Defining Recovery Point Objective (RPO)

Understanding the Concept
A Recovery Point Objective (RPO) is a critical component of business continuity and disaster recovery planning. It essentially defines the maximum acceptable period of time that a business can afford to be without access to its critical data or systems. This timeframe represents the maximum tolerable downtime before significant business disruption occurs, impacting revenue, reputation, and operational efficiency. Understanding the RPO is crucial for organizations to develop effective data backup and recovery strategies.
Defining this objective requires a deep understanding of the business's operational needs and tolerance for data loss. The RPO is often tied to the criticality of the data, the cost of downtime, and the potential impact on customer satisfaction and revenue generation.
Factors Influencing RPO
Several factors influence the establishment of a suitable RPO. These include the cost of downtime, the potential for revenue loss, the impact on customer satisfaction, and the criticality of the data or system. For example, a company with a high-volume e-commerce website may have a lower RPO than a financial institution that needs to maintain continuous operation to prevent fraud and ensure regulatory compliance. Data criticality plays a major role in determining the acceptable timeframe for data loss.
Setting Realistic RPO Values
Determining a realistic RPO value necessitates thorough analysis of the business's operations and risk tolerance. A company should assess the potential financial impact of downtime, such as lost sales, customer dissatisfaction, and operational inefficiencies. This analysis helps in setting an RPO that aligns with the business's tolerance for data loss and potential disruption.
Relationship with Recovery Time Objective
The Recovery Point Objective (RPO) is closely linked to the Recovery Time Objective (RTO). While the RPO focuses on the acceptable amount of data loss, the RTO defines the maximum acceptable time to restore operations after a disruption. Establishing a clear relationship between the two objectives ensures a comprehensive disaster recovery strategy. For example, a lower RPO might necessitate a faster RTO to minimize data loss and maintain business continuity.
Implementing RPO in Practice
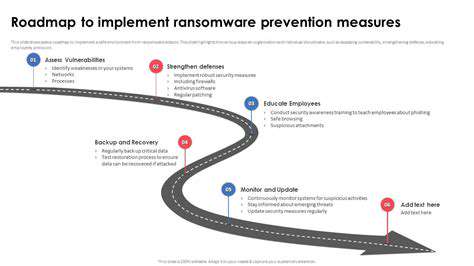
Implementing an RPO involves several practical steps, including data backup and recovery procedures. A robust data backup strategy is essential to meet the RPO. This includes frequent backups, secure storage locations, and verified data restoration processes. Organizations should regularly test their backup and recovery procedures to ensure they can meet their defined RPO. This includes simulating disaster scenarios to evaluate the efficiency and effectiveness of the recovery plan.
RTO and RPO in Ransomware Recovery Strategies
Understanding RTO and RPO
Ransomware attacks can cripple businesses, leading to significant disruptions in operations and financial losses. A crucial aspect of a robust ransomware recovery strategy is the establishment of clear Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO). These objectives define the acceptable timeframe for restoring critical systems and data after an attack, and the maximum data loss that the organization can tolerate.
Effectively defining RTO and RPO allows businesses to prioritize recovery efforts and allocate resources strategically. The process involves careful consideration of the organization's specific needs and potential impact of downtime, ensuring that recovery plans are aligned with business continuity goals.
Defining Recovery Time Objective (RTO)
The Recovery Time Objective (RTO) is the maximum acceptable time to restore critical systems and applications to a fully operational state after a ransomware attack. This timeframe is crucial for minimizing the negative consequences of downtime, including lost revenue, damaged reputation, and disruption of essential services. A shorter RTO generally indicates a higher level of business resilience and a greater emphasis on rapid recovery.
Factors influencing RTO determination include the criticality of the affected systems, the complexity of the recovery process, and the availability of recovery resources. Organizations need to meticulously evaluate these factors to establish a realistic and achievable RTO.
Determining Recovery Point Objective (RPO)
The Recovery Point Objective (RPO) defines the maximum acceptable amount of data loss that an organization is willing to tolerate after a ransomware attack. It represents the point in time from which data can be recovered. A lower RPO indicates a higher level of data protection and a commitment to minimizing data loss.
RPO calculations often consider factors like data frequency, the value of the data, and the potential impact of data loss on business operations. Organizations must carefully weigh the balance between data protection and the speed of recovery to achieve an appropriate RPO.
Establishing Realistic RTO and RPO Values
Setting RTO and RPO values requires a deep understanding of the organization's operational requirements. These values should be based on realistic assessments of the potential impact of downtime and data loss. Too aggressive targets can result in unrealistic recovery plans, while overly conservative targets might not adequately address the business needs.
A thorough risk assessment, considering potential threats and vulnerabilities, is crucial for establishing suitable RTO and RPO values. Regular review and updates of these values are essential to reflect changes in business operations and technological advancements.
Implementing Recovery Strategies Aligned with RTO and RPO
Once RTO and RPO values are established, organizations must develop and implement recovery strategies that align with these objectives. This involves creating detailed recovery plans, regularly testing recovery procedures, and ensuring the availability of necessary resources.
Key components of effective recovery strategies include data backups, disaster recovery plans, and redundant systems. These elements are crucial for ensuring that recovery operations can be executed efficiently and effectively in the event of a ransomware attack.
Testing and Validation of Recovery Procedures
Testing and validating recovery procedures are essential to ensure that the established RTO and RPO values are achievable. Regular testing exercises allow organizations to identify weaknesses in their recovery plans and make necessary adjustments.
These tests should simulate real-world ransomware scenarios to evaluate the effectiveness of recovery processes. Thorough post-test analysis helps organizations identify areas for improvement and fine-tune their recovery strategies for optimal performance.
Monitoring and Maintaining RTO and RPO
RTO and RPO values are not static; they require continuous monitoring and adjustments to remain relevant and effective. Regular reviews of the established values should be conducted to ensure that they continue to align with the organization's evolving needs and operational environment.
Monitoring the performance of recovery procedures and identifying potential risks help organizations proactively address issues and maintain the desired levels of resilience. Adapting to changing technologies and threats is crucial to ensure that RTO and RPO remain effective safeguards against ransomware attacks.
Practical Considerations for Establishing RTO and RPO Values
Defining Realistic Recovery Time Objectives (RTOs)
Establishing Recovery Time Objectives (RTOs) requires a deep understanding of the business impact of downtime. RTOs represent the maximum acceptable time a system or service can be unavailable after a disruptive event, such as a ransomware attack. A realistic RTO considers the criticality of the affected systems and the potential financial and reputational damage associated with prolonged outages. This process necessitates careful consideration of the operational workflows and dependencies, ensuring that the recovery process is efficient and aligned with the specific needs of the organization. Understanding the cascading effects of a prolonged outage is crucial for accurate RTO definition. For example, if a production line relies on a specific database, a significant delay in restoring the database would have direct implications on the entire production schedule.
Furthermore, the RTO should be achievable by the recovery plan. A highly ambitious RTO, while desirable, may not be attainable with the available resources and technology. A practical approach involves evaluating the current infrastructure, staffing levels, and existing recovery procedures. The goal is to define an RTO that is realistic and achievable while still minimizing the negative impact on business operations. Detailed documentation and clear communication are vital for effective RTO planning, allowing for seamless execution of the recovery process.
Determining Appropriate Recovery Point Objectives (RPOs)
Recovery Point Objectives (RPOs) define the maximum acceptable data loss after a disruptive event. RPOs are crucial for data integrity and operational continuity in the aftermath of a ransomware attack. A low RPO necessitates a more frequent backup schedule and robust data protection strategies. Balancing the need for minimal data loss with the practical constraints of backup frequency is essential. This involves evaluating the sensitivity of the data and the potential impact of data loss on ongoing operations. For instance, if a company handles sensitive customer data, a higher level of data protection is required, leading to a stricter RPO definition.
Practical considerations in defining RPOs include the cost of data recovery and the cost of downtime. The frequency of backups, the storage capacity, and the complexity of the recovery process all play a role in determining a suitable RPO. It's also important to consider the potential for data corruption or loss during the recovery process. A thorough evaluation of these factors allows for the establishment of a realistic RPO that balances data integrity with operational feasibility. By accurately assessing the value of data and the operational implications of data loss, organizations can establish appropriate and achievable RPOs.