Featured
Aug 21, 2025
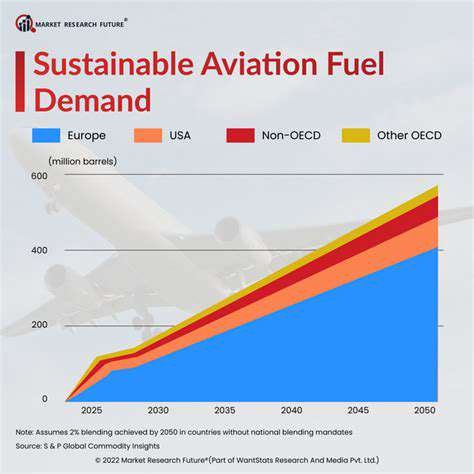
Sustainable Aviation Fuel Production
Sustainable Aviation Fuel Production
Featured
Aug 21, 2025
Lunar Dust Characterization
Lunar Dust Characterization
Featured
Aug 21, 2025
OSIRIS REx Mission: Asteroid Sample Return
OSIRIS REx Mission: Asteroid Sample Return
Featured
Aug 21, 2025
Satellite Based Smart Farming
Satellite Based Smart Farming
Featured
Aug 20, 2025
Space Based Quantum Communication
Space Based Quantum Communication
Featured
Aug 20, 2025
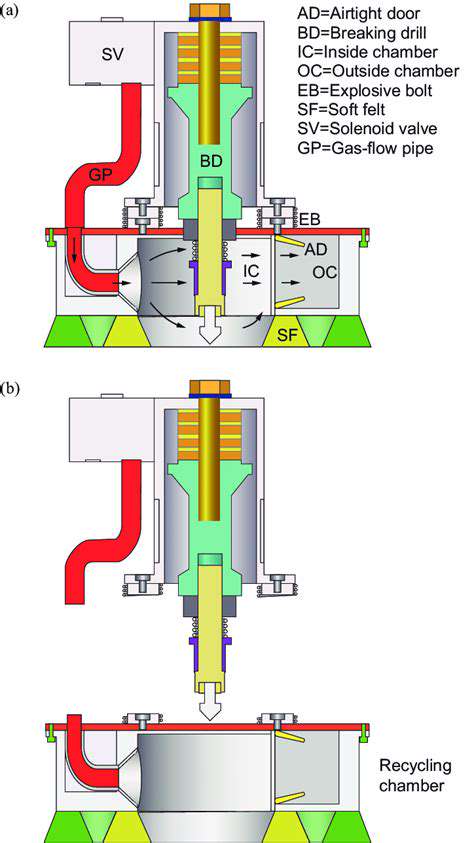
Aero Innovations: The Future of Flight
Aero Innovations: The Future of Flight
Featured
Aug 20, 2025
AI in Aerospace Design
Reduce time-to-market with automated analysis and iterative design improvements.- Improved Performance: Achieve optimal aerodynamic, structural, and safety features through data-driven insights.- Cost Savings: Lower prototyping and testing expenses with virtual simulations and predictive analytics.- Enhanced Innovation: Enable engineers to explore complex design spaces and innovative solutions with AI assistance.---Harness the power of AI to transform aerospace design processes. Whether you're looking to accelerate project timelines, improve aircraft performance, or cut costs, AI-driven optimization tools are the future of aerospace engineering. Stay ahead of the competition by integrating intelligent design solutions that push the boundaries of innovation and efficiency.
Featured
Aug 20, 2025
Space Based Human Exploration of Mars
Space Based Human Exploration of Mars
Featured
Aug 20, 2025
Space Sustainability: Ensuring Long Term Access to Space
Space Sustainability: Ensuring Long Term Access to Space
Featured
Aug 19, 2025
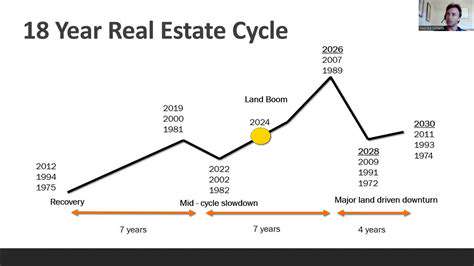
Future of Aerospace Industry
Future of Aerospace Industry
Featured
Aug 19, 2025
Space Based Space Situational Awareness
Space Based Space Situational Awareness
Featured
Aug 19, 2025
Satellite Based Smart Agriculture Practices
Satellite Based Smart Agriculture Practices
Featured
Aug 18, 2025
Sustainable Aviation Ecosystem
Sustainable Aviation Ecosystem
Featured
Aug 18, 2025
Next Generation Space Telescopes: Beyond Webb
Next Generation Space Telescopes: Beyond Webb
Featured
Aug 18, 2025
Lunar Water Ice Distribution
Lunar Water Ice Distribution
Featured
Aug 18, 2025
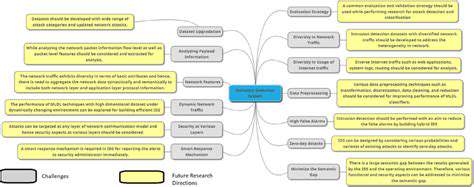
Space Based Space Debris Detection
Space Based Space Debris Detection
Featured
Aug 17, 2025
AI in Aerospace Product Development
AI in Aerospace Product Development
Featured
Aug 17, 2025
SETI Research: Listening for Extraterrestrial Life
SETI Research: Listening for Extraterrestrial Life
Featured
Aug 17, 2025
Space Based Communications Technologies
Space Based Communications Technologies