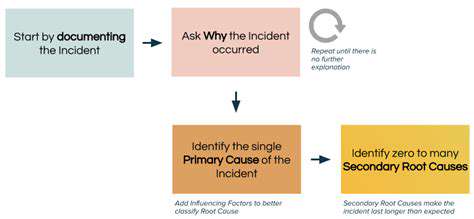
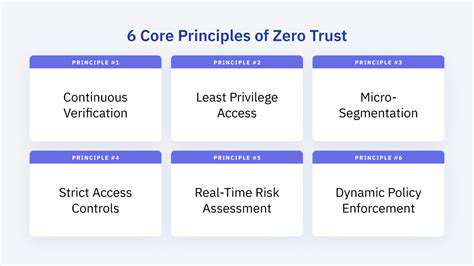
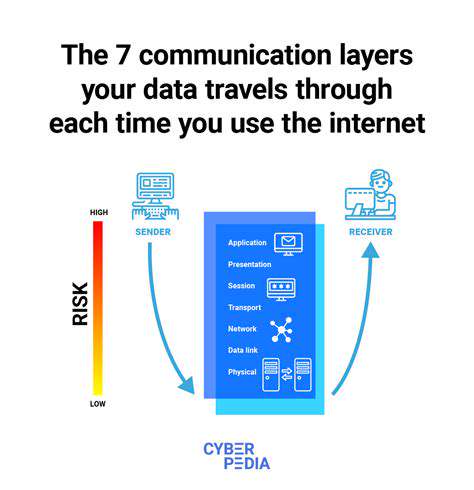
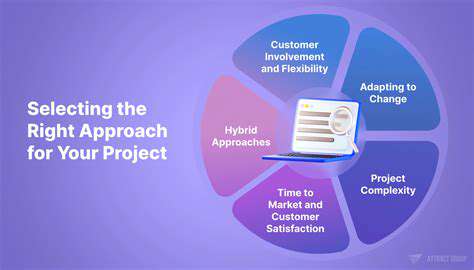
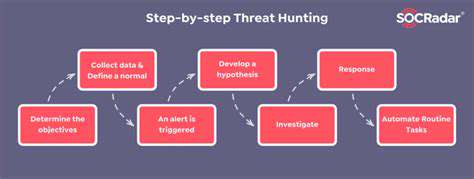
Understanding the Double Extortion Tactic
The Double Extortion era of ransomware represents a significant escalation in cybercriminal tactics. Beyond encrypting data, these sophisticated attacks now threaten to leak sensitive information if the victim doesn't pay. This dual threat leverages the fear of public exposure and reputational damage, often targeting organizations with valuable or sensitive data. This tactic significantly increases the pressure on victims to comply, making it a more effective and lucrative strategy for attackers.
The Rise of Data Leak Sites
A key component of double extortion is the creation and maintenance of dedicated leak sites. These sites, often hosted on the dark web, serve as a public repository for stolen data. The threat of data exposure on these sites is a powerful motivator for victims to pay the ransom, as the potential consequences of public disclosure can be devastating, impacting everything from financial stability to customer trust and legal liabilities. The existence of these sites demonstrates a calculated and organized approach to the attacks.
Motivations Behind the Escalation
The shift to double extortion tactics reflects the evolving motivations of ransomware attackers. Beyond financial gain, the potential for reputational damage and the exploitation of data vulnerabilities provides a stronger incentive. Attackers are increasingly focused on maximizing their financial returns by leveraging the fear of exposure and compliance pressure. This shift also signals a greater sophistication in the targeting and execution of these attacks.
Impact on Victims and Businesses
Double extortion ransomware attacks have a profound and multifaceted impact on victims. Beyond the financial costs of the ransom and recovery efforts, businesses face substantial reputational damage and potential legal ramifications if the leaked data compromises sensitive customer information. The disruption to operations, the need for extensive data recovery, and the long-term implications on business continuity are all serious concerns. The potential for significant financial and operational losses underscores the need for robust cybersecurity measures.
The Role of Threat Intelligence
Effective threat intelligence is crucial in combating the double extortion era of ransomware. Monitoring and analyzing emerging attack patterns, identifying leak sites, and understanding the motivations of attackers are all key aspects of developing a comprehensive defense strategy. This includes staying informed about the latest techniques and tactics used by cybercriminals to proactively identify and mitigate the risks associated with these attacks. Early detection is critical to minimizing damage.
Security Measures and Mitigation Strategies
Organizations must implement robust cybersecurity measures to mitigate the risks of double extortion attacks. These measures include strong data encryption, robust access controls, regular security audits, and employee training programs to raise awareness of phishing attempts and other attack vectors. Implementing multi-layered security systems can significantly reduce the likelihood of successful attacks. Furthermore, robust incident response plans are essential to minimize the impact of an attack if one occurs.
Conti: A Case Study in Ransomware as a Service (RaaS)

Understanding the Conti Ransomware Threat
The Conti ransomware group, a notorious cybercriminal organization, has been active since 2018, causing significant disruptions to businesses and governments worldwide. Their tactics involve encrypting sensitive data and demanding payment in cryptocurrency to restore access. This highly sophisticated operation leverages advanced techniques, including exploiting vulnerabilities in software systems, to penetrate networks. Conti's infrastructure is structured to ensure their operation's longevity and resilience.
This ransomware group has a well-defined structure, allowing them to effectively carry out their malicious activities. They often employ sophisticated tools and techniques to avoid detection and maintain their anonymity. Understanding their methods is crucial for organizations to bolster their cybersecurity posture and mitigate the risk of such attacks. Conti's reach extends to various sectors, including healthcare, finance, and government, highlighting the broad impact of this threat.
The Impact of the Conti Ransomware Attack
The repercussions of a Conti ransomware attack can be devastating for affected organizations. Beyond the immediate financial cost of the ransom demand, there are significant long-term consequences, such as operational downtime, reputational damage, and legal liabilities. Data breaches can expose sensitive information, leading to regulatory fines and potential legal actions.
Furthermore, the disruption to business operations can cripple productivity and cause significant financial losses. The recovery process itself can be lengthy and complex, requiring substantial resources and expertise. The impact can ripple through supply chains, affecting multiple organizations and individuals.
Mitigation Strategies and Prevention
Preventing a Conti ransomware attack requires a multi-layered approach. Regular software updates are crucial to patch known vulnerabilities, which are frequently exploited by ransomware groups. Implementing strong access controls, including multi-factor authentication, will limit unauthorized access to sensitive data.
Regular data backups are essential to ensure business continuity in the event of an attack. These backups should be stored offline to prevent ransomware from encrypting them. Employee training on cybersecurity best practices, including recognizing phishing emails and suspicious links, is vital to prevent human error, which often plays a significant role in attacks.
Robust security measures, including intrusion detection and prevention systems, can help detect and respond to threats in real-time. Collaboration with cybersecurity experts and law enforcement is crucial for investigating and mitigating the impact of an attack. Establishing incident response plans will help organizations effectively manage and recover from a ransomware attack.
Securing representative samples from Mars presents significant logistical hurdles. The Martian surface environment, with its diverse geological formations and potential for hidden or dispersed samples, necessitates a nuanced approach. Understanding the spatial distribution of scientifically valuable materials is crucial for optimizing collection strategies, ensuring that the samples obtained are truly representative of the planet's geological history and potentially past habitability. This requires careful planning and consideration of the various geological contexts across the target area.
The Future of Ransomware: Adaptation and Innovation
Ransomware's Evolving Tactics
Ransomware attacks are no longer confined to simple encryption of files. Modern attackers are increasingly sophisticated, employing a blend of techniques to maximize their impact and profitability. This includes not just encrypting data, but also exfiltrating sensitive information for double extortion, threatening to leak or sell compromised data if a ransom isn't paid. This escalation in tactics necessitates a shift in defensive strategies, moving beyond basic backups to encompass robust security protocols and incident response plans.
Furthermore, the rise of ransomware-as-a-service (RaaS) models has democratized access to these attacks. This means that even individuals or smaller groups can launch sophisticated campaigns, making the threat landscape more diffuse and challenging to track. The anonymity provided by the dark web and cryptocurrencies further complicates law enforcement efforts to apprehend perpetrators.
Adapting to the Shadow IT Landscape
The proliferation of Shadow IT, where employees use unauthorized software and cloud services, presents a significant vulnerability to ransomware attacks. This hidden technology often lacks robust security measures, creating a backdoor for malicious actors to gain entry into the organization's network. Businesses must actively address the challenges posed by Shadow IT, implementing policies that encourage transparency and control of IT usage while simultaneously educating employees about the risks.
Moreover, the increasing reliance on remote work and cloud-based applications has expanded the attack surface. Attackers are exploiting vulnerabilities in these remote access points and cloud environments to gain initial access to networks. Organizations need to strengthen their remote access security, implementing multi-factor authentication, robust VPNs, and regular security audits of cloud services.
Innovation in Detection and Response
Staying ahead of the curve in the ransomware game requires a proactive approach to detection and response. Advanced threat detection systems, capable of identifying subtle anomalies and malicious patterns, are becoming increasingly crucial. This includes employing machine learning algorithms to analyze network traffic and identify potential threats before they escalate into full-blown attacks. The development and deployment of proactive security measures, such as intrusion detection systems and advanced endpoint protection, are essential components of a robust defense strategy.
Furthermore, the development of innovative response strategies is vital. This involves not just restoring data from backups, but also identifying the root cause of the attack and implementing measures to prevent similar incidents in the future. Collaboration between security teams and incident response experts is paramount in effectively mitigating the damage and minimizing the long-term impact of a ransomware attack.
Beyond the Ransom: The Wider Implications of Cyberattacks

Beyond the Ransom: The Wider Implications of Ransomware Attacks
Ransomware attacks are more than just a digital extortion tactic; they represent a multifaceted threat with far-reaching consequences. These attacks can cripple critical infrastructure, disrupt essential services, and cause significant financial and reputational damage to individuals and organizations alike. Understanding the broader implications is crucial for effective mitigation and response.
Financial Losses and Economic Disruption
The immediate financial impact of a ransomware attack can be devastating. Organizations often pay the ransom, but the costs extend far beyond the payment itself. Significant downtime can lead to lost productivity and revenue, impacting the entire supply chain. Furthermore, the cost of recovery, including data restoration, system remediation, and legal fees, can be substantial.
Operational Disruption and Service Impacts
Ransomware attacks can disrupt operational processes, impacting critical services. Hospitals may struggle to access patient data, leading to delays in treatment and potentially life-threatening consequences. Businesses may face delays in production, impacting their ability to meet customer demands and potentially leading to supply chain issues.
Reputational Damage and Loss of Trust
The reputational damage associated with a ransomware attack can be severe. Customers and stakeholders may lose trust in the affected organization, leading to a decline in brand loyalty and potential legal repercussions. The perception of vulnerability can erode public confidence and damage long-term relationships.
Cybersecurity Vulnerabilities and Increased Risks
Ransomware incidents often expose underlying cybersecurity vulnerabilities within an organization. These vulnerabilities can make the organization more susceptible to future attacks. Addressing these vulnerabilities is crucial to preventing similar incidents from occurring in the future, as well as implementing robust and proactive security measures.
Legal and Regulatory Implications
Ransomware attacks frequently trigger legal and regulatory implications. Organizations must comply with data privacy regulations, such as GDPR or CCPA, to protect sensitive data. Failing to do so can result in substantial penalties. Furthermore, legal battles over ransom payments and data recovery can be complex and costly.
Social and Ethical Considerations
Beyond the technical and financial aspects, ransomware attacks raise significant social and ethical concerns. The attacks can disproportionately affect vulnerable populations and communities, and the ethical implications of paying ransoms are debated extensively. These considerations require a multifaceted approach to combatting the wider societal impact of these attacks, including advocating for stronger regulations and promoting cybersecurity awareness.