Understanding the Ransomware Threat
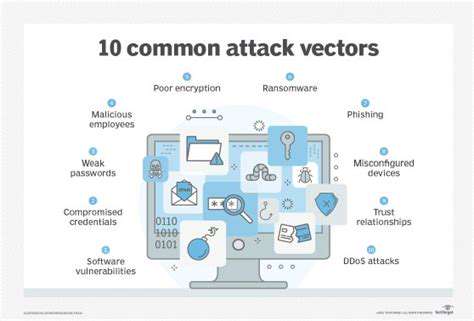
Ransomware attacks are no longer isolated incidents targeting individual users or small businesses. The threat landscape has evolved dramatically, with sophisticated actors employing increasingly complex tactics to infiltrate networks and extort valuable data. These attacks are not just about encrypting files; they involve intricate planning, exploiting vulnerabilities, and leveraging advanced techniques to maximize their impact and financial gain. Understanding this evolution is crucial for organizations of all sizes to effectively mitigate risk.
From simple encryption to double extortion tactics, the methods used by ransomware attackers are constantly adapting. This includes not only the initial infection vector but also the post-exploitation activities, such as data exfiltration and manipulation, making it harder to simply restore from backups.
Advanced Tactics and Techniques
Modern ransomware groups are adept at employing advanced tactics, techniques, and procedures (TTPs) to bypass traditional security measures. This includes exploiting zero-day vulnerabilities, using sophisticated social engineering techniques to target employees, and leveraging legitimate tools to move laterally within the network. Organizations need to proactively identify and address these evolving threats to protect sensitive data and maintain operational continuity.
The use of living-off-the-land binaries, which leverage legitimate system tools for malicious purposes, is another example of the sophistication. These attacks are harder to detect because they blend in with normal system activity.
The Rise of Ransomware-as-a-Service (RaaS)
The emergence of Ransomware-as-a-Service (RaaS) models has democratized the threat landscape. This allows individuals or smaller groups lacking advanced technical skills to launch sophisticated attacks by leveraging the expertise and infrastructure provided by established ransomware operators. This creates a larger and more diverse threat pool, increasing the frequency and complexity of attacks.
RaaS models also offer a variety of features and support, allowing attackers to customize their campaigns to target specific organizations and industries, increasing the potential for financial gain and damage.
The Human Element: Social Engineering
While technical sophistication is critical, the human element remains a key vulnerability in ransomware attacks. Social engineering tactics, such as phishing emails and malicious websites, are frequently used to trick employees into unknowingly installing malware. Employees often lack the awareness or training to recognize these threats, making them easy targets for attackers.
Robust security awareness training programs are essential to educate employees about the latest social engineering tactics and to empower them to identify and report suspicious activity. Regular updates and simulations are critical to maintain effectiveness.
Protecting Against Evolving Threats
Protecting against the evolving ransomware threat requires a multi-layered approach. This includes implementing strong endpoint security, robust network segmentation, regular vulnerability assessments, and proactive security awareness training for employees. Furthermore, organizations must develop incident response plans to effectively handle a ransomware attack and minimize its impact.
Maintaining offline backups of critical data, regularly testing backup restoration procedures, and having clear communication channels are also crucial steps toward mitigating the impact of a ransomware attack. These proactive measures are essential to ensure business continuity and data recovery.
Proactive Security Measures: Building a Multi-Layered Defense

Proactive Security Planning
A proactive approach to security involves anticipating potential threats and vulnerabilities rather than simply reacting to incidents. This forward-thinking strategy emphasizes the importance of establishing robust security policies, procedures, and technologies to mitigate risks before they materialize. Proactive measures are crucial for safeguarding sensitive data and maintaining the integrity of systems. This proactive stance not only strengthens the overall security posture but also fosters a culture of vigilance and responsibility across the organization.
Implementing Multi-Factor Authentication
Multi-factor authentication (MFA) is a cornerstone of proactive security. By requiring multiple forms of verification, such as passwords, security tokens, or biometric scans, MFA significantly increases the difficulty for unauthorized access. This layered approach substantially reduces the risk of compromise, even if one authentication method is compromised. Implementing MFA across all critical systems and accounts is a fundamental step in enhancing security.
Regular Security Audits and Assessments
Regular security audits and assessments are essential for identifying vulnerabilities and weaknesses in existing security measures. These assessments provide a comprehensive evaluation of the security controls in place, pinpointing potential entry points for malicious actors. Identifying these gaps and vulnerabilities allows for proactive mitigation and improvement of the security posture.
These assessments should cover all aspects of the security infrastructure, from network configurations to user access privileges, ensuring that security measures align with the organization's evolving needs and threats. By regularly reviewing and updating security protocols, organizations can significantly reduce their exposure to cyber threats.
Employee Training and Awareness Programs
Human error often plays a significant role in security breaches. Consequently, employee training and awareness programs are essential to foster a security-conscious culture within the organization. These programs should cover various topics, including phishing awareness, safe password practices, and recognizing suspicious emails or websites. By equipping employees with the knowledge and skills to identify and avoid potential threats, organizations can effectively reduce the risk of internal compromise.
Data Encryption and Backup Strategies
Protecting sensitive data is paramount in any proactive security strategy. Data encryption ensures that even if data is intercepted, it remains unintelligible to unauthorized individuals. Robust encryption protocols are vital for safeguarding confidential information. Implementing strong encryption methods across storage systems, databases, and transmission channels is crucial. Complementing encryption is a well-defined and tested data backup and recovery plan, ensuring business continuity in the event of a disaster or breach.
Incident Response Planning
A comprehensive incident response plan is a crucial component of proactive security. This plan outlines the steps to be taken in the event of a security incident, from containment and eradication to recovery and post-incident analysis. This proactive approach to incident response allows organizations to quickly and effectively mitigate the impact of a security breach, limiting the damage and ensuring swift recovery. Well-defined processes and communication protocols are essential elements of an effective incident response plan. Regular testing and rehearsal of the plan ensure that the organization is prepared to handle any security incident promptly and efficiently.
Beyond Technical Measures: Cultivating a Security-Conscious Culture

Cultivating a Culture of Collaboration
Fostering a collaborative environment within a team is crucial for success. Open communication channels and shared goals are essential for effective teamwork. Encouraging employees to share ideas and support each other in problem-solving fosters a sense of collective responsibility and ownership over projects. This collaborative spirit transcends individual efforts, leading to more innovative solutions and a stronger overall team dynamic. This includes actively seeking input from all team members and valuing diverse perspectives.
When team members feel valued and heard, they are more likely to contribute their best work. Regular team-building activities and opportunities for social interaction can also strengthen relationships and promote a sense of camaraderie, further enhancing collaboration.
Investing in Training and Development
Consistent training and professional development opportunities are critical for staying ahead of the curve in any industry. Investing in these programs demonstrates a commitment to employees' growth and advancement, which in turn fosters loyalty and a sense of appreciation. Continuous learning allows employees to adapt to changing technologies and industry best practices, strengthening their skill set and improving their overall performance.
Employees who feel supported in their professional development are more likely to be engaged and motivated. This investment in human capital translates into a more skilled and adaptable workforce, ready to tackle challenges and seize opportunities.
Promoting Open Communication
Open communication is paramount to any successful endeavor. Clear and transparent communication channels ensure that everyone is on the same page, reducing misunderstandings and fostering trust. This includes regular updates, constructive feedback sessions, and readily accessible information.
Promoting a culture where employees feel comfortable expressing concerns and suggestions is crucial for problem-solving and innovation. Actively listening to and responding to employee input demonstrates a commitment to their well-being and a willingness to adapt.
Empowering Decision-Making
Empowering employees to make decisions within their area of expertise is crucial for fostering a culture of ownership and accountability. This delegation of authority allows employees to take initiative, develop their problem-solving skills, and feel a greater sense of responsibility for their work. It also unlocks innovative thinking and allows for quicker responses to changing circumstances.
Providing the necessary resources, training, and support to make informed decisions will help employees feel empowered and confident in their ability to contribute effectively. This empowerment significantly contributes to greater productivity and efficiency.
Recognizing and Rewarding Contributions
Recognizing and rewarding employees' contributions, both big and small, is essential for boosting morale and motivation. This can range from public acknowledgements to formal awards, and even simple expressions of appreciation. Acknowledging achievements, no matter how small, fosters a sense of accomplishment and validates hard work.
A culture of appreciation motivates employees to strive for excellence and encourages continued dedication to their work. Consistent recognition reinforces positive behaviors and fosters a supportive work environment.
Establishing Clear Goals and Expectations
Establishing clear and attainable goals, along with outlining the expected outcomes and responsibilities, is fundamental to any successful endeavor. Clearly defined goals provide a roadmap for employees and help them understand how their contributions align with the overall objectives of the organization. This clarity reduces ambiguity and fosters a shared understanding of priorities. Understanding the expectations for each role and task empowers each individual with a clear sense of direction.
When employees understand the goals and expectations, they are more likely to feel engaged and invested in the organization's success. This fosters a sense of purpose and direction, which in turn contributes to higher productivity and better performance.
Building Trust and Transparency
Building trust and transparency within the organization is paramount for fostering a positive and productive work environment. Open communication, honesty, and accountability are essential components of building this trust. Transparency regarding decisions and their rationale builds confidence and strengthens the relationship between employees and management.
When employees trust leadership and feel informed, they are more likely to be engaged and motivated. Fostering a culture of honesty and openness promotes a sense of shared purpose and responsibility, ultimately contributing to the organization's overall success.