Predictive security modeling is a crucial aspect of modern cybersecurity, focusing on anticipating potential threats and vulnerabilities before they materialize. This proactive approach allows organizations to develop robust defenses tailored to specific risks, rather than reacting to incidents after they occur. By understanding the potential attack vectors and the likely impact of different threats, organizations can prioritize their security investments and allocate resources effectively. This foresight is essential in today's rapidly evolving threat landscape.
The core principle behind predictive security modeling lies in leveraging historical data, current trends, and expert knowledge to create a comprehensive picture of potential future threats. This process involves analyzing various factors, from known vulnerabilities in software to emerging attack techniques and social engineering tactics. Detailed analysis of these factors allows for the creation of accurate threat models, which provide a framework for understanding and mitigating risks.
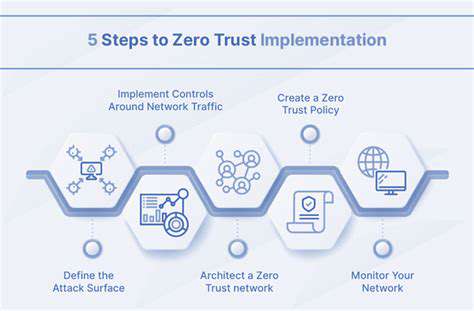
Key Components of a Predictive Model
A robust predictive security model incorporates several key components. These include threat intelligence feeds, vulnerability databases, and security logs. These resources provide valuable insights into the current threat landscape, enabling organizations to identify potential weaknesses and adapt their security strategies accordingly. Effective threat intelligence is paramount in this process, as it provides timely information about emerging threats and attack methods.
Furthermore, the model should include detailed analysis of system dependencies, network topologies, and user behavior. Understanding these components is crucial for identifying potential points of entry for attackers and assessing the potential damage caused by successful exploits. This holistic approach to risk assessment is essential for creating a truly predictive security strategy.
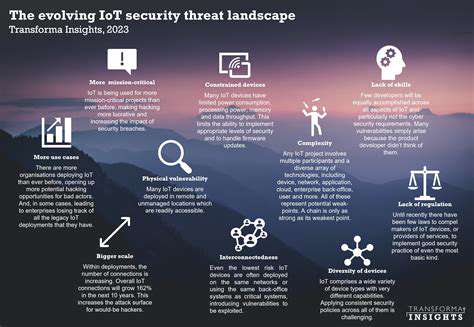
Data Sources and Analysis Techniques
The accuracy of a predictive security model hinges on the quality and quantity of data used for analysis. Organizations must leverage a diverse range of data sources, including security logs, network traffic data, and threat intelligence feeds. Careful filtering and processing of this data are essential to ensure accuracy and prevent false positives, which could lead to unnecessary security alerts and wasted resources. Thorough analysis of this data helps in identifying patterns, anomalies, and potential threats.
Various analysis techniques, such as machine learning algorithms and statistical modeling, can be employed to extract valuable insights from the data. These techniques can identify subtle patterns and anomalies that might be missed by traditional methods, providing a more comprehensive understanding of potential threats. This advanced analysis allows for the development of proactive security measures that are tailored to specific risks, rather than relying on generic security protocols.
Implementing Predictive Security Measures
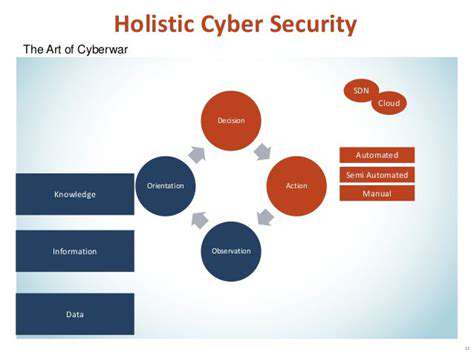
Once a predictive security model is developed, it's crucial to implement the identified security measures. This involves proactive patching of vulnerabilities, implementing intrusion detection and prevention systems, and strengthening access controls. Implementing these measures in a timely manner is critical to mitigating potential risks and protecting sensitive data. The goal is to proactively address potential threats before they can exploit vulnerabilities and cause significant damage.
Continuous monitoring and adjustment of the predictive model are vital for maintaining its effectiveness. Security threats are constantly evolving, and the model must adapt to new developments. Regular updates and adjustments to the model ensure it remains relevant and effective in the ever-changing landscape of cybersecurity threats. This iterative process is a fundamental part of any effective security strategy.
Real-World Applications and Benefits
Predictive security modeling has a wide range of practical applications in various industries. In finance, it can help identify fraudulent transactions and prevent cyberattacks targeting financial institutions. In healthcare, it can help protect patient data and prevent medical device compromises. These real-world applications demonstrate the crucial role that predictive security modeling plays in safeguarding sensitive information and critical infrastructure.
The benefits of implementing predictive security models are numerous. Organizations can reduce the risk of costly security breaches, improve incident response times, and enhance the overall security posture. By anticipating potential threats, organizations can proactively address vulnerabilities, thereby minimizing the potential for financial losses, reputational damage, and operational disruption.