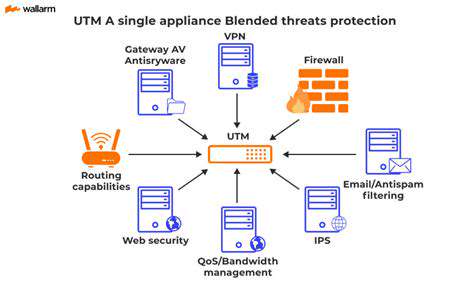
Network Infrastructure: The Unsung Hero
Network infrastructure, often hidden behind the scenes, plays a critical role in enabling seamless communication and data transfer. From the humble Ethernet cable to sophisticated fiber optic networks, these physical components form the backbone of any successful digital operation. Understanding and maintaining this infrastructure is paramount for reliable performance and security. This includes ensuring optimal bandwidth capacity to handle increasing data demands and implementing robust security measures to prevent unauthorized access.
Modern networks are complex systems, demanding careful planning and implementation. Careful consideration needs to be given to the scalability of the network to accommodate future growth. Furthermore, the choice of network architecture significantly impacts performance, reliability, and cost-effectiveness.
Security Considerations
Security is a critical concern in any network environment. Cyber threats are constantly evolving, demanding proactive measures to protect sensitive data and maintain system integrity. Implementing robust firewalls, intrusion detection systems, and regular security audits are essential components of a strong security posture. These measures, combined with employee training on security best practices, help mitigate potential vulnerabilities and protect against data breaches.
Data encryption and access controls are also vital components of a secure network. Implementing strong encryption protocols for sensitive data transmission is a critical step in protecting confidential information. Restricting access based on user roles and responsibilities is another crucial aspect of network security.
Network Management and Optimization
Effective network management is crucial for maintaining optimal performance and stability. This involves continuously monitoring network traffic, identifying bottlenecks, and proactively addressing potential issues. Regular performance assessments help identify and resolve performance problems before they significantly impact users. This also includes monitoring resource utilization to ensure that network resources are allocated efficiently.
Proactive management strategies are key to ensuring the network can adapt to changing demands. This requires implementing automated monitoring tools and developing well-defined troubleshooting procedures. Regular maintenance and upgrades are also necessary to ensure that the network remains reliable and efficient.
Future Trends and Innovations
The future of networking is poised for significant advancements, driven by emerging technologies and evolving user demands. The rise of cloud computing, IoT devices, and big data is placing increasing demands on network infrastructure, requiring greater bandwidth capacity and enhanced security protocols. Cloud-based network management tools and automation are transforming how networks are managed and maintained. These innovations are paving the way for more flexible, scalable, and intelligent network architectures.
The integration of artificial intelligence into network management is another exciting trend. AI algorithms can analyze network data in real-time, enabling predictive maintenance and automated troubleshooting. This will lead to significant improvements in network efficiency and reliability.
Artificial intelligence (AI) is rapidly transforming the field of medical diagnostics, offering the potential for faster, more accurate, and more accessible diagnoses. AI algorithms can analyze vast amounts of medical data, including images, lab results, and patient history, to identify patterns and anomalies that might be missed by human clinicians. This capability is particularly valuable in areas like radiology, where AI can assist in detecting subtle signs of diseases like cancer or cardiovascular problems.
The Future of IoT Security: A Collaborative Effort

The Evolving Threat Landscape
The Internet of Things (IoT) is rapidly expanding, connecting billions of devices to the global network. This interconnectedness, while offering numerous benefits, also presents significant security vulnerabilities. The threat landscape is constantly evolving, with new attack vectors and sophisticated malware emerging at an alarming rate. This necessitates a proactive and adaptable approach to IoT security.
Attackers are increasingly targeting IoT devices, not just for data breaches but also for disrupting services and causing physical harm. The potential impact of successful attacks on critical infrastructure, such as smart grids or medical devices, is enormous, highlighting the urgent need for robust security measures.
Addressing the Device-Specific Challenges
Many IoT devices are manufactured with limited processing power and memory, making them particularly vulnerable to simple attacks. This often leads to the use of weak or default passwords, easily exploited by malicious actors. Security features are sometimes overlooked or poorly implemented during the design and development phases of these devices.
Furthermore, the diverse range of IoT devices, from smart home appliances to industrial sensors, creates a complex security problem. There's no single solution that effectively addresses all these varied vulnerabilities.
The Importance of Secure Data Transmission
Protecting the data transmitted between IoT devices and the cloud is crucial. Data encryption and secure communication protocols are essential to prevent unauthorized access and eavesdropping. Weak or outdated protocols can expose sensitive information, potentially leading to identity theft or financial fraud. Robust encryption methods are needed to safeguard the integrity and confidentiality of data throughout its lifecycle.
Furthermore, ensuring secure communication channels between devices is critical. This includes using strong authentication mechanisms, secure protocols, and regular security updates to keep communication pathways protected.
The Role of AI and Machine Learning
Artificial intelligence (AI) and machine learning (ML) can play a significant role in enhancing IoT security. AI algorithms can detect anomalies and potential threats in real-time, enabling swift responses to emerging vulnerabilities. This proactive approach can significantly reduce the risk of successful attacks.
Machine learning models can be trained to identify patterns of malicious activity, allowing for the detection of sophisticated attacks that might evade traditional security measures. This approach has the potential to enhance the overall security posture of the IoT ecosystem.
The Need for Collaboration and Standardization
Addressing the security challenges of the IoT requires a collaborative effort among manufacturers, developers, and users. Standardization of security protocols and best practices is essential to ensure interoperability and a common framework for security across different IoT devices and systems. Open communication and knowledge sharing are critical to fostering a secure IoT environment.
Collaboration between industries, research institutions, and regulatory bodies is crucial to develop and implement security standards that address the unique vulnerabilities of IoT systems. This multifaceted approach is essential for creating a robust and resilient IoT ecosystem that is secure and trustworthy.