Sort By:
View:
Vertical Landing Technology: Pioneering Rocket Reusability
Vertical Landing Technology: Pioneering Rocket Reusability
Views
READ MORE →
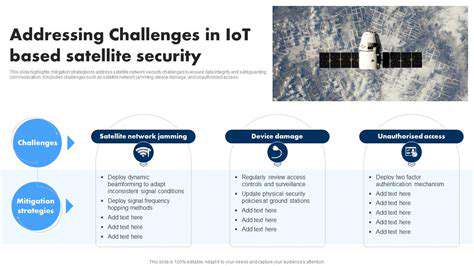
Satellite Based Infrastructure Resilience
Satellite Based Infrastructure Resilience
Views
READ MORE →
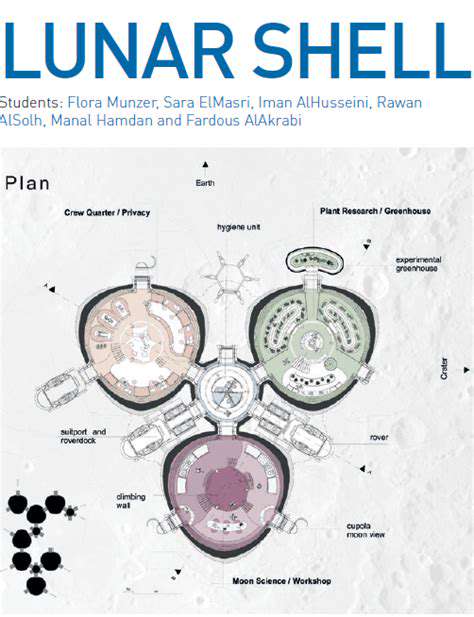
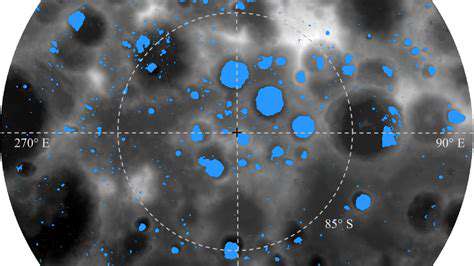
Lunar Ice Extraction Methods: Technologies and Challenges
Lunar Ice Extraction Methods: Technologies and Challenges
Views
READ MORE →
Satellite Communications for Remote Operations
Satellite Communications for Remote Operations
Views
READ MORE →
Advanced Flight Control Systems for New Aircraft
Advanced Flight Control Systems for New Aircraft
Views
READ MORE →
Space Tourism Safety Regulations: Ensuring Secure Journeys
Space Tourism Safety Regulations: Ensuring Secure Journeys
Views
READ MORE →
Space Based Manufacturing of Pharmaceuticals
Space Based Manufacturing of Pharmaceuticals
Views
READ MORE →