
Featured
Jun 13, 2025
Zero Trust and Cloud Security Posture Management (CSPM): Comprehensive Cloud Defense
- Enhanced Security Posture: Minimizes vulnerabilities by enforcing strict access policies.- Improved Data Protection: Ensures sensitive information is accessible only to verified users and devices.- Greater Visibility and Control: Enables continuous monitoring and real-time threat detection.- Regulatory Compliance: Assists in meeting industry standards and data protection regulations. Implementing Zero Trust in Cloud SettingsSuccessful Zero Trust deployment involves several key steps:- Identity and Access Management (IAM): Implement robust authentication mechanisms like multi-factor authentication (MFA).- Device Security: Authenticate and verify devices before granting access.- Least Privilege Access: Limit user permissions to only what is necessary.- Micro-Segmentation: Divide cloud networks into smaller segments to contain potential breaches.- Continuous Monitoring: Use security analytics and threat detection tools to monitor activities constantly. ConclusionAdopting Zero Trust in cloud environments is no longer optional—it's a strategic necessity. By prioritizing verification over trust, organizations can safeguard their digital assets against evolving cyber threats. Embrace Zero Trust principles today to build a resilient, secure, and compliant cloud infrastructure that supports your business growth and innovation.---Interested in strengthening your cloud security with Zero Trust? Learn more about implementing effective Zero Trust strategies and safeguard your organization against modern cyber threats. Contact our security experts for tailored solutions that fit your specific cloud environment needs.

Featured
Jun 13, 2025
Ransomware and Data Exfiltration: Preventing Data Breach
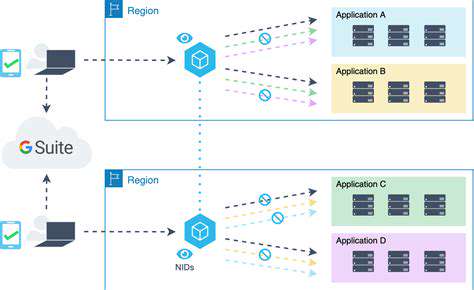
Discover the escalating dangers of ransomware and data exfiltration with our comprehensive overview. In today's digital landscape, cyber threats are more sophisticated and prevalent than ever, posing significant risks to organizations of all sizes. Our detailed article sheds light on the scope of these malicious activities, emphasizing the importance of proactive security measures to safeguard sensitive information.Learn about the rising threat of ransomware, a form of malicious software that encrypts an organization's data, demanding ransom payments for decryption keys. Understand how cybercriminals leverage ransomware to disrupt operations, cause financial losses, and tarnish reputations. Additionally, explore the increasing prevalence of data exfiltration — the clandestine theft of sensitive data meant to be kept confidential. These breaches often lead to severe consequences, including regulatory penalties and loss of customer trust.Our guide highlights the critical need for adopting Zero Trust principles and advanced encryption strategies for data both in transit and at rest. We emphasize the importance of implementing robust security frameworks, continuous monitoring, and employee awareness to prevent and mitigate these threats effectively.Whether you're an IT professional, business owner, or cybersecurity enthusiast, this article provides essential insights into the evolving landscape of cyber threats. Stay informed about the latest tactics used by cybercriminals and learn practical steps to enhance your organization's security posture.Protect your data, maintain your operational integrity, and stay ahead of cybercriminals by understanding the scope of ransomware and data exfiltration threats. Read our complete guide today for expert advice and actionable strategies to defend against these rising cyber threats.
Featured
Jun 13, 2025
Zero Trust Principles for Data Encryption in Transit and at Rest
Never trust, always verify. Unlike traditional security models that depend heavily on perimeter defenses such as firewalls, Zero Trust assumes that threats can exist both outside and inside your network. Therefore, it requires continuous validation of every user, device, and network request before granting access to resources.This approach minimizes the risk of data breaches by ensuring that no entity is automatically trusted, even if it is within the corporate network. Every access request undergoes strict identity verification, device health checks, and contextual analysis to determine its legitimacy. This continuous validation process helps organizations detect and respond to threats in real-time, significantly reducing the attack surface. Key Components of a Zero Trust Data Security FrameworkImplementing Zero Trust involves multiple layers of security controls, including robust identity management, least privilege access, and micro-segmentation of networks. Identity and access management (IAM) systems verify user identities through multi-factor authentication (MFA), ensuring that only authorized personnel can access sensitive data. Micro-segmentation divides the network into smaller zones, each protected individually, preventing lateral movement of attackers within the network. Additionally, real-time monitoring and analytics play a vital role in identifying suspicious activities and potential vulnerabilities. Benefits of Adopting Zero Trust SecurityBy embracing the Zero Trust model, organizations can achieve enhanced security and operational efficiency. It helps prevent data breaches, reduces insider threats, and ensures compliance with industry regulations. Moreover, Zero Trust supports remote work and cloud adoption by providing a flexible yet secure access framework tailored to modern digital environments. Why Your Organization Needs Zero Trust Data SecurityAs cyber threats evolve, traditional perimeter-based defenses are no longer sufficient. Zero Trust offers a proactive security posture that adapts to the complexities of today's digital landscape. Implementing this framework safeguards your critical assets, maintains customer trust, and aligns with best practices for cybersecurity resilience.---Secure your organization today with a comprehensive Zero Trust Data Security Framework. Learn how to build a resilient, adaptive security strategy that protects your data, users, and systems from evolving cyber threats. Contact our experts for tailored solutions and start your Zero Trust journey now.
Featured
Jun 13, 2025
AI and Behavioral Analytics: Uncovering Anomalous Activity
AI and Behavioral Analytics: Uncovering Anomalous Activity
Featured
Jun 13, 2025
Cyber Resilience in the Supply Chain: Preparing for Disruptions
Cyber Resilience in the Supply Chain: Preparing for Disruptions
Featured
Jun 12, 2025
Medical Device Security: Safeguarding Connected Healthcare Technology
Medical Device Security: Safeguarding Connected Healthcare Technology
Featured
Jun 12, 2025
Ransomware Resilience: Building an Adaptive and Proactive Security Strategy
Ransomware Resilience: Building an Adaptive and Proactive Security Strategy
Featured
Jun 12, 2025
Zero Trust Principles for Government Agencies
Zero Trust Principles for Government Agencies
Featured
Jun 12, 2025
Medical Device Security: Protecting Connected Healthcare Equipment
Medical Device Security: Protecting Connected Healthcare Equipment
Featured
Jun 12, 2025
Third Party Access Control in Supply Chain Security: Limiting Exposure
Third Party Access Control in Supply Chain Security: Limiting Exposure
Featured
Jun 12, 2025
AI for Security Posture Management: Continuous Improvement and Optimization
AI for Security Posture Management: Continuous Improvement and Optimization
Featured
Jun 12, 2025
Zero Trust for Cloud Native Applications
Zero Trust for Cloud Native Applications
Featured
Jun 12, 2025
AI for Threat Hunting: Empowering Cybersecurity Analysts
AI for Threat Hunting: Empowering Cybersecurity Analysts
Featured
Jun 12, 2025
Defending Your Supply Chain: Proactive Cybersecurity Strategies
Defending Your Supply Chain: Proactive Cybersecurity Strategies
Featured
Jun 12, 2025
Zero Trust Principles for Database Security
Zero Trust Principles for Database Security
Featured
Jun 12, 2025
AI for Security Awareness Training: Personalized Learning
AI for Security Awareness Training: Personalized Learning
Featured
Jun 12, 2025
Zero Trust for Government Agencies: Securing Public Sector Data
Zero Trust for Government Agencies: Securing Public Sector Data
Featured
Jun 12, 2025
Smart City Surveillance: Balancing Security and Privacy
Smart City Surveillance: Balancing Security and Privacy
Featured
Jun 12, 2025
Zero Trust in the Cloud: Securing Your Cloud Environment
Zero Trust in the Cloud: Securing Your Cloud Environment
Featured
Jun 12, 2025
Zero Trust and Micro Segmentation: Granular Network Control
Zero Trust and Micro Segmentation: Granular Network Control



















