Ransomware Insurance: A Safety Net or a Crutch for Cyber Incidents?
Ransomware Insurance: A Safety Net or a Crutch for Cyber Incidents?
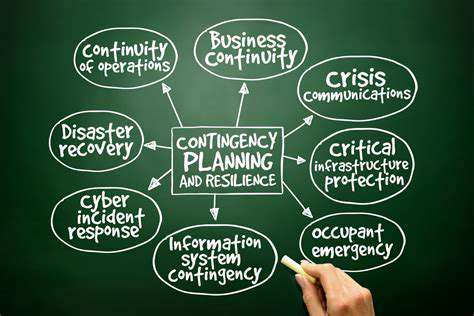
Ransomware Recovery Strategies: Getting Back Online After an Attack
Ransomware Recovery Strategies: Getting Back Online After an Attack
Supply Chain Risk Scoring: Quantifying Vulnerabilities
Supply Chain Risk Scoring: Quantifying Vulnerabilities
Industrial IoT (IIoT) Security: Protecting Critical Infrastructure
Industrial IoT (IIoT) Security: Protecting Critical Infrastructure
Zero Trust for Operational Technology (OT): Bridging IT/OT Security Gaps
Zero Trust for Operational Technology (OT): Bridging IT/OT Security Gaps
Smart Agriculture IoT: Protecting Crops, Data, and Operations
Smart Agriculture IoT: Protecting Crops, Data, and Operations
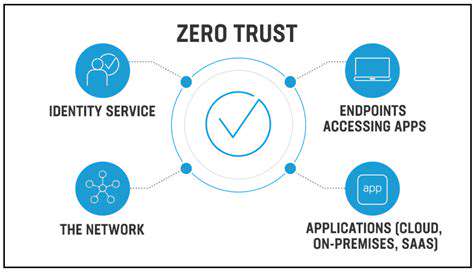
Decoding Zero Trust: A Paradigm Shift in Network Security
Decoding Zero Trust: A Paradigm Shift in Network Security
Zero Trust Principles for Cloud Native Applications
Zero Trust Principles for Cloud Native Applications
Zero Trust vs VPN: Choosing the Right Secure Access Solution
Zero Trust vs VPN: Choosing the Right Secure Access Solution
Zero Trust for Cloud Native Security: A Modern Approach
Zero Trust for Cloud Native Security: A Modern Approach
AI for Security Awareness: Training Employees Against New and Evolving Threats
AI for Security Awareness: Training Employees Against New and Evolving Threats
Deep Learning in Cybersecurity: Predicting Emerging Threats
Deep Learning in Cybersecurity: Predicting Emerging Threats
Zero Trust Network Access (ZTNA): The Evolution of Secure Remote Access
Zero Trust Network Access (ZTNA): The Evolution of Secure Remote Access
Zero Trust Network Segmentation: Enhancing Granular Network Control
Zero Trust Network Segmentation: Enhancing Granular Network Control
The Economics of Ransomware: Why Cybercriminals Target Your Data
The Economics of Ransomware: Why Cybercriminals Target Your Data
Ransomware and Incident Response: A Step by Step Playbook
Ransomware and Incident Response: A Step by Step Playbook
AI Driven Phishing Detection: Outsmarting Evolving Threats
AI Driven Phishing Detection: Outsmarting Evolving Threats
The Human Factor in Ransomware: Phishing and Social Engineering
The Human Factor in Ransomware: Phishing and Social Engineering
Preventing Ransomware: Proactive Measures to Safeguard Your Business
Preventing Ransomware: Proactive Measures to Safeguard Your Business