The Impact of Ransomware on National Security

The Escalating Threat Landscape
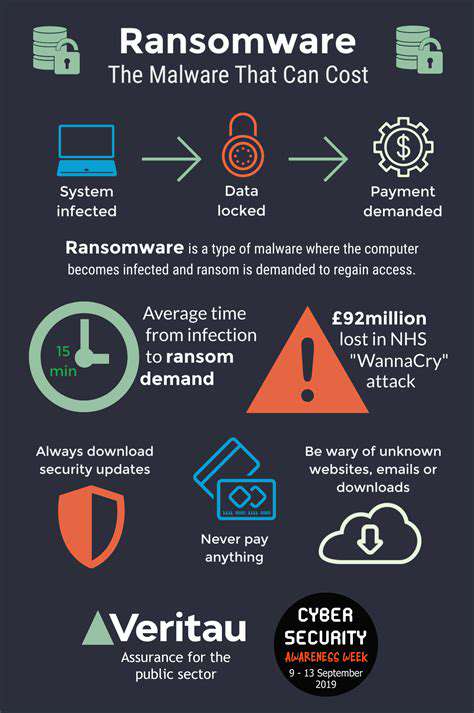
Ransomware attacks are no longer isolated incidents targeting individual businesses; they are increasingly sophisticated and impactful, posing a significant threat to national security and critical infrastructure. The scale and frequency of these attacks are rising exponentially, demanding urgent attention and proactive measures to mitigate the risk. This growing threat necessitates a comprehensive approach that considers both immediate response and long-term prevention strategies.
The evolving tactics of ransomware actors, including double extortion and supply chain attacks, are compounding the challenges faced by governments and organizations alike. The financial and reputational damage caused by these attacks can be devastating, and the disruption to essential services can have far-reaching consequences.
Economic Disruption and Loss
The financial consequences of ransomware attacks are substantial, impacting not only the targeted organizations but also the broader economy. Significant sums are lost in ransom payments, recovery costs, and lost productivity. These losses can cripple businesses and undermine economic stability, particularly in sectors reliant on uninterrupted operations.
Beyond the immediate financial losses, ransomware attacks can lead to cascading effects. Supply chains can be disrupted, production halted, and consumer confidence eroded. These indirect consequences can have a prolonged and detrimental impact on the national economy.
National Security Concerns
Ransomware attacks targeting critical infrastructure, such as healthcare facilities, energy providers, and government agencies, pose a direct threat to national security. Disruption to essential services can have devastating consequences, potentially jeopardizing public safety and national stability.
The potential for ransomware to be used as a weapon of mass disruption by state-sponsored actors or terrorist groups necessitates a robust national security strategy. Protecting critical infrastructure and ensuring the resilience of national systems against these threats is paramount.
Cybersecurity Preparedness and Response
A robust cybersecurity posture is crucial for mitigating the impact of ransomware attacks. This includes implementing strong security measures, such as robust firewalls, intrusion detection systems, and multi-factor authentication. Regular security audits, employee training, and incident response plans are equally important components of a comprehensive strategy.
Developing and maintaining a well-coordinated incident response plan is critical. This includes clear protocols for identifying, containing, and recovering from ransomware attacks. Effective communication channels between affected organizations and government agencies are vital for a swift and coordinated response.
International Cooperation and Information Sharing
Given the transnational nature of ransomware attacks, international cooperation is essential for effective prevention and response. Sharing intelligence, best practices, and threat information across borders can significantly enhance collective defenses. Collaboration between law enforcement agencies, cybersecurity experts, and international organizations is critical.
Policy and Regulatory Frameworks
Robust policy and regulatory frameworks are needed to address the challenges posed by ransomware. These frameworks should include guidelines for data protection, incident reporting requirements, and incentives for cybersecurity investments. Clear legal frameworks for prosecuting ransomware actors and holding them accountable are also essential for deterring future attacks.
Public Awareness and Education
Raising public awareness about ransomware threats and best practices for cybersecurity is crucial. Educating individuals and organizations about the risks, signs of infection, and preventative measures can significantly reduce the vulnerability to attack. Promoting strong cybersecurity hygiene through public awareness campaigns will make a substantial difference in preventing ransomware attacks. Individuals are often the weakest link in a cybersecurity chain.
Protecting Critical Infrastructure from Ransomware Attacks
Protecting Physical Assets
Protecting critical infrastructure involves safeguarding physical assets from a wide range of threats, including natural disasters, acts of vandalism, and deliberate attacks. Robust security measures are crucial to mitigating potential damage and ensuring the continued operation of essential services. This includes implementing physical security protocols, such as access controls, surveillance systems, and perimeter fencing. Furthermore, regular inspections and maintenance of critical infrastructure components are essential for identifying and addressing potential vulnerabilities.
Properly maintained infrastructure is less susceptible to failures. This preventative approach not only reduces the risk of costly repairs but also helps maintain the reliability of vital services. Implementing comprehensive risk assessments is paramount to understanding the specific threats facing each asset and tailoring security measures accordingly.
Ensuring Network Security
The increasing reliance on interconnected digital systems makes network security a critical aspect of protecting critical infrastructure. Cybersecurity threats pose a significant risk to the integrity and availability of these systems. Implementing robust firewalls, intrusion detection systems, and security information and event management (SIEM) solutions is essential to detect and respond to malicious activity effectively. Regular security audits and vulnerability assessments are essential to identify weaknesses and apply appropriate patches or updates.
Human Capital Security
Protecting critical infrastructure also involves safeguarding its human capital. This includes the employees, contractors, and other personnel involved in the operation and maintenance of these systems. Background checks, security clearances, and access controls tailored to individual roles are necessary to minimize the risk of insider threats. Comprehensive security training programs are essential to equip personnel with the knowledge and skills needed to identify and report suspicious activities.
A significant part of this is fostering a culture of security awareness within the organization. Employees must understand their role in protecting the infrastructure and be empowered to report potential threats without fear of retribution.
Disaster Preparedness and Response
Disasters, both natural and man-made, can severely impact critical infrastructure. Having a well-defined disaster preparedness and response plan is essential. This plan should outline procedures for responding to various types of emergencies, including communication protocols, evacuation strategies, and resource allocation. Regular drills and exercises are crucial for testing the effectiveness of the plan and ensuring personnel are adequately trained to respond effectively.
Proactive measures, such as developing contingency plans for essential services and establishing backup power sources, significantly enhance resilience in the face of emergencies. Maintaining consistent communication channels during emergencies is also critical for coordinating response efforts and providing timely updates to stakeholders.
Compliance and Regulatory Frameworks
Adhering to relevant compliance and regulatory frameworks is crucial for protecting critical infrastructure. These frameworks often outline specific security standards and requirements that organizations must meet. This includes understanding and implementing industry best practices and regulations. Keeping abreast of evolving threats and regulatory changes is vital to ensure ongoing compliance.
Maintaining thorough documentation of security measures and compliance efforts is essential for demonstrating accountability and transparency. Regular audits and assessments conducted by independent parties can further validate the effectiveness of implemented security protocols and demonstrate compliance with established standards.
International Cooperation and Information Sharing

Global Collaboration in Information Sharing
International cooperation in information sharing is crucial for addressing global challenges, from pandemics to economic crises. Effective collaboration requires a commitment to transparency and data sharing across borders. This fosters a more interconnected and informed global community, enabling quicker responses to emerging issues and facilitating the exchange of best practices.
The sharing of information is not simply about exchanging data; it's about building trust and understanding between nations. This collaborative effort allows for the identification of patterns, trends, and potential risks that may not be evident within a single nation's borders.
Technological Advancements in Information Exchange
Technological advancements are revolutionizing the way information is shared internationally. The rise of cloud computing, secure communication platforms, and advanced data analytics tools has facilitated faster and more efficient international collaboration. These advancements enable the rapid dissemination of crucial data, allowing for quicker responses to crises and improved decision-making.
Moreover, the development of standardized data formats and protocols is critical to ensuring seamless information exchange across different systems and countries. This promotes interoperability and avoids the complexities of translating data between incompatible formats.
Addressing Barriers to International Information Sharing
Despite the benefits, several barriers to effective international information sharing persist. These include differing legal frameworks, varying levels of technological infrastructure, and concerns about data privacy and security. Overcoming these obstacles is essential to realizing the full potential of global cooperation.
Furthermore, cultural differences and language barriers can also impede the smooth flow of information. Developing effective communication strategies that account for these factors is key to fostering trust and mutual understanding.
Ethical Considerations in Data Sharing
International cooperation in information sharing must prioritize ethical considerations. Ensuring data privacy and security is paramount, particularly when sensitive information is exchanged between nations. Robust protocols and regulations are needed to safeguard confidential data and prevent misuse or unauthorized access.
Furthermore, the potential for bias in data sets must be acknowledged and mitigated. International collaboration should strive to collect and analyze data in a way that avoids perpetuating or amplifying existing inequalities.
The Role of International Organizations in Facilitating Cooperation
International organizations play a critical role in facilitating international cooperation and information sharing. These organizations often act as neutral platforms for dialogue and collaboration, bringing together diverse stakeholders and fostering a shared understanding of global challenges.
The Impact of Information Sharing on Global Governance
Effective information sharing can significantly impact global governance. It enables the development of more informed and responsive policies, leading to better decision-making at both the national and international levels. Improved global governance, in turn, fosters greater stability and cooperation on a global scale.
The availability of reliable and timely information allows for the identification of systemic issues and the development of effective solutions to address them.