Challenges and Considerations in ZTNS Implementation
Network Segmentation Complexity
Implementing Zero Trust Network Segmentation (ZTNS) presents a significant challenge in managing the complexity of network segmentation. The traditional approach to network security often relied on perimeter defenses, a relatively straightforward model. ZTNS, however, requires a granular level of access control, meticulously defining who can access what resources and from where. This necessitates a comprehensive understanding of every application, user, and device within the organization's network, which can be a daunting task for large and complex environments. Careful planning and meticulous documentation are crucial to avoid creating more problems than solutions in the segmentation process. This process demands a shift from a broad, perimeter-based approach to a highly granular, identity-centric approach to security.
Furthermore, the sheer scale of the network can make the segmentation process incredibly intricate. Each application, server, and device needs to be carefully considered, and the segmentation policies must be precisely tailored to ensure optimal security without hindering productivity. Over-segmentation can lead to operational inefficiencies, increased administrative overhead, and potential bottlenecks in data flow. Therefore, a balanced approach is essential, ensuring appropriate security without compromising performance.
Identity and Access Management (IAM) Integration
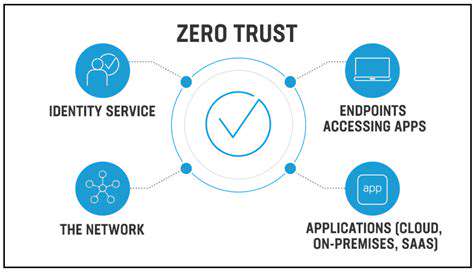
A crucial aspect of ZTNS implementation is seamlessly integrating it with Identity and Access Management (IAM) systems. Effective ZTNS requires precise identification and authentication of users, devices, and applications. This demands a robust IAM solution capable of providing real-time, context-aware access control. Implementing ZTNS without a strong IAM foundation can lead to significant security gaps, as unauthorized access attempts might circumvent the segmentation policies. The integrity and accuracy of user and device identities are paramount to ensuring the effectiveness of ZTNS.
Integrating existing IAM systems with ZTNS can be a complex process. Existing systems may not be designed for the granularity and dynamic nature of ZTNS policies. Careful planning and potentially custom integrations or modifications may be necessary to ensure a smooth transition. The successful integration of IAM with ZTNS is essential to maintaining a secure and efficient network environment. It enables the system to make informed decisions about access based on the identity and context of the user, device, or application. This dynamic evaluation of access requests is critical for responding to evolving security threats.
Maintaining Ongoing Management and Monitoring
ZTNS implementation is not a one-time project; it requires ongoing management and monitoring to maintain its effectiveness. Security threats and vulnerabilities evolve constantly, and ZTNS policies must be updated and adjusted accordingly. This ongoing maintenance includes regular review and refinement of segmentation rules, monitoring for anomalies, and implementing appropriate responses to security incidents. Failing to maintain these processes can render the ZTNS strategy ineffective, leaving the organization exposed to potential breaches.
Effective monitoring tools are essential for identifying potential security issues and maintaining the integrity of the ZTNS implementation. These tools need to provide real-time visibility into network traffic, user activity, and application behavior. Furthermore, the ability to quickly identify and respond to security incidents is critical. The monitoring and management aspects of ZTNS are as crucial as the initial implementation, ensuring long-term security and operational efficiency.