Key Components of a ZTNA Solution
Zero Trust Network Access (ZTNA) Architecture
Zero Trust Network Access (ZTNA) solutions are built on a fundamentally different security model compared to traditional network security. Instead of assuming trust within the network perimeter, ZTNA solutions verify the identity and authorization of every user, device, and application attempting access, regardless of their location. This granular control ensures that only authorized entities can access specific resources, significantly reducing the attack surface and improving overall security posture. The architecture typically involves a central policy engine, identity and access management (IAM) systems, and a network of secure access gateways.
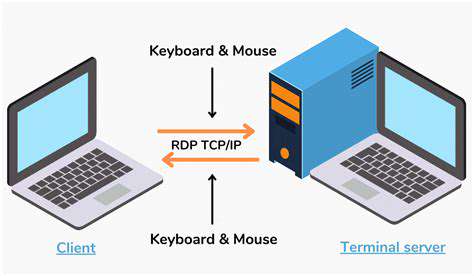
A crucial component of this architecture is the secure access gateway, which acts as a secure intermediary between the user and the network resources. This gateway rigorously validates access requests and enforces security policies defined by the central policy engine. This layered approach to security significantly strengthens the overall defense against unauthorized access attempts.
Identity and Access Management (IAM) Integration
Effective Zero Trust Network Access (ZTNA) relies heavily on robust Identity and Access Management (IAM) systems. ZTNA solutions integrate with existing IAM infrastructures to leverage existing user identities, roles, and permissions. This integration ensures seamless user access while maintaining a granular level of control over who can access what resources. The strong authentication mechanisms within IAM systems are vital for verifying the identity of users and devices attempting to access the network.
Integrating IAM allows for dynamic access control, which is a cornerstone of ZTNA. As user roles and permissions change, the ZTNA solution automatically updates access policies, ensuring that users always have the correct level of access to the resources they need. This adaptability is a critical aspect of a modern, dynamic security environment.
Secure Access Gateways and their Function
Secure access gateways are the frontline of defense in a ZTNA architecture. These gateways act as secure intermediaries between users and the network resources, ensuring that all communications are encrypted and adhering to established security policies. They are responsible for validating user identities, enforcing access controls, and managing the traffic flow between users and the network. Their primary function is to limit the attack surface and prevent unauthorized access to sensitive data and applications.
Furthermore, these gateways often provide advanced security features such as intrusion detection and prevention systems (IDS/IPS), firewall capabilities, and multi-factor authentication (MFA) to further strengthen the security posture. This multi-layered approach ensures a comprehensive defense against various threats.
Policy Enforcement and Management
A robust policy engine is essential for effectively managing and enforcing access policies in a ZTNA environment. This engine defines granular access permissions for users, devices, and applications based on the Zero Trust principles. This includes defining which users have access to specific resources, what actions they can perform, and the times of day they can access them. Policy enforcement ensures that users are only granted the minimum necessary access to complete their tasks.
The policy management aspect of a ZTNA solution allows for easy modification and updates to access policies as business needs evolve. This adaptability is critical for maintaining a secure and efficient network in a dynamic environment, where user roles and access requirements change frequently. Effective policy management ensures that security policies are aligned with the organization's current needs.
Network Segmentation and Micro-segmentation
Network segmentation and micro-segmentation are integral components of ZTNA, enabling a granular level of control over network access. These techniques isolate sensitive resources behind secure access gateways, limiting the impact of a potential breach. Network segmentation divides the network into smaller, isolated segments, allowing for greater control and security over network resources. Micro-segmentation further refines this by segmenting individual servers and applications, providing an even more granular level of access control.
By implementing these segmentation strategies, ZTNA solutions reduce the blast radius of a security incident. If a user or device is compromised, the attacker's access is contained within the specific segment where the breach occurred, thus protecting other critical resources within the network. This is a crucial aspect of achieving the Zero Trust security model.
Evidence of ancient riverbeds and channels on Mars, often appearing as intricate networks of valleys and canyons, strongly suggests the presence of liquid water in the Martian past. These features, observed by various spacecraft, including the Curiosity rover, point to flowing water that carved these channels over vast stretches of time. The channels' complexity, including meandering patterns and the presence of alluvial fans, further supports the theory that liquid water once flowed on the Martian surface, potentially in significant quantities. Understanding these features is crucial to reconstructing the Martian climate and its potential habitability.