Defining Zero Trust: A Foundation for Modern Security
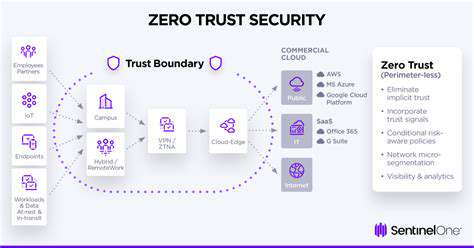
Zero Trust security is a paradigm shift from traditional network security models. Instead of relying on implicit trust within a network perimeter, zero trust assumes no implicit trust for any user, device, or application, regardless of its location. This fundamental shift necessitates a comprehensive approach to verifying and authorizing access to resources, regardless of whether the access originates inside or outside the network.
This approach prioritizes continuous authentication and authorization, demanding strong verification measures for every access request. This proactive verification process significantly reduces the attack surface by limiting the potential damage from compromised accounts or devices.
Key Principles of Zero Trust
A Zero Trust security model is built on several key principles. These include the principle of least privilege, which dictates that users and devices should only be granted access to the resources they absolutely need to perform their tasks. This principle is crucial for minimizing the impact of a security breach.
Furthermore, these models emphasize the importance of continuous monitoring and threat detection. Regular analysis of user and device behavior, coupled with advanced threat intelligence, is critical for proactively identifying and responding to emerging threats.
Zero Trust and the Modern Enterprise
The modern enterprise environment is characterized by increased complexity, with employees working remotely and utilizing a diverse range of devices and applications. This complexity significantly expands the attack surface, making traditional security approaches increasingly ineffective. Zero Trust architecture effectively addresses these challenges by providing a comprehensive security framework that adapts to these evolving dynamics.
Implementing a Zero Trust strategy enables organizations to better manage and secure their expanding digital footprint. This is particularly important for enterprises that operate across multiple geographies, with employees working from various locations and utilizing diverse devices.
Implementing Zero Trust: Practical Considerations
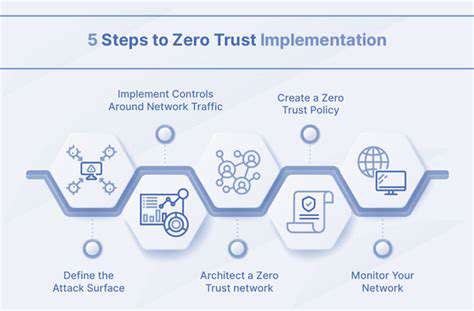
Implementing a Zero Trust architecture requires careful planning and execution. Organizations must assess their current security posture, identify their critical assets, and develop a robust access control strategy. This strategy needs to incorporate multi-factor authentication, granular access controls, and real-time threat detection and response capabilities.
A crucial consideration is the integration of existing systems and technologies with the new Zero Trust framework. This requires a phased approach that allows for incremental adoption and avoids disruption to business operations.
The Role of Identity and Access Management (IAM)
Identity and Access Management (IAM) plays a critical role in Zero Trust security. A strong IAM system is essential for verifying user identities, managing access privileges, and enforcing access policies. It ensures that only authorized users have access to the resources they need.
Effective IAM solutions are critical for maintaining the security posture. They are integral to the overall Zero Trust approach, facilitating a robust and adaptable security architecture.
Benefits of Zero Trust Security
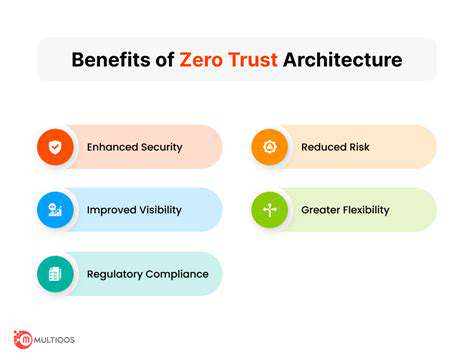
Implementing a Zero Trust security model offers numerous benefits, such as enhanced security posture, reduced risk of data breaches, and improved compliance with security regulations. This approach also provides increased visibility and control over network access, which can significantly improve the overall efficiency of operations.
By shifting to a Zero Trust model, organizations can effectively safeguard their sensitive data and resources, minimizing the impact of potential threats. The comprehensive approach to authentication and authorization offered by Zero Trust makes it a robust and adaptable solution for the modern digital landscape.
Implementing Zero Trust: Key Considerations
Implementing Zero Trust: A Comprehensive Approach
Zero Trust security is a crucial aspect of modern cybersecurity, requiring a fundamental shift in how organizations approach network access. It's not just about technology; it's about a mindset that demands continuous verification and validation of every user and device attempting to access sensitive data and resources. This meticulous approach is essential to protect against sophisticated attacks that exploit vulnerabilities in traditional network models.
Implementing Zero Trust demands a strong understanding of your organization's unique security needs and a willingness to adapt to evolving threats. This requires a proactive, rather than reactive, approach to security, constantly monitoring and adjusting your security posture to stay ahead of emerging threats.
Defining the Zero Trust Perimeter
Traditional network security often relies on a perimeter-based approach, assuming that anything inside the firewall is safe. Zero Trust fundamentally disrupts this model, recognizing that no user or device should be implicitly trusted. Instead, the network is treated as inherently untrusted, requiring constant verification for all access requests.
Micro-segmentation and Access Control
Micro-segmentation is a key component of Zero Trust, dividing the network into smaller, isolated segments. This limits the impact of a potential breach, containing the damage and preventing the spread of malware. Implementing granular access controls based on user roles and device identities further enhances security.
By implementing micro-segmentation, organizations can isolate sensitive data and applications, minimizing the potential damage from a security incident and improving overall security posture.
Identity and Access Management (IAM)
Robust Identity and Access Management (IAM) systems are critical in a Zero Trust environment. They are essential for verifying user identities, managing access privileges, and enforcing policies. A strong IAM system helps to ensure that only authorized users and devices can access specific resources, significantly reducing the risk of unauthorized access.
Zero Trust security requires a deep understanding of who your users are and what access they need. This detailed knowledge and control directly correlate to a more secure and resilient network.
Continuous Monitoring and Threat Detection
Zero Trust is not a one-time implementation; it requires continuous monitoring and adaptation. Implementing advanced threat detection systems is crucial to identify and respond to malicious activities in real time. Proactive monitoring ensures that security measures remain effective against evolving threats.
Continuous monitoring and threat detection are essential for identifying and responding to potential security breaches, keeping your organization's data and systems secure against emerging threats.
Security Posture Assessment and Planning
Before embarking on a Zero Trust implementation, a thorough security posture assessment is paramount. This process involves evaluating existing security infrastructure, identifying vulnerabilities, and defining clear goals. Careful planning and prioritization are crucial to ensure a smooth and successful transition to a Zero Trust model.
The Human Element in Zero Trust
Zero Trust security is not just about technology; it's also about people. Training users on security best practices, raising awareness about potential threats, and fostering a security-conscious culture are crucial for success. By empowering users with the knowledge and tools to identify and report suspicious activities, organizations can significantly enhance their security posture.
Ultimately, human involvement in security protocols is critical for successful Zero Trust implementation. Educating employees about cybersecurity best practices and the importance of adhering to security policies is vital for maintaining a strong security posture.
Building a Zero Trust Network: Practical Strategies
Understanding the Zero Trust Model
The zero trust model fundamentally shifts the traditional network security approach. Instead of relying on implicit trust within a network perimeter, zero trust assumes no implicit trust for any user, device, or application, regardless of their location or access level. This rigorous approach mandates continuous verification and authorization for every access attempt, even from trusted internal sources. Implementing zero trust requires a shift in mindset, moving from a perimeter-based security strategy to a continuous verification and validation model. This means scrutinizing every interaction and validating identity, access, and context before granting any access.
This paradigm shift is crucial in today's increasingly complex and dynamic threat landscape. A zero trust framework demands a comprehensive understanding of all users, devices, and applications within the network, enabling granular control over access privileges and mitigating the risk of unauthorized access even if an attacker gains a foothold within the network.
Implementing Granular Access Control
A cornerstone of zero trust is granular access control. This involves meticulously defining and restricting access rights to specific resources based on the principle of least privilege. Admins should implement a system that prevents users from accessing resources they do not need, even if they have existing privileges. This proactive approach significantly reduces the potential impact of a breach by limiting the scope of compromised access.
Implementing granular access control requires careful planning and meticulous documentation. Defining the required access rights for each user, role, and application is paramount to ensure that only authorized users have access to the required resources. This strategy is essential to limit the potential damage caused by unauthorized access.
Leveraging Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) plays a critical role in strengthening the zero trust security posture. MFA adds an extra layer of security beyond just usernames and passwords by requiring users to provide multiple forms of verification, such as a one-time code sent to a mobile device or a biometric scan. This significantly reduces the risk of unauthorized access even if passwords are compromised.
Choosing the right MFA methods is critical. Consider factors such as user experience, cost, and security requirements when evaluating different options. Implementing a robust MFA system across all user accounts is a fundamental step in a zero trust architecture.
Employing Network Segmentation
Network segmentation is another essential component of a zero trust strategy. By dividing the network into smaller, isolated segments, organizations can limit the impact of a breach by containing the damage to a specific segment. This isolation significantly reduces the attack surface and prevents lateral movement within the network.
Careful planning is crucial for effective network segmentation. Consider factors such as application dependencies, user access patterns, and security requirements when designing the segmentation strategy. Comprehensive segmentation is key to containing any potential breach and reducing the potential impact.
Monitoring and Auditing Access Activities
Continuous monitoring and auditing of access activities are vital for maintaining a secure zero trust environment. Implementing robust logging and monitoring mechanisms ensures the detection of suspicious activity, providing valuable insights for threat detection and response. This proactive approach enables the early identification of potential breaches and allows for timely remediation.
Regularly reviewing audit logs for anomalies and patterns can help organizations proactively identify and address security vulnerabilities. This continuous monitoring ensures that security measures are effective and adaptable to evolving threats.
Enforcing Continuous Security Posture Assessments
Regular security posture assessments are essential for ensuring that the zero trust implementation remains effective and aligned with evolving threats. These assessments should encompass the entire network, including user access controls, network segmentation, and security tools. By periodically evaluating the zero trust posture, organizations can identify weaknesses and implement necessary adjustments.
This proactive approach enables organizations to adapt their security strategies to emerging threats and maintain a strong security posture. Ongoing security posture assessments are crucial in ensuring that the zero trust framework remains effective in the ever-changing security landscape.
Addressing the Challenges of Zero Trust Implementation

Zero-Waste Living: A Growing Movement
The zero-waste movement is gaining significant traction globally, as more and more individuals and communities strive to minimize their environmental footprint. This shift towards conscious consumption and waste reduction reflects a growing awareness of the detrimental effects of traditional waste management practices on the planet's ecosystems.
This commitment to reducing waste often begins with small, everyday changes, like using reusable bags, water bottles, and food containers. These seemingly simple actions collectively contribute to a more sustainable lifestyle.
The Economic Impact of Zero Waste
Implementing zero-waste practices can have both positive and potentially negative economic impacts. While there are initial costs associated with purchasing reusable items and potentially adjusting consumption patterns, the long-term financial benefits can be considerable. Reducing reliance on single-use products, for example, can save money in the long run.
The potential for significant cost savings is substantial, potentially leading to increased household budgets available for other expenditures. Additionally, supporting local businesses that prioritize sustainable practices can boost local economies.
The Social Aspect of Zero Waste
Zero-waste living often fosters a stronger sense of community and shared responsibility. People who embrace these practices often find themselves connecting with others who share similar values and engaging in collaborative efforts to reduce waste in their communities. This collective action can lead to a more sustainable and equitable future.
The social aspect is crucial for the movement's long-term success. Sharing tips, recipes, and resources within communities can reinforce the importance of zero-waste practices.
The Environmental Consequences of Waste
The environmental consequences of waste are undeniable and far-reaching. From overflowing landfills to the pollution of our oceans and waterways, the negative impacts of waste on our planet are significant and require urgent attention. This problem is significantly impacting wildlife and ecosystems.
Overcoming the Challenges of Zero Waste
Adopting zero-waste practices can present various challenges, including the initial investment in reusable products, the need for adjustments to existing routines, and the potential for social stigma or criticism. This is where community support and education play a crucial role.
Overcoming these hurdles requires conscious effort and a willingness to adapt. Learning new skills and adopting new habits can be challenging but ultimately rewarding.
The Role of Government and Businesses in Zero Waste
Governments and businesses play a critical role in fostering a zero-waste society. Implementing policies that incentivize the use of sustainable materials, reducing single-use plastics, and promoting recycling initiatives are all essential steps in this direction. The government's role is crucial in setting the tone for the entire nation.
The Future of Zero Waste
The zero-waste movement is constantly evolving, with new technologies and innovations emerging that make waste reduction easier and more effective. From advanced recycling methods to innovative design solutions, the future of zero-waste living looks promising. This is a testament to the continuing efforts to protect our planet.
With continued commitment and innovation, zero-waste living can become a reality for all. This movement is not about perfection but rather about continuous improvement and progress toward a more sustainable future.
Maintaining a Secure Zero Trust Posture: Ongoing Efforts
Defining Zero Trust
Zero Trust security is a security model that assumes no implicit trust, either for users or devices. This means that every user and device attempting to access resources within the network must be authenticated, authorized, and continuously validated, regardless of their location or prior access history. This contrasts sharply with traditional network security models that often rely on perimeter defenses and implicit trust, treating everything within the network as safe.
Implementing a Zero Trust architecture requires a shift in mindset, moving away from a trust but verify approach to a never trust, always verify approach. This involves a fundamental change in how organizations view and manage access to their resources.
Identifying and Verifying Users and Devices
A robust Zero Trust architecture starts with meticulous identification and verification of all users and devices seeking access to resources. This involves employing strong authentication methods, such as multi-factor authentication (MFA), to ensure that only authorized individuals and devices can gain entry. This proactive approach reduces the risk of unauthorized access significantly. Beyond initial authentication, ongoing verification is crucial to ensure that access privileges remain aligned with current needs and risk profiles.
Continuously Monitoring Access Activity
Implementing continuous monitoring of access activity is essential for maintaining a secure Zero Trust posture. Real-time monitoring tools provide insights into user and device behavior, allowing security teams to identify anomalies and potential threats in a timely manner. This proactive approach allows for rapid response to suspicious activity, minimizing the potential for breaches. Log analysis and security information and event management (SIEM) systems are crucial components of this continuous monitoring process.
Enforcing Least Privilege Access
The principle of least privilege is fundamental to Zero Trust. Users and devices should only be granted the minimum access rights necessary to perform their tasks. This drastically reduces the impact of a potential security breach, limiting the potential damage to compromised accounts or devices. Properly implementing least privilege access requires meticulous planning and ongoing review of user roles and permissions.
Segmenting Networks and Resources
Network segmentation plays a vital role in achieving a Zero Trust posture. By dividing the network into smaller, isolated segments, organizations can minimize the impact of a security incident. This isolates potential threats and limits their ability to spread throughout the network. Each segment should be carefully planned to ensure that only necessary communication paths are established between them.
Regular Security Assessments and Audits
Maintaining a secure Zero Trust posture requires ongoing security assessments and audits. Regular evaluations of the security posture can identify vulnerabilities and misconfigurations that could compromise the security. This includes evaluating the effectiveness of security controls, user access controls, and the overall architecture. Regular assessments and audits allow for proactive identification and remediation of issues before they can be exploited by attackers.
Employee Training and Awareness
A crucial component of maintaining a Zero Trust posture is educating employees about security best practices. Training programs should emphasize the importance of strong passwords, phishing awareness, and reporting suspicious activity. Employee awareness and adherence to security policies are essential for preventing human errors that could compromise the entire system. This training should be ongoing and regularly updated to keep pace with evolving threats.