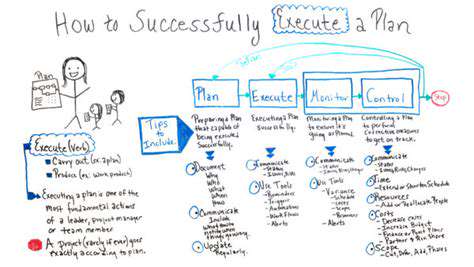
Expanding Awareness Beyond the Basics
Genuine awareness extends far beyond mere recognition; it demands a thorough grasp of context, implications, and potential consequences. Cultivating this depth requires actively pursuing knowledge, engaging in thoughtful analysis, and recognizing the boundaries of our own viewpoints. This proactive stance moves past surface-level understanding, delving into the underlying reasons for phenomena and their ripple effects across our environment.
Cultivating a Holistic Perspective
A comprehensive worldview acknowledges the intricate web of connections between events. It understands that circumstances rarely exist in isolation but rather as components of a vast network of relationships. Recognizing these interdependencies enables us to weigh all contributing factors when assessing situations, leading to more nuanced decision-making.
The Importance of Self-Reflection
Introspection serves as a cornerstone for broadening awareness. By examining our preconceptions, driving forces, and underlying beliefs, we gain insight into how these internal elements shape our interactions. This personal insight forms the foundation for individual development and more meaningful connections with others.
Applying Awareness to Problem-Solving
Enhanced awareness equips us to tackle challenges more effectively. We can examine issues from multiple vantage points, evaluating various solutions and their potential ramifications. This multifaceted approach fosters innovative problem-solving techniques that yield superior results.
The Role of Critical Thinking in Expanding Awareness
Analytical reasoning proves invaluable for deepening understanding. It entails challenging presuppositions, assessing data, and exploring differing viewpoints. Through critical examination, we transcend superficial observations to grasp the complexities inherent in any scenario. This methodical approach refines our comprehension and enables more sophisticated evaluations.
Connecting Awareness to Action
Insight without implementation remains fruitless. We must transform our expanded understanding into tangible initiatives - whether through taking charge, championing transformation, or fostering productive discussions. Through purposeful action, we manifest the practical value of our heightened awareness and drive meaningful progress.
The Continuous Nature of Awareness Expansion
Developing awareness represents an endless journey rather than a final destination. As our environment constantly evolves, we must remain receptive to fresh knowledge and experiences. This commitment to perpetual learning enhances our adaptability, allowing us to navigate our rapidly changing world with greater assurance and competence. Maintaining a growth-oriented perspective remains crucial for sustained awareness development.
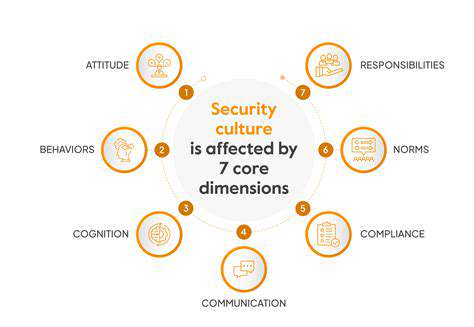
Measuring the Impact and Evaluating Program Effectiveness
Understanding Key Metrics for Supply Chain Cybersecurity
Assessing program efficacy in supply chain cybersecurity demands a comprehensive strategy focused on metrics that reveal the initiative's capacity to detect, address, and counter threats. Establishing well-defined SMART objectives aligned with organizational priorities and risk tolerance creates a solid foundation for evaluation. Numerical indicators like resolved vulnerabilities, reaction times to incidents, and breach-related expenses offer concrete evidence of program performance. Subjective measures, including staff training participation rates and perceived security awareness value, contribute additional perspective on the supply chain's defensive strength.
Monitoring attack frequency and complexity across supply chain tiers helps allocate resources strategically. Periodic evaluations of vendor security postures through penetration testing and vulnerability assessments maintain continuous adaptation to emerging risks. Analyzing resulting data patterns enables refinement of protective measures and strengthens overall supply chain durability.
Evaluating the ROI of Cybersecurity Investments
Determining the financial return on cybersecurity expenditures necessitates comparing implementation costs against potential breach consequences. Calculating possible losses encompassing revenue declines, regulatory penalties, and brand damage enables accurate ROI projections. Detailed risk evaluations ensure security spending aligns with business objectives while supporting informed cost-benefit decisions.
Tracking savings from reduced security events and operational improvements demonstrates cybersecurity value. Comparing prevention costs against incident response expenses, conducted regularly to reflect evolving threats, validates investment rationale. Clear presentation of these findings to leadership ensures continued support for supply chain protection initiatives.
Assessing the Resilience of the Supply Chain
Evaluating cyberattack resistance involves identifying vulnerabilities throughout the entire supply network. Understanding interdependencies proves crucial, as compromises at one level can propagate systemwide. Disruption simulations and response exercises reveal weaknesses while strengthening contingency capabilities.
Comprehensive continuity strategies, regularly updated to match current threats, outline recovery procedures for maintaining operations during crises. Post-incident analyses extract lessons that enhance both response protocols and overall supply chain robustness.
Measuring Compliance with Regulations and Standards
Adherence to frameworks like NIST CSF and ISO 27001 validates program quality while building stakeholder confidence. Routine audits identify security gaps and verify vendor compliance with organizational requirements.
Ongoing monitoring and transparent reporting of conformity status maintain accountability. Implementing continuous improvement processes based on audit outcomes and regulatory changes ensures persistent compliance with evolving standards. This demonstrates unwavering commitment to supply chain security excellence.