Building a Zero Trust Architecture: Layering Security Controls for Comprehensive Protection
Understanding the Foundation of Zero Trust
A zero trust architecture fundamentally shifts the traditional security paradigm, moving away from the implicit trust granted to users and devices within a network perimeter. Instead, it assumes no implicit trust, verifying every user and device attempting access to resources. This necessitates a layered approach to security controls, implementing continuous authentication and authorization, and granular access policies. This shift is driven by the increasing sophistication of cyber threats and the evolving nature of work, where employees and devices can be located anywhere in the world, potentially outside of the traditional network perimeter.
This foundational shift demands a comprehensive understanding of all users and devices, regardless of their location or network connection. It's crucial to understand that a zero trust architecture is not a one-time implementation but an ongoing process of evaluating and adapting security measures to evolving threats.
Implementing Granular Access Control
A key element of a zero trust architecture is implementing granular access control policies. These policies define precisely what resources each user and device is permitted to access, based on their specific needs and roles. This contrasts sharply with traditional network security models that often grant broad access privileges. This granular control minimizes the impact of a security breach by limiting the potential damage to only the resources directly compromised.
Leveraging Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a critical component of any zero trust strategy. Requiring multiple forms of authentication—such as passwords, security tokens, or biometric data—significantly enhances security by making it harder for unauthorized users to gain access. By implementing MFA across all user logins, including remote access, the organization significantly reduces the risk of successful credential theft and subsequent data breaches. The use of MFA is now widely considered a critical security best practice for any organization.
Utilizing Network Segmentation and Micro-segmentation
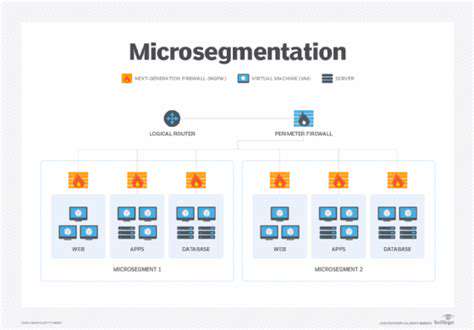
Network segmentation and micro-segmentation play a vital role in isolating sensitive resources and limiting the impact of a security breach. Segmentation divides the network into smaller, isolated segments, making it harder for attackers to traverse the network and reach critical data. Micro-segmentation further refines this approach, segmenting network traffic down to the individual application or server level. This granular control helps confine any potential compromise to a specific segment, protecting sensitive information and applications.
Monitoring and Continuous Security Posture Assessment
A zero trust architecture isn't a static implementation; it requires continuous monitoring and assessment of the security posture. Regular security audits, threat intelligence analysis, and automated security tools are crucial for identifying vulnerabilities and adapting security controls to emerging threats. Continuous monitoring ensures that the architecture remains effective in the face of evolving threats, and allows for rapid response to any identified security incidents. This proactive approach is essential for maintaining a robust and resilient security posture.
The subsurface ocean, a vast and largely unexplored realm beneath the surface, holds secrets about our planet's history and potential for life. This hidden world is a complex and dynamic environment, with unique physical and chemical characteristics that differ significantly from the surface ocean. Understanding these differences is crucial for comprehending the full scope of Earth's oceanic systems.
Implementing and Managing Zero Trust: Continuous Monitoring and Improvement
Understanding the Foundation of Zero Trust
Zero Trust security architecture fundamentally shifts the traditional network security model. Instead of relying on implicit trust within a perimeter, it assumes no implicit trust, verifying every user, device, and application attempting access. This granular approach requires continuous monitoring and assessment to adapt to evolving threats and maintain a secure environment. Understanding the core principles and how they relate to ongoing monitoring is crucial for successful implementation.
Zero Trust security is built on the principle of never trust, always verify. This means that every request, regardless of its source, requires authentication and authorization before access is granted. This contrasts sharply with traditional network security, which often assumes trust within a defined network perimeter.
Continuous Monitoring: The Heart of Zero Trust
Continuous monitoring is essential for a successful Zero Trust deployment. It involves proactively identifying and responding to security threats in real-time, rather than reacting to incidents after they occur. This proactive approach allows organizations to identify vulnerabilities and suspicious activities before they escalate into significant breaches.
Implementing robust monitoring tools and systems is critical. These tools should track user activity, application usage, and device configurations across the entire network. Continuous analysis of this data provides valuable insights into potential threats and anomalous behavior. Real-time monitoring ensures quick detection and response to emerging security risks.
Establishing Baseline Security Profiles
Establishing baseline security profiles for users, devices, and applications is a crucial step in implementing Zero Trust. These profiles define the expected behavior and access permissions for each entity. This baseline is regularly updated to reflect evolving security needs and threats. A robust baseline profile helps in quickly identifying deviations from the norm, signaling potential security breaches.
Baseline security profiles must be regularly reviewed and updated to keep pace with changing security threats and the evolving needs of the organization. This proactive approach helps maintain a dynamic and adaptive security posture that effectively mitigates risks.
Adaptive Response Mechanisms for Evolving Threats
Zero Trust security isn't a static solution; it's a dynamic and adaptive system that needs continuous improvement. Adaptive response mechanisms are essential to handle the ever-changing threat landscape. These mechanisms allow for swift adjustments to security policies and procedures based on real-time threat intelligence and observed behaviors.
Organizations need to implement mechanisms that allow for rapid adjustments to security policies and procedures. This includes automation for responding to threats and adjusting access privileges based on risk assessments. Adapting quickly to new threats and vulnerabilities is critical for maintaining a robust security posture.
Improving and Refining the Zero Trust Posture
Continuous improvement is a cornerstone of Zero Trust security. Regularly assessing the effectiveness of implemented controls and policies, and identifying areas for optimization, is vital. Gathering feedback from users and security teams is crucial for understanding the effectiveness of the Zero Trust implementation and identifying potential areas for improvement.
Regularly auditing and evaluating the security posture against industry best practices and regulatory requirements is key to ensuring compliance and identifying potential weaknesses. Collecting and analyzing security logs, user behavior data, and threat intelligence reports allows for continuous assessment and refinement of the Zero Trust security model.
Embracing the Future of Security: Navigating the Challenges of Zero Trust

Proactive Security Measures
In today's interconnected world, proactive security measures are paramount. Organizations must move beyond reactive strategies and embrace a culture of continuous improvement in their security posture. This involves implementing robust security frameworks, regularly assessing vulnerabilities, and staying ahead of emerging threats.
Proactive measures also include educating employees about cybersecurity best practices. A well-trained workforce is a strong first line of defense against phishing attacks and other social engineering tactics.
Advanced Threat Detection and Response
Advanced threat detection systems are crucial for identifying and mitigating sophisticated cyberattacks. These systems should utilize machine learning and AI to analyze network traffic and user behavior for anomalies, enabling faster response times and minimizing damage.
Implementing a robust incident response plan is vital for effectively managing and containing security breaches. This plan should outline clear procedures for identifying, containing, and recovering from incidents, ensuring minimal disruption and swift recovery.
The Role of Artificial Intelligence
Artificial intelligence (AI) is transforming the security landscape. AI-powered tools can automate tasks, identify patterns, and predict potential threats, significantly enhancing security operations.
AI's ability to analyze vast amounts of data allows for a more comprehensive understanding of potential risks, enabling organizations to proactively address vulnerabilities before they are exploited. This predictive capability is a game-changer in the fight against evolving cyber threats.
Zero Trust Security Architecture
A zero-trust security architecture is a critical component of modern security strategies. This approach assumes no implicit trust, regardless of location or user access level. All users and devices are continuously verified and authorized.
By implementing zero trust, organizations can significantly reduce the attack surface and minimize the impact of compromised accounts or devices.
Multi-Factor Authentication (MFA)
Implementing multi-factor authentication (MFA) is a fundamental security measure that adds an extra layer of protection to user accounts. This prevents unauthorized access even if a username and password are compromised.
Stronger security measures, like MFA, contribute to a significant reduction in the risk of account breaches and data theft. This is an essential step for bolstering overall security posture and protecting sensitive information.
Cybersecurity Awareness Training
Regular cybersecurity awareness training is essential for all employees. This training should cover topics such as phishing awareness, password management, and safe browsing practices.
Employees who are well-versed in cybersecurity best practices are less likely to fall victim to social engineering attacks. This proactive training is a significant investment in protecting the entire organization from cyber threats.
Security Auditing and Compliance
Regular security audits are essential for identifying weaknesses and ensuring compliance with industry standards and regulations. These audits should cover network security, endpoint protection, and data security policies.
Thorough security audits provide valuable insights into the effectiveness of current security measures and help organizations adapt their strategies to meet evolving threats. Staying compliant with regulations is also crucial for maintaining a trustworthy reputation and preventing costly penalties.