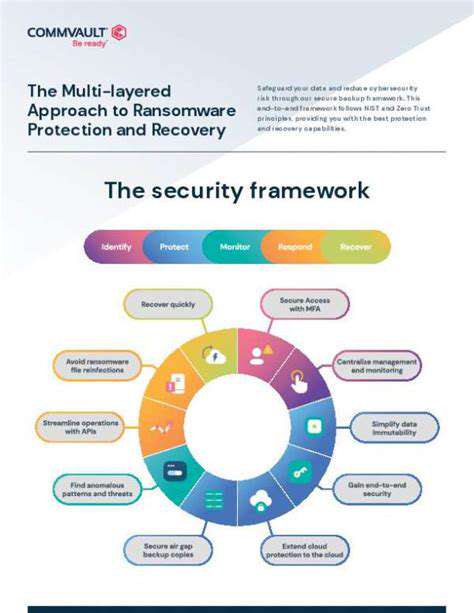
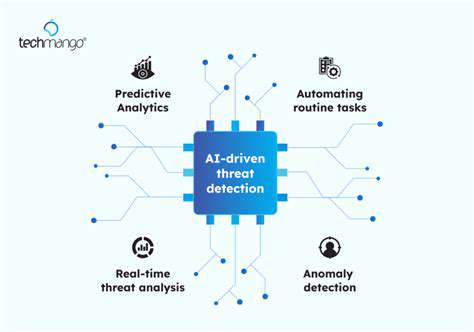
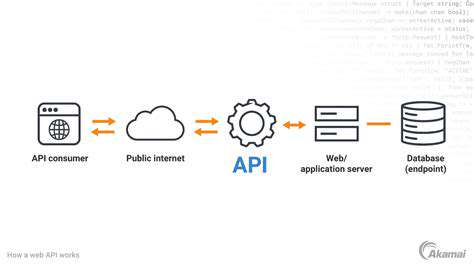
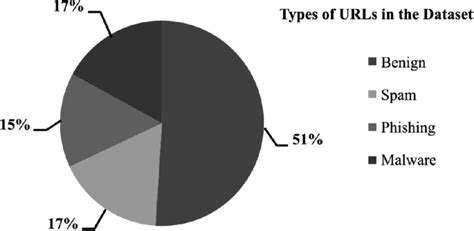
Automated incident response systems are rapidly changing the way organizations approach security threats. These systems leverage sophisticated algorithms and machine learning to proactively identify and respond to security incidents, often before human analysts even notice them. This proactive approach significantly reduces the time to containment and minimizes the potential damage caused by breaches. This speed and efficiency are critical in today's fast-paced digital landscape, where even a brief delay can have severe consequences.
These systems are designed to work around the clock, constantly monitoring network activity and user behavior for anomalies that might indicate malicious activity. They can also automatically trigger predefined response actions, such as quarantining compromised systems or blocking malicious traffic, further enhancing security posture.
Key Benefits of Automated Systems
The advantages of automated incident response systems extend beyond just speed. They enhance the overall security posture of an organization by providing a 24/7 monitoring system. This constant vigilance significantly reduces the likelihood of successful attacks, as potential threats are addressed before they can cause widespread disruption.
Beyond proactive detection, automated systems often provide detailed reporting and analysis of incidents. This allows security teams to understand the root causes of threats, identify patterns, and refine their security strategies over time, making them more resilient to future attacks. This invaluable information leads to more targeted and effective security measures.
The Role of AI and Machine Learning
AI and machine learning are pivotal components in modern automated incident response systems. These technologies enable the systems to learn from past incidents, identify new threats more quickly, and adapt their responses to changing attack vectors. This adaptability is crucial as cybercriminals constantly evolve their tactics.
By learning from historical data, these systems can identify subtle anomalies and deviations from normal behavior, which might be missed by traditional security tools. This ability to anticipate and adapt to new threats is a significant advantage over manual processes.
Integration with Existing Infrastructure
A key consideration for implementing automated incident response systems is their integration with existing security infrastructure. The seamless integration of these systems with existing tools and processes is critical to ensure effective and efficient operation, minimizing disruption to normal business functions. This integration streamlines the entire incident response process and prevents conflicts with existing systems.
Implementing a robust integration strategy allows the system to leverage existing security infrastructure data, making the identification and response to threats even more precise. This synergy significantly improves the overall effectiveness of the security response.
Scalability and Cost-Effectiveness
Automated incident response systems are designed to scale with the growth of an organization. As the network and data infrastructure expands, the system can adapt to handle the increased volume of data and security threats. This scalability is crucial for organizations with rapidly growing needs.
Beyond scalability, these systems often prove cost-effective in the long run. While initial setup costs might be higher, the reduced operational costs associated with faster response times, minimized downtime, and fewer manual interventions often offset these initial investments. This translates to significant long-term savings.
Future Trends in Automated Incident Response
The future of automated incident response systems looks promising, with ongoing advancements in AI, machine learning, and cloud computing further enhancing their capabilities. The integration of these technologies will likely lead to even more sophisticated threat detection and response mechanisms. This will further enhance security posture and reduce the risk of successful attacks.
Expect to see greater automation in threat hunting, incident triage, and remediation. This ongoing evolution will position organizations to better handle the ever-evolving threat landscape in the digital age.