Post-Incident Recovery and Lessons Learned
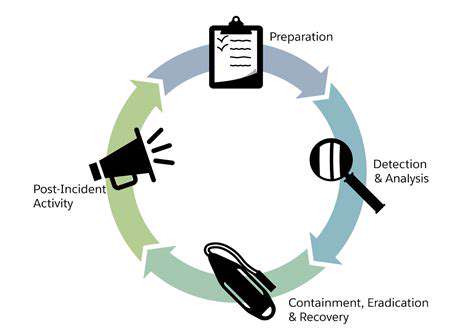
Post-Incident Assessment and Documentation
A thorough post-incident assessment is crucial for understanding the root causes of the event and preventing similar occurrences in the future. This involves a detailed review of all aspects of the incident, including the sequence of events, the impact on individuals and systems, and the effectiveness of existing response procedures. A documented record of the entire incident, including witness statements, system logs, and evidence collected, is essential for a comprehensive investigation and future reference. This documentation forms the basis for identifying weaknesses in processes and procedures, and ultimately, for implementing necessary improvements.
Critically evaluating the effectiveness of existing recovery protocols is vital. This includes examining the response time, the adequacy of resources, and the communication channels used during the incident. By identifying areas of improvement and gaps in the current procedures, organizations can proactively strengthen their resilience and preparedness for future incidents. This assessment should include a review of the incident response plan, identifying any critical gaps or deficiencies that need attention.
Resource Allocation and Prioritization
Effective resource allocation is paramount to a successful post-incident recovery. This involves evaluating the financial, human, and technological resources required to address the immediate needs and long-term implications of the incident. Prioritization is crucial, focusing on critical systems and functions that are essential for maintaining business continuity and minimizing further disruption. Prioritizing resources in this manner ensures that critical operations are restored swiftly, minimizing the overall impact of the incident.
Assessing the availability and suitability of various resources, including personnel, equipment, and financial aid, is an integral part of the process. This assessment should consider the potential long-term needs of the organization, as well as the immediate needs. This proactive approach to resource allocation helps to ensure a smooth and efficient recovery process.
Communication and Stakeholder Management
Maintaining effective communication with all stakeholders, including employees, customers, and regulatory bodies, is essential during the post-incident recovery phase. Open and transparent communication helps manage expectations, build trust, and ensure a smooth transition back to normal operations. Prompt and accurate communication builds confidence and minimizes the potential for misinformation and speculation. This includes providing updates on the recovery progress, outlining the steps being taken, and addressing any concerns that stakeholders may have.
Identifying and engaging key stakeholders is important. This includes internal teams, external partners, and regulatory bodies, if applicable. Developing a communication strategy that addresses the specific needs of each stakeholder group is crucial for ensuring that information is delivered effectively and efficiently.
Lessons Learned and Future Prevention
A critical aspect of post-incident recovery is identifying lessons learned from the event. This involves analyzing the root causes of the incident, evaluating the effectiveness of response procedures, and determining what could have been done differently to mitigate the impact. By understanding the root causes, organizations can proactively implement changes to prevent future incidents of a similar nature. This may involve updating existing policies and procedures, implementing new security measures, or enhancing training programs.
Implementing preventive measures is crucial to prevent future incidents. This could involve a variety of strategies, such as strengthening security protocols, improving incident response plans, conducting regular risk assessments, and enhancing employee training. These actions help to build a more resilient organization, better equipped to handle future challenges and emergencies.