Supply Chain Attacks: Compromising the Foundation
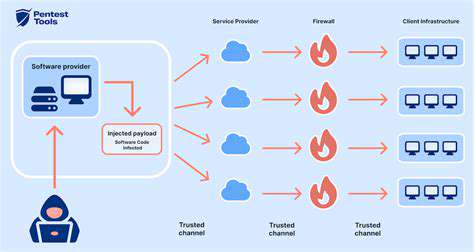
Supply Chain Attacks: A Growing Threat
Supply chain attacks are a significant and evolving cybersecurity threat that leverages vulnerabilities within the complex web of suppliers, manufacturers, and distributors to compromise a target. These attacks often go unnoticed for extended periods, allowing attackers to gain a foothold within a company's systems and infrastructure. The sheer scale and interconnectedness of modern supply chains make them particularly attractive targets for malicious actors. This multifaceted nature of the supply chain creates numerous entry points for attackers to exploit, posing a formidable challenge to organizations seeking to protect their systems and data.
The sophistication of these attacks is also constantly increasing. Attackers are developing increasingly sophisticated methods to compromise systems, often using malware and other malicious code to gain access to sensitive information or disrupt operations. This requires organizations to constantly adapt their security measures and strategies to stay ahead of the curve. The attackers are adapting to the methods of security, making it a continuous process of adaptation and improvement in the cybersecurity space.
Impact of Supply Chain Attacks
The impact of a successful supply chain attack can be devastating, ranging from financial losses to reputational damage and even operational disruptions. Compromised systems can lead to the theft of sensitive data, intellectual property, or financial assets, resulting in significant financial penalties and legal issues. Moreover, the disruption of critical infrastructure or services can have far-reaching consequences, impacting public safety and economic stability.
Beyond the immediate financial and operational costs, supply chain attacks can also inflict substantial reputational damage. The loss of consumer trust and confidence in a company can have long-term consequences, impacting its brand image and market share. This damage can be particularly severe for companies operating in highly regulated industries.
The ripple effects of a supply chain attack can extend far beyond the immediate victim. The interconnected nature of supply chains means that vulnerabilities in one part of the chain can quickly propagate through the entire system, affecting multiple organizations and potentially disrupting entire industries.
Mitigating Supply Chain Risks
Effective mitigation strategies are crucial to reducing the risk of supply chain attacks. This requires a multi-faceted approach that encompasses robust security measures throughout the entire supply chain, from the initial supplier to the final customer. Implementing strong security protocols, conducting regular security assessments, and fostering a culture of security awareness are essential components of an effective defense strategy.
Organizations should prioritize the security of their third-party vendors and suppliers. Conduct thorough due diligence on potential partners, and implement contractual obligations to ensure adherence to agreed-upon security standards. Regular communication and collaboration with supply chain partners are also critical to identifying and addressing potential vulnerabilities in a timely manner.
Beyond these immediate actions, continuous monitoring and adaptation are essential. The threat landscape is constantly evolving, and organizations must remain vigilant to detect and respond to emerging threats and vulnerabilities. Investing in advanced security tools and technologies and fostering a culture of continuous improvement is vital to mitigating the ever-present risk of supply chain attacks.