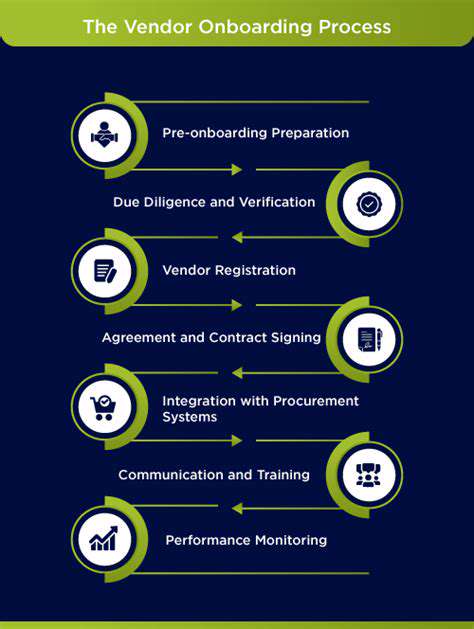
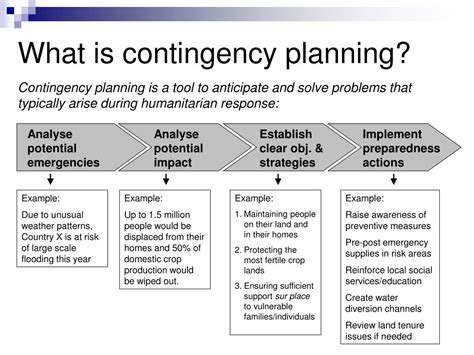
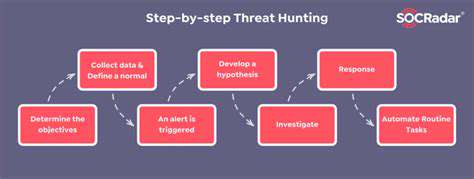
Beyond the Basic Questions: The Importance of Verification
Moving beyond simple questionnaires, robust verification methods are crucial for ensuring the accuracy and reliability of data collected. A questionnaire, while providing a starting point, can be easily manipulated or filled out inaccurately. Verification processes act as a crucial safeguard against such issues, ensuring the integrity of the information gathered. This detailed approach strengthens the foundation for any subsequent analysis and decision-making.
The process of verification goes beyond simply confirming the answers provided in a questionnaire. It delves into independent validation, cross-referencing, and the use of external data sources to establish the truthfulness and completeness of the information. This multi-faceted approach not only strengthens the credibility of the findings but also enhances the confidence level in the conclusions drawn from the data.
Establishing Trustworthy Data
Ensuring the reliability of information is paramount in any research or data collection project. This reliability directly impacts the validity of conclusions and the effectiveness of subsequent decisions. Robust verification methods are essential to address potential biases, errors, and inaccuracies within the data. Effective verification creates a more transparent and trustworthy foundation.
Data verification procedures should be designed to address the specific context of the project. This includes considering the nature of the data, the potential for errors, and the available resources for verification. A tailored approach ensures the process is relevant and effective in achieving the desired outcomes.
Verification Methods: A Diverse Approach
A range of verification methods can be employed, each with its own strengths and limitations. These include direct observation, independent audits, and the use of external databases to cross-reference the information obtained. The selection of the most appropriate method(s) is dependent on the nature of the data being collected and the specific objectives of the project.
Careful consideration of various methods, including interviews with key stakeholders, review of supporting documentation, and the use of readily available publicly accessible data, allows for a more comprehensive and robust validation process. This often leads to more reliable and insightful findings.
Cross-Referencing and External Validation
Cross-referencing data collected with other available information sources is critical for verifying accuracy and completeness. This can involve comparing responses with existing records, data from other surveys, or publicly available information. This process helps to identify inconsistencies and potential errors, ultimately leading to more accurate and reliable results.
External validation is a powerful tool in the verification arsenal. It involves validating data points against external sources of truth. This can provide an additional layer of assurance and confidence in the validity of the collected data. This approach can mitigate potential biases and errors inherent in self-reported data.
The Role of Technology in Verification
Technology plays an increasingly important role in streamlining and enhancing verification processes. Software tools and automated systems can be used to identify inconsistencies, flag potential errors, and expedite the overall verification process. This technology-driven approach improves efficiency and scalability, particularly when dealing with large datasets.
Evaluating the Effectiveness of Verification
It is crucial to evaluate the effectiveness of the verification process. This involves assessing the accuracy of the validated data, identifying any remaining discrepancies, and making adjustments to the process as needed. Regular evaluation of verification procedures ensures ongoing improvement and optimizes the integrity of the data.
Measuring the impact of verification on data quality is essential for understanding the overall value of the process. This includes analyzing the reduction in errors, the improvement in data consistency, and the enhanced reliability of the final results. This careful assessment is vital for future iterations of data collection and verification.