Protecting Against Phishing Attacks
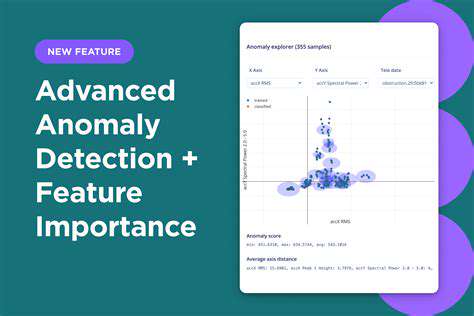
Phishing attacks are a significant threat in today's digital landscape, often leveraging sophisticated social engineering techniques to trick victims into revealing sensitive information, such as usernames, passwords, credit card details, or other personal data. These attacks can have devastating consequences, leading to financial losses, identity theft, and reputational damage. Understanding the tactics employed by phishing attackers is crucial for protecting yourself and your organization.
Recognizing phishing attempts often involves scrutinizing the email sender's address, the content of the message, and the links provided. Suspicious requests for urgent action, poor grammar, and generic greetings are common indicators. Employing multi-factor authentication and regularly updating security software are also crucial preventative measures.
Mitigating Malware Infections
Malware, encompassing viruses, spyware, and ransomware, poses a constant threat to computer systems. These malicious programs can infiltrate systems through various avenues, including malicious websites, infected email attachments, and compromised software. Malware infections can result in significant damage, ranging from data breaches to system instability and costly repairs.
Proactive measures, such as installing robust antivirus software, regularly updating operating systems and applications, and exercising caution when opening email attachments or clicking on unknown links, are essential for mitigating the risk of malware infections. Employing firewalls and practicing safe browsing habits are also crucial components of a comprehensive security strategy.
Strengthening Password Security
Strong passwords are a fundamental line of defense against unauthorized access to accounts. Using complex passwords that combine upper and lowercase letters, numbers, and symbols significantly increases the security of your accounts. Avoid using easily guessed passwords, such as your birthday or pet's name. Regularly changing your passwords and employing password managers can greatly enhance security.
Implementing Two-Factor Authentication
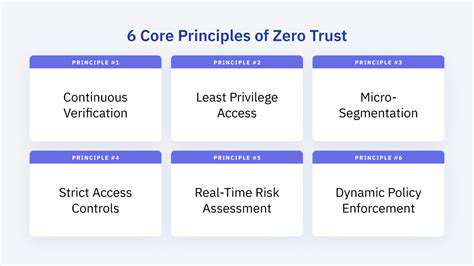
Two-factor authentication (2FA) adds an extra layer of security to your accounts by requiring two forms of verification. This typically involves a code sent to your phone or email, in addition to your password. 2FA significantly reduces the risk of unauthorized access, even if a hacker manages to obtain your password. Implementing 2FA across all your important accounts is a highly recommended practice for enhanced security.
Educating Users on Security Best Practices
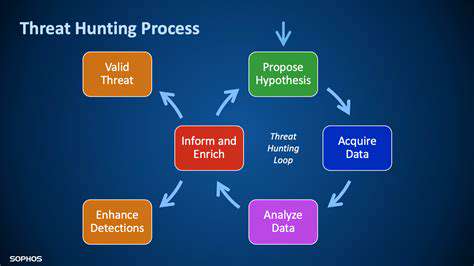
Employee training and awareness programs are crucial for fostering a culture of security within an organization. Educating users on recognizing phishing attempts, avoiding suspicious downloads, and maintaining strong passwords are vital components of a comprehensive security strategy. Regular security awareness training reinforces best practices and helps employees identify and avoid potential threats. This proactive approach significantly reduces the likelihood of successful attacks.
The Role of Secure Communication Protocols

The Importance of Confidentiality
Secure communication plays a crucial role in protecting sensitive information from unauthorized access and disclosure. Confidentiality ensures that only authorized individuals or systems can access and view the transmitted data. This is particularly vital in industries like finance, healthcare, and government, where the leakage of confidential information can lead to significant financial losses, reputational damage, and even national security risks. Maintaining confidentiality is paramount for building trust and ensuring the integrity of communication channels.
Implementing robust encryption protocols and access controls are essential elements in achieving confidentiality. These measures help protect sensitive data from interception and misuse, safeguarding the interests of all parties involved in the communication process.
Authentication and Integrity
Authentication verifies the identity of the communicating parties, ensuring that the sender and receiver are who they claim to be. This is crucial to prevent unauthorized access and manipulation of messages. Strong authentication mechanisms, like digital signatures and multi-factor authentication, are vital to building trust and confidence in the communication process.
Integrity, on the other hand, ensures that the data transmitted remains unaltered during transit. This is achieved through cryptographic hashing and digital signatures, which allow the recipient to detect any unauthorized modifications to the message.
Non-Repudiation
Non-repudiation is a critical aspect of secure communication, ensuring that the sender cannot deny having sent a message, and the receiver cannot deny having received it. This feature is essential in legal and business contexts, providing evidence of communication and transactions. Digital signatures and timestamps are crucial components of non-repudiation mechanisms, providing verifiable proof of the origin and integrity of the message.
Secure Communication Protocols
Various secure communication protocols are designed to facilitate secure data exchange. Examples include TLS/SSL for web communication, SSH for secure shell access, and PGP/GPG for email encryption. These protocols use cryptographic techniques to encrypt data, authenticate users, and ensure data integrity, providing a secure channel for sensitive information transmission.
These protocols are essential for protecting sensitive information in various applications, including online transactions, remote access, and secure messaging. Choosing the right protocol is critical to ensure the appropriate level of security and compliance with industry standards.
Compliance and Regulatory Considerations
Secure communication is not just about technical implementation; it also involves compliance with industry regulations and legal frameworks. Organizations must adhere to specific standards and guidelines, such as HIPAA in healthcare or GDPR in the EU, to ensure data privacy and security. These regulations often mandate specific security measures and protocols to protect sensitive information, and failure to comply can lead to significant penalties and legal issues.
Understanding and implementing these regulatory requirements is crucial to maintaining a secure communication environment and avoiding potential risks. Therefore, organizations need to conduct regular security assessments and audits to identify vulnerabilities and ensure ongoing compliance.
Addressing the Challenges of Software Updates and Patches
Addressing the Growing Complexity of Updates
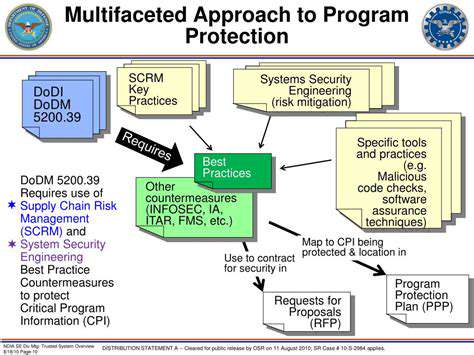
Software updates and patches are crucial for maintaining the security and functionality of automotive IoT systems. However, the sheer complexity of these systems, with their intricate interplay of embedded software, cloud connectivity, and various hardware components, presents significant challenges. Modern vehicles often house numerous interconnected modules, each requiring specific update procedures. This intricate architecture makes it difficult to ensure a consistent and reliable update process across all components without introducing vulnerabilities or disrupting vehicle operation.
The increasing number of software components and the diverse hardware platforms used across different vehicle models further complicate the update process. Developers must address compatibility issues, potential conflicts between different software versions, and the need for rigorous testing across a wide range of conditions and configurations to ensure seamless integration and avoid unforeseen issues.
Ensuring Compatibility Across Diverse Systems
Modern vehicles often employ a diverse range of hardware and software systems, including various sensors, actuators, communication protocols, and embedded systems. Achieving compatibility across these diverse components during software updates and patch deployments is critical. Failing to address potential conflicts can lead to malfunctions, system instability, and security breaches.
The need for compatibility extends beyond the vehicle itself. Integration with external systems, such as cloud platforms and diagnostic tools, must also be considered during the update process. Maintaining seamless communication and data exchange between the vehicle and these external systems is essential for maintaining functionality and preventing security vulnerabilities.
Managing Update Rollout and Deployment
Rolling out software updates and patches to a large fleet of vehicles requires careful planning and execution. This includes developing a phased approach to deployment, prioritizing updates based on criticality, and establishing effective monitoring mechanisms to track the progress and identify potential issues during the process. Managing the rollout efficiently is vital for minimizing disruption to vehicle operations and ensuring a smooth transition to the updated software.
Minimizing Downtime During Updates
Minimizing downtime during software updates is a key consideration for automotive IoT systems. Strategies for minimizing downtime during updates include employing incremental updates, implementing rollback procedures, and developing robust testing environments. Carefully planned update schedules and strategies can significantly reduce the impact of updates on vehicle operation, ensuring minimal disruption to the user experience.
Maintaining Security Throughout the Update Process
Security must be a paramount concern throughout the entire software update and patch process. This includes employing secure update channels, implementing robust authentication and authorization mechanisms, and conducting rigorous security testing to identify and address potential vulnerabilities. Maintaining a high level of security during updates is critical for preventing unauthorized access and exploitation of vulnerabilities.
Addressing the Human Factor in Updates
The human element plays a crucial role in the success of software updates and patches. Training technicians and mechanics on the proper procedures for updating vehicle software and handling potential issues is essential. Effective communication and documentation are also critical to ensure that all stakeholders understand the update process and potential impacts. Addressing the human factor in the update process is vital for minimizing errors and ensuring a smooth transition.
The Importance of Continuous Monitoring and Evaluation
Post-deployment monitoring and evaluation are essential for identifying and addressing any lingering issues or vulnerabilities introduced during software updates and patches. This includes tracking system performance, collecting feedback from drivers and technicians, and proactively identifying and rectifying any problems that arise. Continuous monitoring and evaluation are essential for maintaining the security and reliability of automotive IoT systems over time.