Bridging the Gap Between On-Premises and Cloud Security

Optimizing On-Premise Infrastructure
Migrating from cloud-based systems to on-premise solutions often necessitates a meticulous approach to optimizing existing infrastructure. This involves a comprehensive assessment of current hardware and software configurations to identify bottlenecks and areas for improvement. Careful planning and execution are crucial to avoid disruptions and ensure a seamless transition. A critical element of this optimization process is the identification and implementation of efficient resource allocation strategies. This proactive approach ensures that resources are utilized effectively, minimizing potential performance issues and maximizing overall system efficiency.
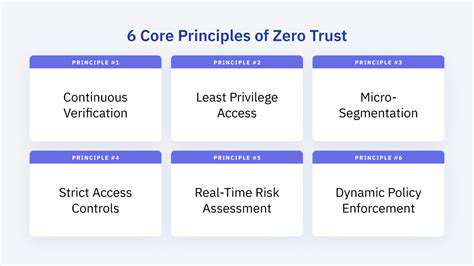
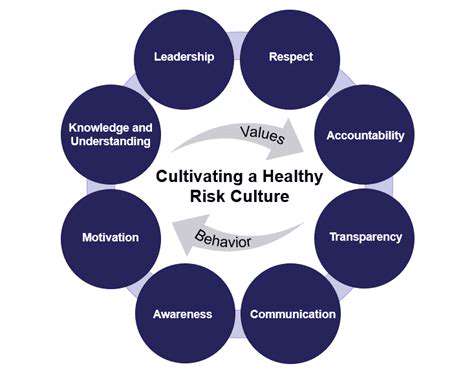
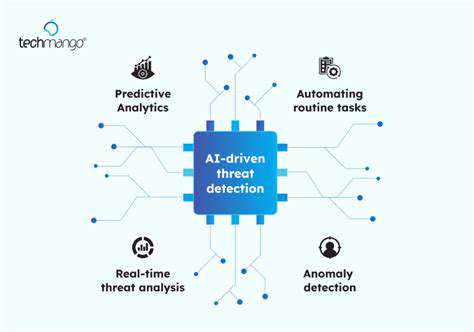
Furthermore, maintaining optimal security protocols is paramount when dealing with sensitive data stored on-premise. Implementing robust firewalls, intrusion detection systems, and access controls are essential steps to protect against cyber threats. Regular security audits and vulnerability assessments are also critical to proactively identify and address potential security gaps. Prioritizing security measures ensures the confidentiality, integrity, and availability of data, safeguarding against potential breaches.
Addressing Data Migration Challenges
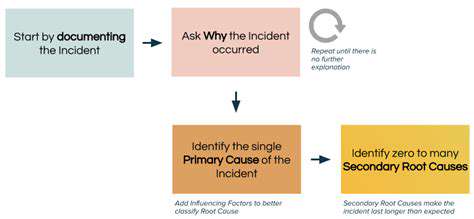
One of the most significant hurdles in transitioning to on-premise systems is the careful and efficient migration of data. Data migration projects require meticulous planning, testing, and execution to ensure a smooth and error-free transfer. This process involves not only transferring data but also ensuring data integrity and compatibility with the new on-premise environment. Careful consideration must be given to the volume and complexity of the data being migrated. It is vital to employ robust data validation techniques to ensure accuracy and completeness throughout the process.
Careful consideration must be given to the potential impact on existing workflows. A thorough understanding of the current data flows and processes is critical to designing a migration strategy that minimizes disruption to ongoing operations. Implementing appropriate change management strategies is essential to ensure that all stakeholders are informed and prepared for the changes. This proactive approach to data migration minimizes downtime and maximizes the chance of a successful transition.
Leveraging On-Premise Resources
On-premise systems offer the advantage of greater control over data and infrastructure. This control can be particularly beneficial for organizations with stringent regulatory requirements or sensitive data needing maximum security. Harnessing the control afforded by on-premise solutions allows for customization and optimization tailored to unique organizational needs. Organizations can often leverage existing hardware and software investments to reduce the overall cost of implementation.
The ability to tailor the infrastructure to specific needs is a key advantage of on-premise solutions. This customization allows for the implementation of highly specialized software and hardware configurations, optimized for specific workflows. Furthermore, the enhanced control over infrastructure can facilitate better internal collaboration and communication, enhancing overall efficiency. This level of control is especially vital for industries with stringent compliance regulations, ensuring adherence to specific standards and requirements.
Implementing robust disaster recovery and business continuity plans is also critical for on-premise environments. Establishing redundant systems and data backup procedures can help mitigate the impact of potential disruptions. This proactive approach to risk management ensures that business operations can continue uninterrupted, even in the face of unexpected events. Ensuring data availability and system resilience is a core element of successful on-premise deployments.