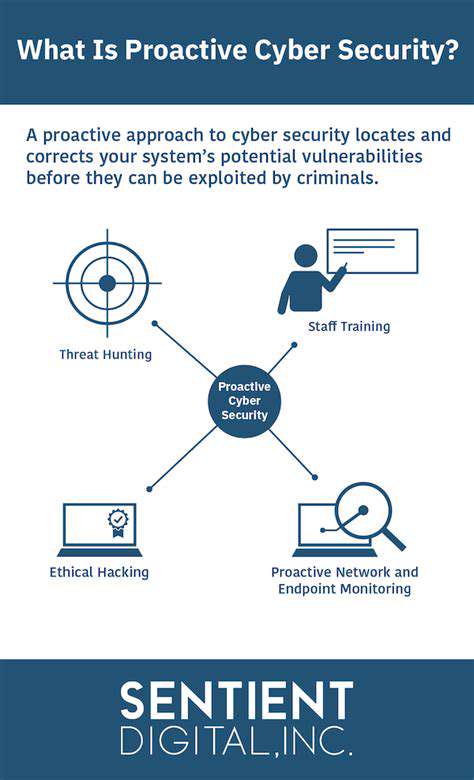
Modern cybersecurity demands sophisticated detection methods that surpass traditional signature-based systems. These advanced approaches incorporate proactive threat analysis, artificial intelligence applications, and real-time intelligence integration. Combining these elements creates a dynamic defense system capable of anticipating emerging threats before they materialize. Such comprehensive protection significantly reduces vulnerability to complex cyber attacks.
Actively searching for suspicious activities enables organizations to neutralize threats before they cause damage. Early identification of potential breaches minimizes operational impact and protects critical data assets. In today's rapidly evolving digital landscape, these advanced technologies provide essential safeguards for business continuity.
Leveraging Machine Learning
Artificial intelligence systems process enormous datasets to uncover subtle indicators of cyber threats. This capability proves particularly effective against novel attack methods that bypass conventional security measures. As these intelligent systems continuously learn from new data, their detection accuracy improves over time, strengthening overall security.
The adaptive nature of machine learning provides a powerful defense against sophisticated cybercriminals. By recognizing subtle anomalies and evolving attack patterns, these systems offer protection against previously unknown threats that might otherwise go undetected.
Integrating Threat Intelligence Feeds
Incorporating real-time threat data provides actionable insights about current cyber risks. This information enables organizations to strengthen defenses against known vulnerabilities and attack methods. Understanding attacker motivations and techniques allows for precisely targeted security enhancements. Such intelligence-driven strategies significantly improve overall protection.
Maintaining awareness of emerging threats remains critical in today's dynamic cybersecurity environment. Threat intelligence integration offers a proactive approach to identifying and mitigating risks before they can be exploited.
Proactive Threat Hunting
Active threat identification involves systematically examining systems and networks for signs of compromise. This preemptive strategy complements traditional security measures by searching for threats before they cause harm. Specialized analytical tools scrutinize system logs, network activity, and operational patterns to uncover hidden threats.
Security Information and Event Management (SIEM) Systems
SIEM solutions aggregate and analyze security data from multiple sources, providing centralized threat monitoring. These systems identify suspicious patterns that might indicate security breaches. By consolidating security information, SIEM platforms dramatically improve organizational visibility and control over potential threats.
Endpoint Detection and Response (EDR)
EDR solutions provide comprehensive protection for individual devices across an organization's network. These tools monitor endpoint activity, detect malicious behavior, and contain threats before they spread. Such protection is particularly crucial as endpoints often serve as initial attack vectors for cybercriminals.
Device-level security forms a critical layer in comprehensive protection strategies. EDR systems safeguard against data breaches and operational disruptions by securing the most vulnerable points in corporate networks.
Building a Comprehensive Security Strategy
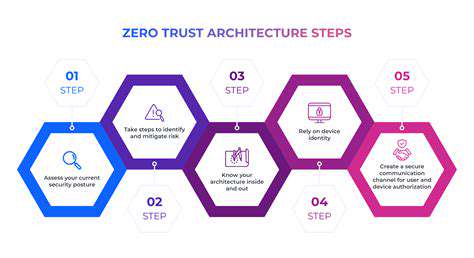
Effective threat detection requires a multi-layered approach incorporating various technologies and processes. This includes implementing strict access controls, maintaining up-to-date systems, conducting regular vulnerability assessments, and promoting security awareness. A defense-in-depth strategy significantly enhances an organization's resilience against sophisticated attacks.
Ultimately, protecting digital assets demands an integrated approach that evolves with the threat landscape. Regular strategy reviews ensure security measures remain effective against emerging cyber threats. This ongoing commitment to security forms the foundation for sustained business operations in an increasingly digital world.