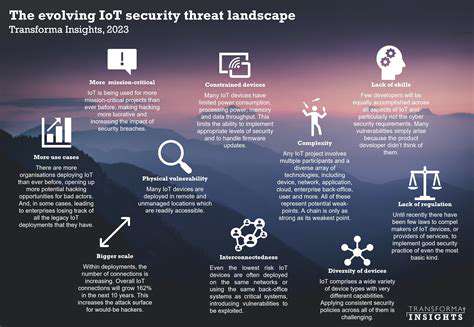
Each cloud provider operates with distinct architectures and security frameworks, creating challenges for maintaining uniform protection. Security teams must develop comprehensive strategies that span all platforms, ensuring consistent policies and practices. This requires moving beyond traditional security measures to address novel concerns like cross-platform data governance and compliance management in hybrid environments.
Security Challenges in a Multi-Cloud World
Traditional security tools often prove inadequate in dynamic multi-cloud ecosystems, where visibility gaps can create dangerous vulnerabilities. Security professionals must contend with varying access controls, identity management systems, and compliance standards across different platforms. The absence of centralized oversight frequently results in policy inconsistencies that could expose sensitive information to potential breaches.
Data fragmentation presents another significant obstacle. When information becomes isolated in separate cloud environments with differing security configurations, maintaining control becomes exponentially more difficult. These challenges necessitate specialized expertise and resource allocation that many organizations find demanding to implement effectively.
Implementing Enhanced Security Measures in Multi-Cloud Environments
Addressing these challenges requires proactive security strategies. A centralized management platform can provide the comprehensive oversight needed across all cloud deployments, enabling uniform policy enforcement and threat detection. Security training programs become indispensable, helping employees navigate the complexities of multi-cloud operations while recognizing potential threats.
Robust identity and access management (IAM) solutions form the foundation of cross-platform security. When integrated with Security Information and Event Management (SIEM) systems, they enable real-time monitoring and response capabilities. Adopting zero-trust principles further strengthens defenses by continuously verifying every access request, regardless of origin.
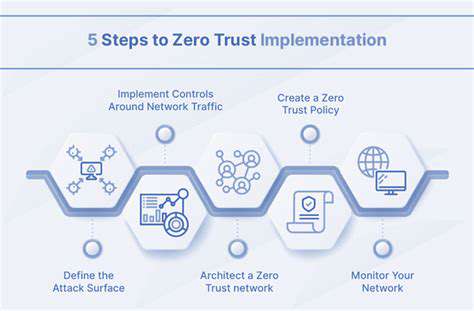
Zero Trust: A Foundation for Secure Cloud Access
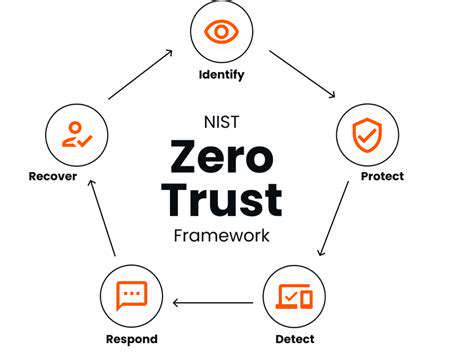
Zero Trust Architecture: A Holistic Approach
The zero-trust model operates on a fundamental principle: never assume trust for any user, device, or application without continuous verification. This represents a paradigm shift from traditional perimeter-based security, requiring ongoing authentication of all network interactions. Every access attempt must be evaluated based on current contextual factors, ensuring only properly authenticated entities gain entry.
Unlike conventional security frameworks that focus on defending network boundaries, zero trust maintains vigilance across all access points. This approach proves particularly valuable against modern threats that can originate from anywhere, whether inside or outside traditional network perimeters.
Key Components of a Zero Trust Strategy
Effective zero-trust implementation requires multiple integrated security layers. Critical elements include identity and access management (IAM), micro-segmentation, and advanced threat detection systems. IAM verifies user and device authenticity, while micro-segmentation contains potential breaches to limited network areas. Continuous monitoring solutions scan for suspicious activities, enabling rapid threat response.
Multi-factor authentication (MFA) plays a vital role in establishing trust thresholds. By requiring multiple verification forms, MFA creates substantial barriers against unauthorized access attempts, significantly enhancing overall security posture.
Benefits and Implementation Considerations
Organizations adopting zero trust architectures gain substantial security advantages, including reduced attack surfaces and improved operational visibility. Continuous verification protocols dramatically decrease the likelihood of successful breaches while supporting compliance with regulatory requirements.
Implementation requires careful planning due to the system's complexity. A phased approach helps minimize operational disruptions while allowing for proper resource allocation. Ongoing maintenance demands dedicated personnel and training investments to ensure long-term effectiveness.
Cloud Access Security Brokers (CASBs): The Sentinel of Cloud Security
Understanding the CASB Landscape
Cloud Access Security Brokers serve as critical enforcement points within zero-trust frameworks. These solutions provide centralized visibility and control across all cloud applications, enabling uniform policy enforcement regardless of user location. CASBs help organizations manage cloud adoption risks while preventing security oversights that could compromise sensitive data.
Modern CASB solutions combine agent-based and agentless technologies to balance granular control with broad visibility. This dual approach accommodates diverse organizational needs while maintaining security flexibility across expanding cloud environments.
CASB Functionality in Zero Trust
In zero-trust environments, CASBs continuously monitor all cloud interactions, verifying credentials and permissions in real-time. This constant scrutiny prevents unauthorized access by validating every request, irrespective of its origin. Behavioral monitoring capabilities detect anomalies like unusual login patterns, enabling rapid threat response.
By enforcing zero-trust principles across cloud platforms, CASBs significantly reduce vulnerability windows. Their real-time validation processes align perfectly with the zero-trust mandate to verify all access attempts without exception.
Key Benefits of Implementing a CASB
CASB implementation offers organizations comprehensive cloud visibility, revealing usage patterns and potential security gaps. Granular access controls enable customized security policies tailored to different user roles and applications. These capabilities prove invaluable in zero-trust environments where security takes precedence.
Detailed activity logs simplify compliance reporting, demonstrating adherence to industry standards and internal policies. This documentation enhances organizational accountability while reducing regulatory compliance risks.
CASB Integration with Existing Security Infrastructure
Effective CASB solutions integrate seamlessly with established security systems, including IAM and SIEM platforms. This integration creates unified security ecosystems where information flows freely between systems, enabling comprehensive threat analysis and response.
Cross-platform collaboration improves incident response efficiency, allowing security teams to coordinate efforts effectively. In zero-trust environments, this coordinated approach is essential for maintaining consistent security postures across all access points.
Beyond the Basics: Advanced Features and Future Directions

Advanced Feature Engineering Techniques
Feature engineering transforms raw data into more meaningful representations that enhance machine learning model performance. Strategic feature creation often reveals hidden data relationships that significantly improve predictive accuracy. Successful engineering requires deep understanding of domain-specific contexts and variable interrelationships.
For instance, combining customer demographics with purchase histories might uncover valuable market segmentation insights. Domain expertise proves crucial for developing features that capture nuanced business realities.
Handling Missing Values and Outliers
Real-world datasets frequently contain incomplete or anomalous data points that can distort model performance. Effective management requires careful implementation of imputation methods and outlier treatment strategies. While basic imputation techniques exist, more sophisticated approaches like k-nearest neighbors often yield superior results.
Outlier management demands particular caution, as improper handling can compromise model generalizability. Understanding each outlier's context and potential impact is essential before deciding on removal or transformation.
Dimensionality Reduction and Feature Selection
High-dimensional datasets present computational and performance challenges that dimensionality reduction techniques can address. Methods like PCA and t-SNE preserve essential information while reducing variable counts. Feature selection approaches identify the most relevant variables, improving model efficiency.
Focusing on key features enhances model interpretability while reducing overfitting risks. This optimization process creates leaner, more accurate models by eliminating redundant data elements.