Adopting Zero Trust means embracing a holistic approach that emphasizes rigorous access controls, continuous monitoring, and precise data segmentation. These measures ensure data protection regardless of access origin, making security practices compatible with modern cloud infrastructures and remote work scenarios.
The Importance of Data-Centric Security in Zero Trust Models
A pivotal element of Zero Trust is its focus on data-centric security, where safeguarding the data itself takes precedence. This involves encrypting data both at rest and during transmission, enforcing strict access policies, and deploying advanced techniques to prevent data loss.
By prioritizing data-centric security, organizations gain better oversight over who accesses critical information, can monitor usage patterns, and block unauthorized disclosures. This strategy ensures that even if other defenses fail, the data remains secure and inaccessible without proper authorization.
Implementing Micro-Segmentation for Enhanced Data Protection
Micro-segmentation divides networks into smaller, isolated sections, each with tailored security measures. This approach restricts lateral movement within the network, complicating attackers' efforts to reach vital data even if they breach one segment.
In a Zero Trust setup, micro-segmentation allows organizations to apply detailed access policies specific to certain data sets or applications. This minimizes the attack surface and guarantees access only to verified users and devices, substantially improving data security.
Role of Identity and Access Management (IAM) in Zero Trust
IAM systems are essential to Zero Trust, offering robust tools for verifying identities and enforcing access rules. Multi-factor authentication, single sign-on, and adaptive access controls are key features of effective IAM.
By continuously evaluating user roles, device status, and contextual factors, IAM ensures that only legitimate users with appropriate permissions can access sensitive data. This dynamic method reduces risks tied to stolen credentials or unauthorized access attempts.
Utilizing Advanced Monitoring and Analytics for Ongoing Security
Continuous monitoring and real-time analytics are crucial in Zero Trust to quickly identify and address suspicious activities. Deploying sophisticated SIEM systems enables organizations to analyze access patterns and spot irregularities.
This proactive stance allows security teams to react swiftly to threats, mitigate breaches, and refine policies. The objective is to maintain a flexible security posture that adapts to new threats and organizational changes.
Core Principles of Zero Trust Data Encryption
1. Strict Identity Verification for All Access Requests
In Zero Trust, every data access request must pass rigorous identity checks, whether the user is inside or outside the network. This typically involves multi-factor authentication, biometric verification, and contextual analysis like device health and location. The aim is to ensure only authenticated, authorized individuals access sensitive data, reducing risks of credential theft or impersonation.
2. Least Privilege Access Model
The least privilege principle grants users only the permissions needed for their tasks. In data Encryption, this limits exposure by ensuring only authorized personnel or systems can decrypt data. Regular audits and dynamic controls adjust permissions based on role changes and threat landscapes.
This method shrinks the attack surface, blocks lateral movement, and limits damage from compromised credentials. It also aids compliance with data protection regulations by controlling decryption access.
3. Continuous Monitoring and Real-Time Threat Detection
Zero Trust data encryption depends on constant monitoring of data access and usage. Advanced analytics and machine learning detect anomalies like unusual access times, atypical data volumes, or suspicious behavior, enabling immediate responses such as access revocation or extra authentication.
Real-time threat detection protects encrypted data and offers insights into evolving attack methods, keeping encryption strategies robust against new threats.
4. Micro-Segmentation of Data Environments
Micro-segmentation splits data environments into isolated sections, each with unique encryption controls. This confines attackers to one segment, preventing lateral movement. It also allows tailored encryption policies for different data types or user groups.
Segmentation tightens security policies, lowers compliance risks, and improves data governance. Independent key management per segment further strengthens security.
5. Dynamic Encryption Key Management
Strong key management is vital for Zero Trust data encryption. Dynamic key management involves regular key rotation, automated lifecycle processes, and secure storage via hardware security modules (HSMs). This limits key exposure and ensures compromised keys have limited usefulness.
Automating key renewal and revocation lets organizations respond quickly to incidents, maintaining encrypted data integrity and confidentiality.
6. Zero Trust Architecture Integration
Integrating data encryption into a Zero Trust architecture requires seamless coordination between network security, identity management, and data protection. Encryption policies should span all infrastructure layers, including cloud, on-premises servers, and endpoints. This ensures data stays encrypted at rest, in transit, and during processing.
Adopting Zero Trust architecture fosters security awareness, making encryption part of a broader strategy to defend organizational data against evolving cyber threats.
Implementing Encryption in Transit Under Zero Trust
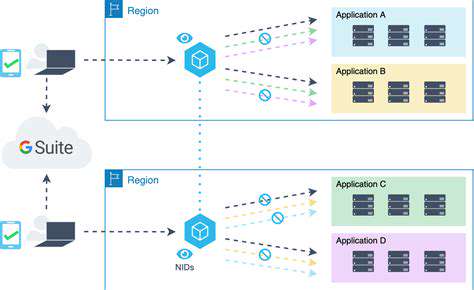
Understanding the Importance of Encryption During Data Transmission
Encrypting data in transit is a cornerstone of Cybersecurity, protecting sensitive information as it moves across networks. Without encryption, data is exposed to interception, leading to breaches and theft. Robust encryption ensures intercepted data remains unreadable to unauthorized parties. Organizations must acknowledge the evolving digital landscape and sophisticated threats, making encryption indispensable.
Encryption also preserves data integrity during transmission. Encrypted data converts to a cipher decipherable only with a specific key, preventing tampering. This is crucial for personal, financial, and confidential business data. Keeping encryption standards current defends against emerging vulnerabilities.
Common Encryption Protocols and Their Applications
Various encryption protocols secure data in transit, each suited to different needs. Transport Layer Security (TLS) is widely used for web communications (HTTPS, email, messaging). Implementing TLS 1.3 enhances security and reduces vulnerabilities from older versions. These protocols use encryption algorithms to create secure client-server channels.
Secure Shell (SSH) is another key protocol for secure remote server management and file transfers. SSH employs strong encryption for user authentication and data protection over unsecured networks. Virtual Private Networks (VPNs) also use encryption to establish secure tunnels for remote corporate access. Protocol choice depends on organizational security needs and operational context.
Implementing Effective Encryption Strategies in Transit
Effective transit encryption requires selecting and configuring the right protocols. Regular updates to encryption software and protocols patch vulnerabilities and counter new threats. Secure cryptographic key management is also critical, as compromised keys undermine encryption.
Training staff on encryption importance and best practices boosts security. Enforcing strict access controls and monitoring network traffic for interception signs is essential. Combining encryption with intrusion detection and multi-factor authentication creates a layered defense, enhancing data protection during transmission.
Protecting Data at Rest with Zero Trust Principles
Implementing Robust Access Controls and Authentication Mechanisms
A core tenet of zero trust for data at rest is enforcing strict access controls. Organizations should adopt multi-factor authentication (MFA) and role-based access control (RBAC) to limit access to authorized personnel only. This reduces unauthorized access risks even if credentials are compromised, strengthening overall data security.
Continuous identity verification and strict access policies create adaptive defenses against evolving threats. Regular access log audits and monitoring detect unusual activity, enabling swift breach responses and maintaining stored data integrity.
Encrypting Data Using Strong Encryption Standards
Encryption is a Zero Trust pillar for data at rest. Advanced standards like AES-256 ensure data remains unreadable to unauthorized users, even during physical or logical breaches. Proper key management prevents compromise and maintains encryption efficacy.
Hardware security modules (HSMs) for key storage and automated key rotation policies prevent long-term key exposure, bolstering data-at-rest security.
Segmenting and Isolating Sensitive Data Repositories
Data segmentation categorizes data by sensitivity, allowing tailored security controls. Zero Trust advocates isolating highly sensitive data to shrink the attack surface and limit breach impacts.
Network segmentation, combined with strict access controls and monitoring, ensures attackers can't easily move laterally. This layered approach significantly boosts data resilience.
Monitoring and Auditing Data Access and Usage
Continuous monitoring of data access patterns is vital for early detection of suspicious activity. Comprehensive audit logs track who accessed data, when, and why, aiding forensic investigations if needed.
Automated alerts flag anomalies like unusual access times or abnormal data retrieval, enabling prompt responses. Regular audit reviews ensure compliance and reinforce Zero Trust posture.
Applying Data Loss Prevention (DLP) Strategies
DLP solutions prevent sensitive data from leaving secure environments unintentionally or maliciously. In Zero Trust, DLP tools monitor data at rest, in use, and in transit, blocking or encrypting unauthorized transfers.
Integrating DLP with other security controls enforces granular policies based on data classification and user roles. This proactive approach reduces leak risks and ensures regulatory compliance.
Regularly Updating Security Policies and Conducting Employee Training
Security policies must evolve with emerging threats and tech advancements. Regular reviews ensure Zero Trust principles stay effective and aligned with organizational goals. Clear policies on data access, encryption, and incident response are critical for consistency.
Comprehensive employee training on data security and Zero Trust best practices is equally important. Educated staff better recognize risks and act accordingly, fostering a culture centered on data protection.
Integrating Zero Trust Data Encryption into Organizational Security Policies
Understanding the Fundamentals of Zero Trust Data Encryption
Zero Trust Data Encryption assumes no device or user is inherently trusted, inside or outside the network. It stresses rigorous verification, continuous monitoring, and encrypting data at rest and in transit to reduce breach and unauthorized access risks.
Implementing Zero Trust for encryption involves advanced cryptographic techniques to maintain data confidentiality and integrity. This approach builds a resilient security posture adaptable to modern threats and complex IT environments.
Aligning Encryption Strategies with Organizational Security Policies
To integrate Zero Trust Data Encryption effectively, organizations must update security policies to include strict encryption standards. This covers key management, encryption algorithms, and access controls aligned with Zero Trust principles.
Policy alignment ensures all departments understand their roles in maintaining data confidentiality and integrity. It also aids compliance with regulations like GDPR, HIPAA, or PCI DSS, which mandate strong encryption for sensitive data.
Implementing Multi-Layered Encryption for Data at Rest and in Transit
Zero Trust Data Encryption requires multiple encryption layers for stored and transmitted data. For example, AES-256 encrypts data at rest, while TLS secures data in transit.
This layered approach minimizes attack surfaces, ensuring additional protections remain if one layer is breached. Encrypting backups and archives prevents unauthorized access from physical theft or insider threats.
Managing Encryption Keys with Zero Trust Principles
Effective key management is critical for encrypted data security. In Zero Trust, keys should be stored securely, rotated regularly, and accessed only by authorized systems or personnel. Hardware Security Modules (HSMs) protect keys from theft or tampering.
Automated key lifecycle management ensures timely renewal and revocation, reducing compromise risks. Key access should be continuously monitored and logged for audits and incident response.
Integrating Identity and Access Management (IAM) with Data Encryption
Zero Trust Data Encryption works best with robust IAM systems that verify identities and enforce least privilege access. This ensures only authenticated, authorized users can decrypt and access sensitive data.
Multi-factor authentication (MFA), role-based access controls, and continuous identity verification enhance security. This layered approach prevents unauthorized access even if credentials are compromised, aligning with Zero Trust tenets.
Monitoring and Auditing Encrypted Data Environments
Continuous monitoring of encrypted data environments detects anomalies, unauthorized access, or potential breaches. Organizations should implement logging to track access attempts, key usage, and encryption events in real-time.
Regular audits of encryption policies and practices identify vulnerabilities and ensure compliance with security standards. Advanced analytics and intrusion detection systems improve visibility, enabling rapid responses to encrypted data incidents.
Training and Cultivating a Security-Aware Organizational Culture
Successful Zero Trust Data Encryption integration requires staff trained in encryption best practices and policies. Regular training, awareness campaigns, and clear communication foster a security-conscious culture prioritizing data protection.
Educating employees on encryption and Zero Trust reduces human error and insider threats. Empowered staff are more likely to follow protocols, report suspicious activity, and contribute to a resilient security environment.











