Implementing Robust Security Measures
Protecting point-of-sale (POS) systems requires a multifaceted approach that goes beyond simply installing antivirus software. A comprehensive strategy must encompass physical security measures, rigorous data encryption protocols, and regular security audits. This layered defense approach creates a formidable barrier against potential threats, safeguarding sensitive customer information and maintaining the integrity of financial transactions.
Physical Security and Access Control
Physical security plays a crucial role in protecting POS systems from theft and unauthorized access. Implementing measures like locking POS terminals in secure cabinets, restricting access to designated personnel, and monitoring high-traffic areas can significantly reduce the risk of physical breaches. Furthermore, employing surveillance cameras and robust alarm systems can deter potential criminals and provide valuable evidence in case of an incident.
Data Encryption and Secure Transmission
Protecting sensitive data is paramount. Implementing strong encryption protocols for both data at rest and in transit is essential. This includes using industry-standard encryption algorithms to safeguard customer credit card information, personal identification numbers, and other financial details. Secure transmission protocols, like HTTPS, should be employed for all online transactions to prevent eavesdropping and data breaches.
Employee Training and Awareness
A robust security posture relies heavily on the awareness and vigilance of employees. Comprehensive training programs should be implemented to educate staff on identifying and reporting suspicious activities, phishing attempts, and potential security vulnerabilities. Regular refresher courses and simulated phishing exercises can reinforce these crucial security protocols and help employees become proactive security advocates.
Regular Security Audits and Vulnerability Assessments
Proactive security measures extend to regular security audits and vulnerability assessments. Conducting periodic reviews of POS systems and associated networks can help identify potential weaknesses and vulnerabilities before they are exploited. These assessments should include a thorough examination of software updates, patch management procedures, and overall system configurations, ensuring that the system is adequately protected against the latest threats.
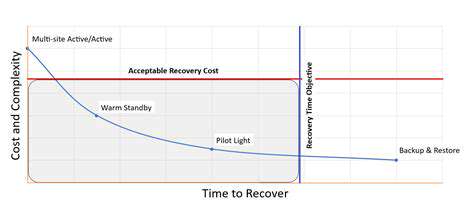
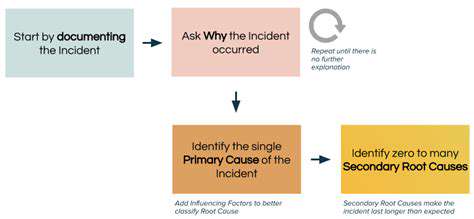
Incident Response Plan and Disaster Recovery
Having a well-defined incident response plan is critical for managing security breaches effectively. This plan should outline the procedures for detecting, responding to, and recovering from security incidents. A robust disaster recovery plan, including backup and restoration procedures, is also essential for minimizing downtime and data loss in case of a major disruption. This preparedness ensures a swift and controlled response to any security incident.
Compliance with Industry Standards and Regulations
Adherence to industry standards and regulations, such as PCI DSS, is a critical aspect of POS security. Complying with these standards ensures that the POS system meets the highest security requirements and protects sensitive financial data. Staying updated with the latest industry best practices and regulatory changes is equally important to maintain a robust security posture.
Safeguarding Inventory: Preventing Shrinkage and Fraud
Preventing Inventory Shrinkage
Inventory shrinkage, a silent thief in retail operations, represents a significant financial loss for businesses. This encompasses a wide range of issues, from shoplifting and employee theft to damaged or misplaced items. Preventing shrinkage requires a multifaceted approach that encompasses both proactive measures and reactive responses. Understanding the various contributing factors, such as poor security systems, inadequate staff training, and even environmental conditions, is crucial in developing a robust strategy to mitigate these losses. A comprehensive inventory management system, coupled with regular stock audits and accurate record-keeping, forms the bedrock of a successful shrinkage prevention program. This proactive approach is essential for maintaining profitability and ensuring the long-term success of any retail establishment.
Implementing robust security measures, including surveillance cameras, well-lit store areas, and strategically placed security personnel, can deter potential theft and create a safer environment for both employees and customers. Regularly reviewing security footage and promptly addressing any suspicious activity can help identify patterns and prevent future occurrences. Furthermore, implementing employee training programs focusing on ethical conduct, inventory handling procedures, and recognizing potential theft indicators can significantly reduce the risk of internal shrinkage. These proactive measures, when coupled with a strong inventory management system, can dramatically improve the bottom line.
Detecting and Addressing Fraudulent Activities
Fraudulent activities, whether internal or external, can severely impact a retail business's financial health. Identifying and mitigating these activities requires a combination of vigilant monitoring, robust internal controls, and a commitment to ethical practices. Regular, thorough audits of inventory records, coupled with sales data analysis, can help identify discrepancies and potential fraudulent activities. An effective system for tracking inventory from receipt to sale, including detailed documentation at each stage, is essential for tracing items and identifying inconsistencies.
Implementing Effective Inventory Management Systems
A strong inventory management system is the cornerstone of preventing shrinkage and fraud. This encompasses a variety of tools and strategies, from sophisticated software solutions to well-defined procedures for receiving, storing, and tracking inventory. Implementing an automated system for inventory tracking and management can provide real-time visibility into stock levels, helping to avoid overstocking or stockouts, and enabling more efficient order fulfillment. Integrating point-of-sale (POS) systems with inventory management software allows for seamless data flow, facilitating accurate record-keeping and reducing the risk of errors.
Accurate record-keeping, regular stock counts, and detailed reporting are paramount. Conducting periodic physical inventory counts, comparing them to recorded data, and addressing discrepancies promptly can reveal potential issues. Establishing clear procedures for receiving, storing, and issuing inventory minimizes the opportunity for errors or manipulation. Furthermore, utilizing barcode scanning and RFID technology can streamline the inventory process, enhance accuracy, and provide real-time visibility into stock levels.
Enhancing Store Security and Employee Training
A secure retail environment is a critical component of a robust inventory protection strategy. This includes implementing measures to deter theft, such as well-lit areas, strategically placed security cameras, and clearly defined security protocols. Regularly reviewing security footage and addressing any suspicious activity promptly is essential in identifying and deterring potential theft. Employee training plays a crucial role in preventing shrinkage and fraud. Comprehensive training programs should focus on ethical conduct, inventory handling procedures, and recognizing potential theft indicators. Empowering employees to report suspicious activity and fostering a culture of accountability is key in reducing the risk of internal theft.
Simulations offer a powerful tool for practical application, allowing users to experience real-world scenarios in a controlled environment. This is particularly valuable in fields like medicine, engineering, and business, where experimenting in the real world can be expensive, time-consuming, or even dangerous. By simulating various conditions and outcomes, individuals can gain valuable experience and refine their skills without the risks associated with real-world experimentation. This process can lead to improved decision-making and problem-solving abilities.
Implementing a Comprehensive Security Program
Establishing a Robust Baseline
A comprehensive security program for a retail environment starts with a thorough assessment of existing security measures and identifying vulnerabilities. This baseline assessment should cover physical security, such as access control systems, surveillance cameras, and alarm systems, as well as digital security, including point-of-sale (POS) systems, inventory management software, and customer data repositories. Critically evaluating current procedures and technologies is crucial to understanding the existing security posture and pinpointing areas requiring improvement, enabling informed decision-making.
Protecting Point-of-Sale Systems
Protecting point-of-sale (POS) systems from cyberattacks is paramount. This involves implementing strong authentication protocols, employing encryption to safeguard sensitive transaction data, and regularly updating software to patch known vulnerabilities. Security measures should also include intrusion detection systems to monitor network traffic for suspicious activity, and robust data backup and recovery plans in case of system breaches. Employing multi-factor authentication and regular security awareness training for staff handling POS systems is also essential to prevent human error.
Enhancing Physical Security Measures
Physical security is just as critical as digital security. Implementing robust access control systems, including keycard entry, biometric scanning, or security guards, is vital in deterring theft and vandalism. Strategically placed surveillance cameras with comprehensive coverage, including high-definition recording and real-time monitoring, provide a powerful deterrent and valuable evidence in the event of a crime. Regular security patrols, well-lit parking lots, and secured storage areas for inventory further contribute to a secure environment.
Implementing Employee Training and Awareness
A crucial component of any security program is employee training and awareness. Staff members must be educated on recognizing and reporting suspicious activities, such as shoplifting, theft, or potential security breaches. Training should cover procedures for handling suspicious packages, responding to alarms, and the proper use of security equipment. Regular training sessions, coupled with ongoing communication regarding security protocols, are essential to maintain a vigilant and informed workforce.
Developing Incident Response Plans
Having a well-defined incident response plan is critical for effectively managing security incidents. This plan should outline procedures for detecting, containing, and recovering from security breaches. It should specify roles and responsibilities for different personnel, including security personnel, management, and IT staff. Clear communication channels and escalation procedures are essential to ensure a swift and effective response in the event of an incident, mitigating potential damage and minimizing financial losses. Regularly reviewing and updating the incident response plan is vital to adapt to evolving security threats.