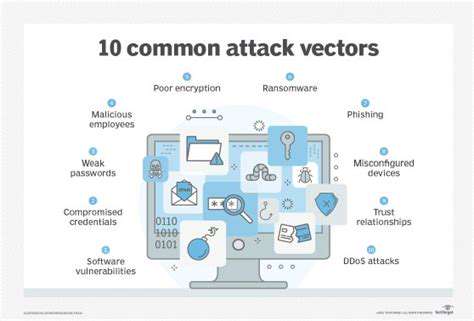
Initial Reconnaissance and Information Gathering
This phase involves systematically gathering information about the target system or network. This initial reconnaissance is crucial for understanding the target's architecture, vulnerabilities, and potential entry points. Gathering information about the target's operating systems, applications, and configurations allows for a more targeted and effective exploitation strategy. We need to determine what systems are running and what services are exposed. It is also important to identify any known vulnerabilities that could be exploited.
Detailed documentation of the findings is essential. This includes notes on discovered services, open ports, and any unusual or unexpected behavior. This documentation forms the basis for the next phases and will be invaluable for tracking progress and ensuring a comprehensive approach to the exploitation process.
Identifying Potential Entry Points
Once reconnaissance has provided a comprehensive overview of the target system, we can start identifying potential entry points. These could be known vulnerabilities in software, misconfigurations, or even weaknesses in the network infrastructure. Thorough analysis is essential to prioritize the most promising vulnerabilities. Careful evaluation allows for a focused approach, maximizing the chances of successful exploitation.
This involves scrutinizing system logs, looking for patterns, and examining the network topology. Understanding how different parts of the system interact is key to finding weaknesses. Identifying potential entry points is critical to minimizing risks and maximizing the effectiveness of the exploitation process.
Exploiting Discovered Vulnerabilities
This phase focuses on leveraging the identified vulnerabilities to gain access to the target system. Exploitation should be carefully planned and executed, with consideration for the potential impact of each action. Careful analysis of the exploit methodology will help ensure that the process remains efficient and minimizes disruption.
The chosen exploit should be carefully evaluated for its potential side effects. This includes considering the impact on the target system's stability and the possibility of triggering alarms or alerting security personnel. Exploiting vulnerabilities requires a nuanced understanding of the target's environment and a commitment to responsible and ethical practices.
Establishing Footholds and Privilege Escalation
Once initial access is gained, the focus shifts to establishing a foothold. This involves gaining control over critical system resources. This is often achieved through exploiting further vulnerabilities within the compromised system or network. This is crucial for maintaining access and enabling further actions.
Privilege escalation is a crucial step in this phase. This involves gaining higher-level access rights to the target system, potentially granting access to sensitive data or administrative functions. This elevation of privileges is essential for achieving the broader objectives of the engagement.
Maintaining Access and Data Exfiltration
Maintaining access to the compromised system is a critical aspect of this phase. This involves establishing persistent access methods, such as backdoors, to ensure continued control. Maintaining access allows for continued actions within the network.
Data exfiltration is the process of extracting valuable data from the compromised system. This could include sensitive information, intellectual property, or financial data. Effective data exfiltration methods are vital for the success of the overall operation. Careful consideration must be given to the methods used to ensure stealth and avoid detection. This phase also requires a secure and reliable method to transmit the extracted information.
Phase 3: Lateral Movement and Privilege Escalation
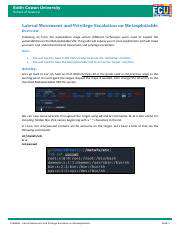
Lateral Movement Techniques
Lateral movement is a critical stage in a cyberattack, enabling attackers to traverse the network beyond their initial point of compromise. This phase often involves exploiting vulnerabilities in legitimate network services to gain access to other systems and data. Understanding the network architecture and identifying potential access points are crucial steps in this process. Attackers frequently use legitimate tools and protocols to move laterally, making detection challenging.
Various methods are employed, including password spraying, exploiting misconfigured services, and leveraging compromised credentials. Attackers may also use internal tools and scripts to automate the process, further complicating security monitoring efforts. A strong understanding of the network's structure and the behaviors of legitimate users is essential for preventing lateral movement.
Privilege Escalation Tactics
Privilege escalation is a common goal in lateral movement, enabling attackers to gain higher-level access to systems and resources. This often involves exploiting vulnerabilities in applications or operating systems to elevate privileges. Successful privilege escalation allows the attacker to access sensitive data and potentially execute malicious code with broader system control.
Techniques employed include exploiting known vulnerabilities, using weak passwords, or even manipulating configuration files to gain elevated privileges. Identifying and mitigating these risks through proactive security measures is crucial in preventing further damage.
Identifying Vulnerable Systems
Identifying vulnerable systems within the network is paramount for preventing lateral movement. Security tools and processes designed to proactively identify potential weaknesses are critical. This includes vulnerability scanning tools, network monitoring systems, and penetration testing exercises. Regular security audits and penetration testing are essential to assess the effectiveness of security controls and identify vulnerabilities.
Thorough inventory management of systems and applications is a critical prerequisite to identifying and mitigating any vulnerabilities that might be present. Without a complete understanding of the IT environment, effective vulnerability assessment and remediation efforts are impossible.
Exploiting Misconfigurations
Many security breaches stem from misconfigurations in systems and applications. Attackers often leverage these misconfigurations to gain unauthorized access. Common misconfigurations include open ports, default credentials, and insecure protocols. Proactively addressing these misconfigurations through regular security audits and configuration hardening is essential for robust security.
Implementing strong security policies and procedures, coupled with automated configuration management tools, can help significantly reduce the risk of misconfigurations. Regular security assessments and penetration testing can also identify and address these vulnerabilities.
Using Compromised Accounts
Exploiting compromised user accounts is a common method for lateral movement. Once an attacker gains access to a user account, they can use that account to access other systems and resources within the network. This often involves using legitimate tools and credentials to move around the network.
This method underscores the importance of strong password policies, multi-factor authentication, and regular account reviews. Monitoring user activity and detecting unusual login attempts is crucial for early detection of compromised accounts.
Data Exfiltration Techniques
After gaining access and control, attackers often exfiltrate data. Methods include copying files to removable devices, transferring data over network shares, or using cloud storage services. Understanding the data exfiltration pathways and implementing security controls to monitor these activities is crucial for data protection.
Implementing robust data loss prevention (DLP) solutions, monitoring network traffic for suspicious activity, and employing encryption techniques can help to mitigate data exfiltration threats.
Network Segmentation Strategies
Network segmentation is a crucial defensive measure against lateral movement. By isolating critical systems and data, attackers are prevented from easily traversing the network. Implementing network segmentation strategies limits the scope of an attack and can contain the damage caused by a compromise.
This often involves creating separate network segments and using firewalls and other security controls to restrict communication between them. Thorough planning and implementation of these strategies are essential to maintain network security.
Phase 4: Installation and Deployment
Initial Setup and Configuration
This phase involves the crucial initial steps of setting up the necessary infrastructure for the deployment. Careful planning and execution in this stage are paramount to a smooth and efficient installation process. Thorough testing of the environment prior to deployment is highly recommended to identify and rectify any potential issues. This includes verifying network connectivity, resource allocation, and compatibility with existing systems. Ensuring all required software components are correctly installed and configured is essential for a successful deployment.
Specific configurations, such as database credentials and API keys, should be securely managed and documented. Implementing robust security measures from the outset is critical for safeguarding sensitive data and preventing unauthorized access. This includes utilizing strong passwords, implementing access controls, and regular security audits. Detailed documentation of the configuration process and all related parameters will be invaluable for future maintenance and troubleshooting.
Deployment Strategies and Monitoring
Several deployment strategies can be employed, ranging from simple file transfers to more complex containerization techniques. The optimal approach depends on the specific project requirements and the existing infrastructure. Careful consideration should be given to the potential impact of the deployment on existing systems and users.
Post-deployment monitoring is essential for ensuring the system functions as expected. This involves tracking key performance indicators (KPIs) such as response times, error rates, and resource utilization. Regular monitoring allows for proactive identification and resolution of potential problems, preventing service disruptions and ensuring optimal performance. Alerting mechanisms should be established to notify relevant personnel of any critical issues or anomalies. Detailed logs and reporting mechanisms should be incorporated to facilitate the analysis of system behavior and identify trends.
Deployment should be approached methodically, adhering to a well-defined plan. This plan should encompass all aspects of the deployment process, from initial setup to ongoing monitoring. Properly documented procedures are crucial for smooth execution and future reference.
Implementing rollback strategies is a crucial element of any deployment process. Having a clear plan for reverting to previous versions in case of issues is critical. These strategies should be well-rehearsed and tested to ensure they can be executed effectively in a crisis situation. This preparedness minimizes the impact of unexpected problems and allows for a rapid recovery.
A well-defined testing strategy should also be incorporated into the deployment process, ensuring that the system is thoroughly vetted before it's released to production. This testing will help identify any potential bugs or issues before they impact users.
Phase 5: Data Exfiltration and Extortion
Data Exfiltration Methods
Data exfiltration is a crucial component of the ransomware attack lifecycle, enabling attackers to steal sensitive information before encrypting it. This stolen data can be used for various purposes, including blackmail, sale on the dark web, or disruption of operations. Attackers employ a range of sophisticated techniques to exfiltrate data, often leveraging legitimate network pathways and tools to mask their activities. This phase may involve copying data to cloud storage, using VPNs to tunnel data to remote servers, or exploiting vulnerabilities in file-sharing systems. Understanding these methods is essential for proactively defending against exfiltration attempts.
Several tools and methods are used by attackers to exfiltrate data during this phase of the attack. These tools are often disguised as legitimate software or processes, making detection challenging. Attackers may also leverage compromised accounts or credentials to gain access to sensitive data and transfer it to their chosen destinations. Staying vigilant about unusual network activity and scrutinizing access logs is vital to thwarting exfiltration attempts.
Extortion Tactics
Once the data is exfiltrated, the attackers typically engage in extortion tactics, leveraging the stolen data to demand payment for its return or to prevent its public release. This can involve threatening to expose sensitive data, leak it to competitor companies, or threaten to disrupt business operations. The extortion phase is often accompanied by a countdown timer to heighten the sense of urgency and pressure on the victim to comply with the attacker's demands.
The nature of the extortion tactics employed can vary significantly. Some attackers might threaten to publicly release the data, while others might demand payment to prevent the release or to promise not to release it at all. The attackers' motivations and the nature of the stolen data play a significant role in determining the specific extortion tactics employed.
Impact on Business Operations
The exfiltration and extortion phase of a ransomware attack can have a devastating impact on business operations. The loss of sensitive data can lead to reputational damage, regulatory fines, and legal liabilities. The disruption caused by the extortion demands can also lead to significant financial losses and operational inefficiencies. The pressure to pay the ransom to prevent data exposure or damage can also lead to a cascade of negative consequences.
Financial Motivations and Payouts
Understanding the financial motivations behind ransomware attacks is crucial to comprehending the exfiltration and extortion phase. Attackers often calculate the potential financial gains from extorting victims, taking into account factors like the value of the stolen data, the victim's financial capacity, and the potential for repeat attacks. The ransom demands are often set based on these assessments. The payout amounts can vary significantly depending on the victim's financial resources, the nature of the stolen data, and the attacker's perceived leverage.
Legal and Regulatory Considerations
The exfiltration and extortion phase of ransomware attacks raises significant legal and regulatory concerns. Organizations must comply with data privacy regulations, such as GDPR or CCPA, and take appropriate steps to protect sensitive data. Failure to comply with these regulations can lead to substantial penalties and legal liabilities. Furthermore, organizations must consider the legal ramifications of paying ransoms, which can be considered illegal in some jurisdictions or could be seen as encouraging further attacks.
Mitigating the Risk of Data Loss
Implementing robust security measures is crucial for mitigating the risk of data loss during the exfiltration and extortion phase. This includes implementing strong access controls, regularly updating security software, and employing robust data encryption protocols. Regular security audits and penetration testing can help identify vulnerabilities and address potential risks. Furthermore, establishing clear incident response plans can help organizations effectively manage and mitigate the impact of a ransomware attack.
Preventing Extortion and Data Leaks
Preventing data exfiltration and extortion attempts requires a multi-faceted approach that goes beyond technical solutions. Organizations should foster a strong security culture, training employees on recognizing and reporting suspicious activities. Proactive security measures, such as regular security awareness training, incident response planning, and robust data backup and recovery strategies, are essential to limit the impact of a successful attack. By taking a proactive approach, organizations can significantly reduce their vulnerability to ransomware attacks.