Data Recovery Options: Restoring Your Valuable Assets
Data Recovery Strategies for Ransomware Attacks
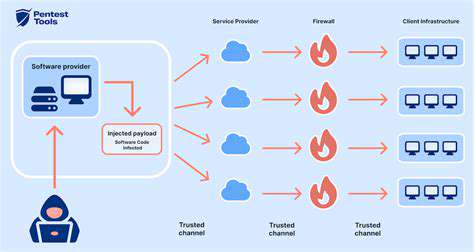
Ransomware attacks are a significant threat to businesses and individuals alike, often leading to the loss of critical data. A robust data recovery strategy is crucial to mitigate the impact of such attacks, ensuring business continuity and minimizing financial losses. This strategy should include proactive measures to prevent infections, as well as well-defined procedures for data restoration in the event of an attack.
Understanding the various attack vectors and implementing strong cybersecurity protocols is paramount. This includes regular software updates, employee training on phishing scams, and robust network security measures to prevent unauthorized access. A layered approach to security is often the most effective.
Backup Solutions for Data Protection
Regular backups are a fundamental aspect of any data recovery strategy. A robust backup system should encompass both off-site and on-site backups to ensure data redundancy. This redundancy is essential in case of a physical disaster or ransomware attack impacting the primary data storage location. Regular testing of backup procedures is equally important to ensure data integrity and the ability to restore data successfully.
Cloud-based backups offer scalability and accessibility but require careful consideration of security protocols. Proper encryption and access controls are critical to safeguard data in the cloud. Hybrid solutions combining cloud and on-site backups often provide the best balance of accessibility and security.
Data Restoration Techniques
Data restoration techniques should be a well-defined part of your ransomware recovery plan, detailing the steps to recover data from backups. The restoration process should be tested regularly to ensure it's efficient and effective. This includes understanding the backup methods, identifying the correct data points to restore, and implementing robust data validation processes to confirm the integrity of the restored data.
Knowing which data to prioritize for restoration is vital. Critical business operations, customer data, and regulatory compliance records should be a top priority. A clear restoration plan should include a process for verifying the integrity of the recovered data and ensuring that the system is free from any malicious remnants of the ransomware attack.
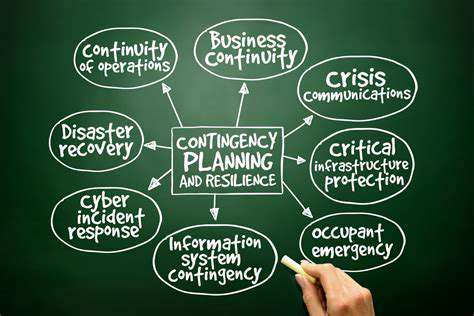
Incident Response and Recovery Plan
A comprehensive incident response plan is essential for managing a ransomware attack effectively. This plan should outline the steps to be taken from initial detection to complete recovery. Identifying key personnel, establishing communication protocols, and documenting procedures are all critical components of a robust incident response plan.
This plan should also detail the roles and responsibilities of various stakeholders. It's crucial to have a clear chain of command and communication channels to streamline the recovery process. Having a dedicated incident response team can significantly enhance the efficiency and effectiveness of the recovery effort.
Legal and Regulatory Considerations
Ransomware attacks often trigger legal and regulatory obligations, especially when sensitive data is involved. Understanding these obligations is critical to ensure compliance and avoid potential penalties. This includes regulatory compliance requirements pertaining to data breach notification, investigation, and recovery, as well as legal implications related to extortion and criminal prosecution. Consulting legal professionals specializing in cybersecurity is highly recommended to ensure compliance with all applicable regulations and legal frameworks.
Implementing data loss prevention and incident response plans in line with regulatory requirements is essential. This can help organizations avoid costly penalties and maintain customer trust. Thorough documentation of all steps taken during the incident response process is crucial for demonstrating compliance and mitigating potential legal issues. Understanding and adhering to legal and regulatory guidelines specific to your industry is vital for managing the ransomware attack and subsequent recovery process.