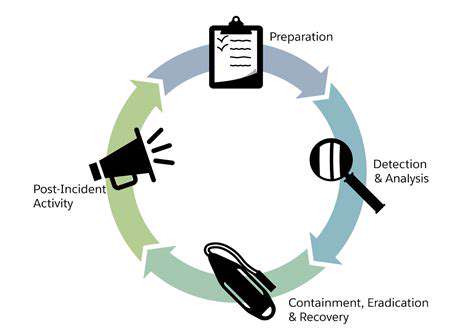
Post-Incident Analysis: Understanding the Breach
A thorough post-incident review is crucial for understanding how a ransomware attack compromised your system. This involves meticulously examining the attack vector, the specific vulnerabilities exploited, and the chain of events that led to data encryption. Analyzing logs, security monitoring data, and internal communications is vital to pinpoint the weak points in your security posture. This analysis should involve both technical experts and business stakeholders to gain a comprehensive understanding of the impact beyond the immediate technical aspects.
Understanding the attackers' tactics, techniques, and procedures (TTPs) is equally important. This knowledge helps to refine security measures and predict future attack patterns. Identifying the specific tools and techniques employed by the attackers provides valuable insights for bolstering defenses and minimizing the risk of similar incidents in the future.
Identifying Vulnerabilities and Weaknesses
The post-incident review should meticulously identify all vulnerabilities that were exploited. This process includes examining software versions, configurations, and security controls. Did a known vulnerability exist in outdated software? Were critical security patches applied in a timely manner? This is not just about technical weaknesses but also includes reviewing user access controls, policies, and procedures. Were employees adequately trained on security best practices, and were those policies enforced consistently?
Analyzing the interplay between different systems and applications is also vital. Identifying the points of entry for the attackers and their movement through the network is critical. Did the attackers exploit a misconfigured firewall, a weak password, or an insecure remote access point? This analysis requires a comprehensive understanding of your network architecture and its security posture.
Implementing Remediation Measures
Based on the findings of the post-incident review, immediate remediation measures must be implemented to prevent future attacks. These measures should prioritize patching vulnerabilities, strengthening access controls, and improving user awareness training. This should involve a multi-layered approach to security including not only technical measures but also organizational changes to improve security culture and awareness.
Strengthening security protocols is paramount. This includes updating antivirus software, implementing intrusion detection systems, and implementing robust data backup and recovery procedures. The remediation process should also include a thorough review of existing security policies and procedures to ensure they are up to date and effective.
Strengthening Security Controls and Procedures
This phase goes beyond simply patching vulnerabilities. It necessitates a comprehensive review and update of security policies, procedures, and controls. Ensuring that all employees understand and adhere to these policies is crucial. This includes regular security awareness training to educate users about phishing attempts, suspicious emails, and other social engineering tactics. Regular security audits and penetration testing should also be incorporated to proactively identify and address potential vulnerabilities.
Improving Incident Response Capabilities
A robust incident response plan is critical for mitigating the impact of future attacks. This plan should outline clear roles and responsibilities for handling security incidents. Regularly testing and updating this plan is essential to ensure its effectiveness. This process should include simulating ransomware attacks to test the preparedness of the team and the effectiveness of the incident response plan.
Establishing communication protocols and channels is essential for quick and effective response during a security incident. This includes determining how to communicate with affected parties, law enforcement, and the media. Practicing these procedures through drills and simulations will improve the efficiency of the response team in a real-world scenario.
Building a Culture of Security
A strong security posture isn't just about technology; it's about fostering a culture of security awareness and vigilance within the entire organization. This involves educating employees about cybersecurity threats, promoting responsible online behavior, and encouraging reporting of suspicious activities. Regular security awareness training sessions and interactive workshops are essential to keep users informed and empowered to recognize and report potential risks.
Open communication about security incidents and vulnerabilities, without fear of retribution, is vital. This creates a safe space for employees to raise concerns and contribute to a more robust security environment. Fostering a culture of security is an ongoing process that requires consistent effort and commitment from all members of the organization.
5. Legal and Communication Considerations: Navigating the Aftermath
Legal Ramifications of Ransomware Attacks
Understanding the legal implications of a ransomware attack is crucial. This encompasses not only potential criminal charges for the attackers but also significant civil liabilities for the victim organization. Legal repercussions can range from data breach lawsuits to regulatory fines, depending on the nature of the attack and the jurisdiction involved. Organizations must be prepared to document the incident thoroughly and consult with legal counsel to navigate these complexities effectively.
Furthermore, the legal landscape surrounding ransomware is constantly evolving, with new laws and regulations emerging regularly. Staying informed about these developments is essential to ensure compliance and minimize potential legal risks.
Communication Strategies for Public Relations
Effective communication is paramount during and after a ransomware attack. Transparency and honesty with stakeholders, including employees, customers, and the public, are critical. A well-defined communication plan should outline how to address the incident, explain the impact, and reassure affected parties. This includes proactive measures to address misinformation and speculation.
Internal Communication Protocols for Employees
Clear and concise internal communication protocols are vital for maintaining order and productivity amidst a ransomware attack. These protocols should outline procedures for reporting suspicious activity, accessing secure communication channels, and following established guidelines for handling sensitive information. Employee training on cybersecurity best practices and incident response procedures is also critical.
External Communication with Customers and Partners
Maintaining open communication with customers and partners is essential for mitigating reputational damage and fostering trust. A timely and transparent communication strategy can help manage anxieties, explain the impact of the attack, and outline steps being taken to restore services. This includes acknowledging the disruption and providing updates on the situation.
Negotiating with Ransomware Attackers
Negotiating with ransomware attackers requires careful consideration and strategic planning. Organizations need to weigh the potential risks and benefits of paying the ransom, including the possibility of future attacks and the potential for data recovery. Legal and security advisors must be consulted to ensure a thorough understanding of the situation and to develop a comprehensive negotiation strategy.
Incident Response Plan and Documentation
A robust incident response plan is crucial for minimizing the impact of a ransomware attack. This plan should outline clear steps for containment, eradication, and recovery. Thorough documentation of the incident, including the timeline, affected systems, and communication efforts, is essential for legal and insurance purposes. This documentation should also serve as a valuable learning experience to prevent future incidents.
Regulatory Compliance and Reporting
Understanding and adhering to relevant regulatory compliance requirements is essential to avoid severe penalties. Organizations must comply with data breach notification laws and other applicable regulations, ensuring timely and accurate reporting of the incident. Failure to comply with these regulations can lead to significant financial penalties and reputational damage.