Future of XAI in Cybersecurity: Enhanced Security and Collaboration
Explaining the Black Box: Enhancing Cybersecurity Through XAI
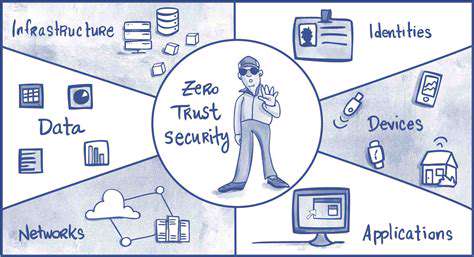
Explainable AI (XAI) is poised to revolutionize cybersecurity by providing transparency and insight into complex machine learning models used in threat detection and response. Currently, many cybersecurity systems rely on black box algorithms, making it difficult to understand why a particular threat was flagged or ignored. This lack of explainability hinders effective incident response, slows down the learning process, and prevents the identification of vulnerabilities in the system itself. XAI techniques can address these challenges by offering clear explanations for model decisions, allowing security teams to understand the reasoning behind alerts and proactively address potential weaknesses.
By demystifying the decision-making process of these models, XAI can foster a deeper understanding of threat patterns and behaviors. This enhanced understanding allows for more accurate threat classification, improved incident response times, and the development of more robust and adaptable security measures. Security professionals will gain a greater understanding of the data used to train these models, allowing them to identify and mitigate biases or inaccuracies that could lead to false positives or missed threats.
Collaborative Security Through Shared XAI Insights
The future of cybersecurity necessitates a collaborative approach, and XAI plays a critical role in facilitating this. By providing clear and concise explanations for security decisions, XAI enables teams across different organizations to share knowledge and best practices. This collaborative environment fosters a more holistic understanding of threats and vulnerabilities, leading to a more effective and coordinated security posture. Sharing insights into the reasoning behind decisions, particularly concerning complex or unusual events, facilitates rapid knowledge transfer and strengthens the collective defense against emerging threats.
Furthermore, XAI enables the sharing of threat intelligence in a more structured and understandable format. This improves the speed and accuracy of threat response, allowing organizations to react more swiftly to emerging threats. By sharing these insights, security teams can leverage a broader range of expertise and data sources, leading to a more comprehensive and effective security strategy. This collaborative approach is crucial in countering the increasingly sophisticated and complex nature of cyber threats in today's interconnected world.
XAI's ability to provide clear explanations for model decisions empowers organizations to build trust within their security systems. This transparency fosters collaboration and knowledge sharing, creating a more resilient and effective cybersecurity ecosystem. By understanding *why* a system flagged a particular event, security teams can better understand the intricate workings of cybersecurity models and improve their ability to anticipate and respond to threats.
The potential for XAI to revolutionize the way security systems are built, operated, and understood is enormous. By providing explainable models, XAI can improve the accuracy and efficiency of threat detection and response, creating a more secure and collaborative cybersecurity landscape.