Protecting Sensitive Data and Maintaining Operational Continuity

Protecting Sensitive Data
Protecting sensitive data is paramount in today's digital landscape. Data breaches can have devastating consequences, impacting individuals and organizations alike. From financial records to personal information, safeguarding sensitive data requires a multifaceted approach that encompasses robust security measures and a vigilant awareness of potential threats.
This involves not only implementing strong encryption protocols and access controls but also educating users about safe online practices and the importance of recognizing phishing attempts and other malicious activities. Regular security audits and vulnerability assessments are crucial to identify and address potential weaknesses in systems and processes.
Maintaining Data Integrity
Data integrity is essential for ensuring the accuracy, reliability, and trustworthiness of information. Maintaining data integrity involves a range of procedures, including data validation, error detection, and data backup and recovery strategies. Robust data management processes are essential to prevent data corruption and ensure its continued use.
Implementing version control systems for data changes is also important for maintaining a clear audit trail and facilitating data recovery in case of errors or accidental alterations. Careful planning and proactive measures are required to uphold data integrity.
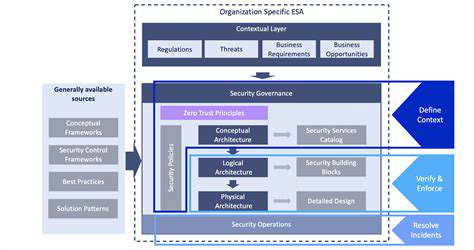
Implementing Robust Security Measures
Implementing robust security measures is crucial for protecting sensitive data. This includes using strong passwords, enabling multi-factor authentication, and regularly updating software and operating systems. These measures help to mitigate the risk of unauthorized access and data breaches.
Employing firewalls and intrusion detection systems can further bolster security by monitoring network activity and identifying potential threats. Regular security awareness training for employees is also essential to ensure that they understand and follow best practices for protecting sensitive data.
Data Backup and Recovery Strategies
Effective data backup and recovery strategies are critical for minimizing the impact of data loss. These strategies should include regular backups of critical data to offsite locations to ensure data availability in case of a disaster or system failure. Implementing a comprehensive disaster recovery plan is crucial for restoring data and systems quickly and efficiently.
This plan should outline the steps to be taken in the event of a disaster, ensuring business continuity and minimizing downtime. Regular testing of the recovery plan is also essential to verify its effectiveness.
Employee Training and Awareness
Employee training and awareness programs are essential components of a comprehensive data security strategy. These programs should educate employees about the importance of protecting sensitive data, and how to identify and report potential threats. Regular training sessions and materials can help employees understand the risks associated with social engineering tactics and other malicious activities.
Incident Response Planning
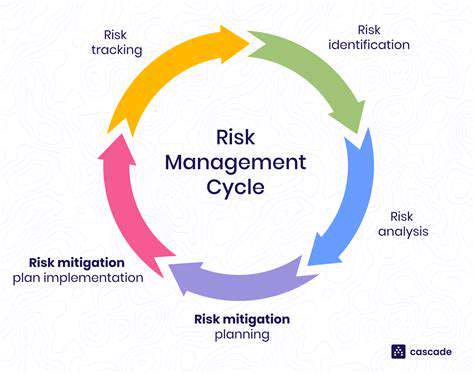
A well-defined incident response plan is crucial for responding to data breaches or security incidents effectively. This plan should outline the procedures for identifying, containing, and recovering from security incidents. A clear chain of command and communication protocols are essential during an incident.
This plan should also include provisions for notifying affected individuals and regulatory bodies, and should be regularly reviewed and updated to reflect evolving threats and vulnerabilities.
Compliance and Regulations
Adhering to relevant compliance and regulatory requirements is another important aspect of data protection. Organizations must be aware of and comply with applicable laws and regulations, such as GDPR or HIPAA, to avoid penalties and maintain trust. Organizations must understand their obligations under data protection laws and implement measures to meet these obligations.
Regular reviews of relevant legislation and industry best practices are essential to ensure ongoing compliance and avoid potential legal issues. This will help maintain a secure and trustworthy environment.