The Evolving Landscape of Cyber Threats
Understanding the Sophistication of Modern Threats
The cyber landscape is constantly evolving, with malicious actors developing increasingly sophisticated techniques to exploit vulnerabilities. This evolution requires a proactive and adaptable approach to security awareness training, moving beyond basic password hygiene and into more nuanced strategies that address the complexities of today's threats. Traditional security measures often fall short against targeted attacks, social engineering, and advanced persistent threats (APTs), which demand a higher level of understanding and preparedness from employees.
Understanding the motivations and tactics of these threat actors is crucial for effectively mitigating risk. This involves analyzing the techniques used in recent attacks, such as phishing campaigns, malware distribution, and data breaches, to identify patterns and develop targeted training strategies to counter them.
The Rise of AI-Powered Attacks
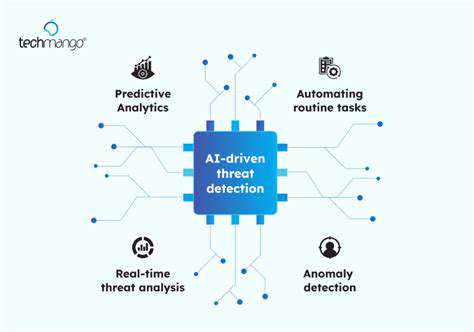
Artificial intelligence (AI) is no longer just a tool for security professionals; it's a weapon in the hands of cybercriminals. AI-powered phishing campaigns are becoming more convincing, using machine learning to personalize messages and bypass traditional spam filters. This necessitates a shift in security awareness training to equip employees with the skills to recognize the subtle indicators of AI-driven attacks.
Moreover, AI is being leveraged to automate malicious activities, such as generating realistic synthetic data for phishing emails, making detection even more challenging. This requires training employees to look beyond the surface-level characteristics and delve deeper into the suspicious activity to identify the underlying AI footprint.
The Importance of Human Factors in Cybersecurity
While technology plays a significant role in cybersecurity, human error remains a critical vulnerability. Phishing attacks often succeed because employees lack the necessary awareness to identify suspicious emails or links. Security awareness training must address the human element of cybersecurity, equipping employees with the critical thinking skills needed to assess risk and make informed decisions.
This includes understanding the psychology behind social engineering tactics, recognizing the emotional triggers that can lead to mistakes, and fostering a culture of caution and skepticism in handling potentially risky situations.
Targeted Training for Specific Roles
Security awareness training should be tailored to the specific roles and responsibilities of employees. A marketing team member, for example, faces different cyber threats than a financial analyst. This role-specific approach ensures that training is relevant and addresses the unique vulnerabilities of each department.
Tailoring training to specific roles helps employees understand and recognize the types of threats they are most likely to encounter. This localized approach fosters a sense of ownership and responsibility in safeguarding company data.
The Value of Simulated Phishing and Security Assessments
Simulated phishing exercises are invaluable tools for evaluating the effectiveness of security awareness training. These exercises provide employees with a safe environment to practice identifying and reporting suspicious emails, links, or attachments.
Regular assessments further enhance the training's impact by measuring employees' understanding and knowledge retention. These practical exercises, combined with feedback and debriefings, help reinforce learning and improve overall security posture.
Implementing and Measuring the Impact of Training
Effective security awareness training is not a one-time event but an ongoing process. Regular training sessions, coupled with periodic reinforcement through newsletters, articles, and reminders, are crucial for maintaining a high level of security awareness.
Metrics and reporting are essential for evaluating the impact of training programs. Tracking the results of simulated phishing exercises, incident reports, and employee feedback provides valuable data to refine training strategies and ensure continuous improvement.
Building a Culture of Cybersecurity
A strong cybersecurity culture is built on a foundation of shared responsibility and proactive engagement. It's not just about training employees; it's about fostering a mindset that prioritizes security in all aspects of work.
Encouraging open communication about security concerns, recognizing and rewarding employees for their vigilance, and promoting a collaborative approach to threat detection are all vital components of a robust cybersecurity culture.
Personalized Learning for Enhanced Engagement

Tailored Learning Experiences
Personalized learning approaches recognize that each student possesses unique learning styles, strengths, and weaknesses. This understanding is crucial for creating effective and engaging educational experiences. By tailoring instruction and activities to individual needs, educators can foster a deeper understanding of the subject matter and encourage greater student motivation. Personalized learning often involves adapting pacing, content, and assessment methods to ensure that each student progresses at their own optimal rate.
A key component of personalized learning is the use of diverse instructional materials and resources. These resources can range from interactive simulations and online learning platforms to hands-on projects and collaborative activities. By providing a variety of choices, learners are empowered to explore concepts in ways that resonate most effectively with their individual preferences.
Adaptive Content Delivery
Adaptive learning platforms utilize sophisticated algorithms to adjust the difficulty and pacing of educational content in real-time, based on the student's performance. This dynamic approach ensures that students are consistently challenged while avoiding frustration from material that is too easy or too complex. This personalized feedback mechanism allows for continuous improvement and a more efficient learning journey.
The adaptability of these platforms enables individualized learning paths. Students can explore specific areas of interest or delve deeper into topics that present challenges, leading to a more in-depth and thorough understanding of the subject matter.
Differentiated Instruction Strategies
Differentiated instruction is a cornerstone of personalized learning. It involves tailoring teaching methods, materials, and assessments to meet the diverse needs of all learners. Teachers employ various strategies, such as flexible grouping, varied learning activities, and multiple assessment options, to cater to different learning styles, paces, and abilities. This approach ensures that every student has the opportunity to succeed and reach their full potential.
By employing flexible grouping strategies, teachers can create dynamic learning environments that cater to different learning styles. Students can collaborate with peers who share similar interests or learning needs, fostering a supportive and collaborative learning atmosphere. This personalized approach can greatly enhance the learning experience for all students.
Personalized Feedback and Assessment
Providing personalized feedback is vital for student growth. Constructive feedback, tailored to individual learning needs, helps students identify areas for improvement and strengthens their understanding of the subject matter. Regular and specific feedback helps students understand their progress and adjust their learning strategies accordingly.
Alternative assessment methods, such as projects, presentations, and portfolios, allow for a more comprehensive evaluation of student understanding. These methods often provide a more engaging and dynamic way to showcase student learning, and allow teachers to gain a richer understanding of individual student strengths and weaknesses.
Student Agency and Motivation
Personalized learning empowers students by giving them a voice in their education. When students have control over their learning journey, they are more likely to be motivated and engaged. This sense of ownership fosters a deeper understanding and appreciation for the subject matter. By incorporating student preferences and interests, educators can create a more engaging and supportive learning environment.
Student agency fosters a sense of responsibility and ownership over their learning, leading to increased intrinsic motivation and a stronger connection to the material. This empowers students to actively participate in their educational process and take ownership of their learning goals, ultimately leading to greater academic success and a more fulfilling educational experience.
Technology Integration for Personalized Learning
Technology plays a crucial role in facilitating personalized learning. Learning management systems (LMS), educational software, and online resources can provide customized learning pathways and adaptive assessments. By leveraging the power of technology, educators can deliver learning materials and support that are tailored to individual student needs.
Interactive learning platforms and multimedia resources can cater to diverse learning styles, making education more accessible and engaging. Using technology effectively provides valuable insights into student progress and performance, enabling educators to adjust their teaching strategies in real-time to optimize learning outcomes.
Measuring Effectiveness and Continuous Improvement

Defining Effectiveness Metrics
Establishing clear and measurable metrics is crucial for evaluating the effectiveness of any initiative. These metrics should be directly tied to the project's objectives and provide a quantifiable way to track progress. For instance, if the goal is to increase brand awareness, a suitable metric could be the number of social media engagements or the growth in website traffic.
A well-defined metric system allows for objective assessment of progress and identifies areas needing improvement. It ensures that efforts are focused on achieving tangible results rather than just completing tasks.
Identifying Key Performance Indicators (KPIs)
KPIs are specific, quantifiable metrics that measure progress toward a particular goal. They offer a focused view of the aspects that are most important to the success of a project. For example, if a marketing campaign aims to boost sales, KPIs might include conversion rates, average order value, and customer acquisition cost.
Tracking Progress and Data Collection
Implementing a robust system for collecting and analyzing data is essential for tracking progress. This involves establishing consistent data collection methods and choosing appropriate tools for analysis. Regular data analysis allows teams to identify trends and patterns, enabling proactive adjustments to optimize outcomes. Data-driven decision-making is paramount to achieving optimal results.
Effective data collection requires careful planning and meticulous execution to ensure accuracy and reliability.
Analyzing Results and Identifying Trends
Analyzing the collected data is a critical step in understanding the effectiveness of the initiatives. This involves identifying trends, patterns, and correlations. Careful examination of the data can reveal insights into what is working well and what aspects require improvement. By understanding the trends, you can adjust strategies and allocate resources more effectively.
Implementing Adjustments Based on Analysis
Analysis of the data should lead to concrete adjustments in strategy. This might involve refining existing approaches, introducing new tactics, or reallocating resources. Implementing these adjustments based on the data analysis is key to achieving continuous improvement and maximizing the impact of initiatives.
Adaptability and a willingness to adjust based on data are essential for long-term success.
Continuous Monitoring and Evaluation
Continuous monitoring and evaluation are not one-time activities but ongoing processes. It's vital to regularly track progress against established metrics and KPIs. This allows for adjustments to strategies and tactics as needed to maintain optimal performance. Regular evaluations help to ensure that projects are staying on track and meeting their goals. This ongoing process of evaluation is essential for maintaining effectiveness and adapting to changing circumstances.