- Supplier security certifications and audit histories
- Geopolitical risks associated with vendor locations
- Data sensitivity levels for shared information
- Business continuity and incident response capabilities
The most robust systems incorporate both objective metrics and expert evaluations, creating multidimensional risk profiles that reflect real-world operational realities.
Identifying and Assessing Supply Chain Vulnerabilities
Vulnerability identification requires moving beyond checklist assessments. Progressive organizations now employ:
- Red team exercises simulating supply chain attacks
- Dependency mapping for critical software components
- Behavioral analysis of supplier security practices
Regular reassessment cycles are crucial, as new vulnerabilities emerge constantly. The average enterprise discovers 15-20% of their critical vendors develop new risk factors each quarter, necessitating continuous monitoring.
Scoring Methodology Considerations: Quantitative vs. Qualitative
While quantitative metrics provide objective benchmarks, qualitative insights often reveal the most significant risks. Effective systems blend:
| Quantitative Factors | Qualitative Factors |
|---|---|
| Patch latency metrics | Security culture assessments |
| Incident frequency | Executive commitment to security |
| Training completion rates | Innovation in security practices |
The most accurate risk scores emerge from synthesizing both data types through weighted scoring algorithms.
Implementing and Maintaining a Risk Scoring System
Successful implementation requires cross-functional collaboration between:
- Procurement teams establishing security requirements
- IT security departments developing assessment protocols
- Legal teams ensuring regulatory compliance
Quarterly review cycles should incorporate threat intelligence updates, ensuring the system evolves with the changing risk landscape. Automated monitoring tools can provide real-time risk scoring for critical suppliers.
Benefits of a Standardized Cyber Risk Scoring Approach
Organizations adopting comprehensive scoring systems report:
- 40-60% faster detection of supply chain threats
- 35% reduction in third-party security incidents
- Improved vendor security through transparent scoring
Standardization enables benchmarking across industries while allowing customization for specific risk profiles. This balance makes scoring systems adaptable yet comparable, creating shared security standards.
Defining the Scope and Components of Supply Chain Risk
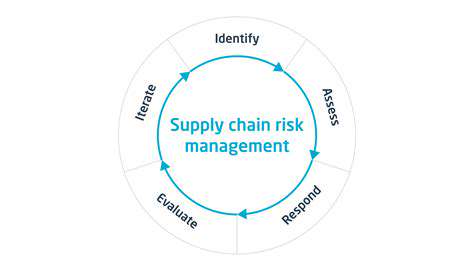
Defining the Project Boundaries
Clear project scoping forms the foundation of effective risk management. Ambiguous boundaries create assessment gaps that attackers routinely exploit. The scope should explicitly define:
- Tier 1-4 vendor inclusion criteria
- Critical system dependencies
- Data flow mapping requirements
Identifying Key Stakeholders
Effective risk management requires engagement across all organizational levels:
| Stakeholder Group | Risk Management Role |
|---|---|
| C-Suite Executives | Risk appetite definition |
| Procurement Teams | Vendor security requirements |
| IT Security | Technical assessments |
Cross-functional collaboration breaks down security silos that often create vulnerability blindspots.
Outlining Project Deliverables
Concrete deliverables should include:
- Risk heat maps for all critical vendors
- Remediation roadmaps for high-risk suppliers
- Continuous monitoring protocols
These outputs transform assessments from academic exercises into actionable security improvements.
Defining Project Metrics
Effective metrics track both security outcomes and process effectiveness:
- Mean time to remediate vendor vulnerabilities
- Percentage of suppliers meeting security benchmarks
- Reduction in supply chain attack surface
Metric selection should directly tie to organizational risk tolerance levels established by leadership.
Listing Essential Resources
Resource planning must account for:
- Specialized assessment tools
- Dedicated vendor risk analysts
- Executive sponsorship for enforcement
Under-resourced programs often fail to achieve meaningful risk reduction.
Establishing Communication Protocols
Effective communication frameworks include:
- Automated vendor risk dashboards
- Quarterly security review meetings
- Escalation paths for critical findings
Transparent communication builds trust while ensuring accountability across the supply chain.
Security fundamentals mirror culinary basics - both require mastering core principles before attempting advanced techniques. The most effective programs build on foundational controls rather than chasing the latest security trends.
Implementing and Monitoring the Scoring System
Developing the Scoring Methodology
Methodology development should follow these phases:
- Threat modeling for the specific supply chain
- Control framework selection (NIST, ISO, etc.)
- Weighting calibration through pilot testing
Industry-specific adjustments ensure relevance to actual risk profiles.
Defining Key Risk Factors
Critical risk dimensions include:
| Risk Category | Assessment Approach |
|---|---|
| Technical Controls | Configuration scanning |
| Organizational | Policy reviews |
| Geopolitical | Regional threat analysis |
Implementing the Scoring System
Implementation best practices:
- Phased rollout starting with critical vendors
- Clear scoring explainer documents
- Appeal process for disputed scores
Successful implementations balance rigor with practicality to maintain vendor cooperation.
Monitoring and Auditing the Scoring System
Effective monitoring requires:
- Automated data feeds from vendor systems
- Quarterly control effectiveness reviews
- Annual methodology validation
Continuous improvement cycles prevent score degradation over time.
Communicating and Acting on Scoring Results
Actionable reporting should:
- Highlight specific remediation steps
- Provide comparative benchmarking
- Tie scores to business consequences
Clear consequence management drives real security improvements across the supply chain.