Improving Incident Response with NLP
Leveraging NLP for Automated Threat Detection
Natural Language Processing (NLP) offers a powerful toolset for automating threat detection in cybersecurity. By analyzing vast quantities of textual data, including security logs, emails, and social media posts, NLP algorithms can identify patterns and anomalies indicative of malicious activity. This automated approach significantly improves the speed and efficiency of incident response, allowing security teams to react to threats proactively rather than reactively.
The ability to sift through massive datasets quickly and accurately is crucial. Traditional methods often struggle with the sheer volume of data generated in modern environments. NLP, with its sophisticated pattern recognition capabilities, can quickly identify suspicious language or unusual communication patterns, flagging potential incidents for further investigation.
Enhancing Security Information and Event Management (SIEM)
Integrating NLP with SIEM systems can significantly enhance their capabilities. Instead of relying solely on predefined rules, NLP can analyze unstructured text within security logs, identifying nuanced indicators of compromise that might be missed by traditional SIEM tools. This deeper understanding of context allows for more accurate threat detection and improved threat intelligence.
This enhanced analysis can translate to faster incident response times and reduced dwell time for attackers. Early detection of malicious activities is paramount to minimizing the damage they can inflict.
Automating Incident Classification and Prioritization
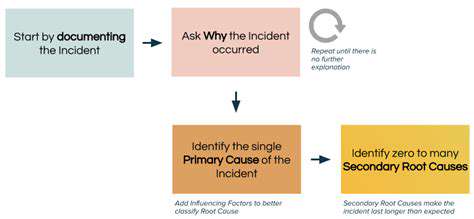
NLP can automate the process of classifying and prioritizing security incidents. Analyzing the textual content of alerts and reports, NLP algorithms can automatically categorize incidents based on severity, impact, and type. This automation streamlines the incident response process, allowing security teams to focus on the most critical issues first.
Prioritization based on NLP analysis is vital for effective incident management. By quickly identifying and prioritizing the most critical incidents, security teams can ensure that resources are allocated appropriately and that the most damaging threats are addressed promptly. This optimized workflow contributes to overall security posture improvement.
Improving Security Awareness Training
NLP can be used to create more engaging and effective security awareness training programs. By analyzing user interactions and feedback, NLP algorithms can personalize training content and tailor it to individual learning styles. This personalized approach can significantly improve the effectiveness of security awareness programs, ultimately reducing the risk of human error in security incidents.
NLP can also help identify and address knowledge gaps in security awareness training. By analyzing the types of questions users ask and the errors they make, NLP can pinpoint areas where additional training is needed. This targeted approach to training is crucial in reducing the risk of phishing attacks and other social engineering attempts.
Extracting Valuable Insights from Threat Intelligence
Threat intelligence is vital for staying ahead of evolving cyber threats. NLP can be used to analyze large volumes of threat intelligence data, identifying patterns, trends, and emerging threats. This analysis allows security teams to proactively adapt their defenses and improve their overall security posture.
NLP algorithms can also translate and summarize threat intelligence from various sources, making it more accessible and actionable for security professionals. This enhanced understanding of threats allows for more informed decision-making, leading to more effective security strategies.
Facilitating Communication and Collaboration
Effective communication and collaboration are critical during incident response. NLP can facilitate these processes by automating the translation of security alerts and reports, making information readily available to relevant personnel, regardless of their language or location. This improved communication fosters better collaboration and quicker resolution of security incidents.
NLP can also assist in identifying key stakeholders and automating communications to them during an incident. This ensures that the right people receive the right information at the right time, contributing to more efficient and effective incident response.
Predictive Modeling for Future Threats
NLP techniques can analyze historical security data, including incident reports, vulnerability reports, and threat intelligence feeds, to identify patterns and predict future threats. Predictive modeling allows security teams to proactively prepare for potential attacks and implement preventative measures before they occur. This approach significantly strengthens the security posture of organizations.
Predictive models developed using NLP can forecast the likelihood and impact of various threats, allowing security teams to prioritize resources and allocate them accordingly. This proactive approach to threat management is critical for staying ahead of cybercriminals and maintaining a robust security infrastructure.