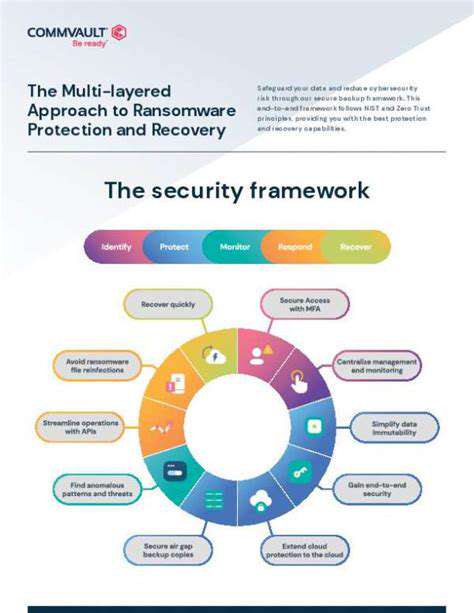
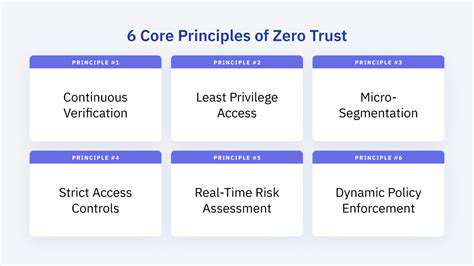
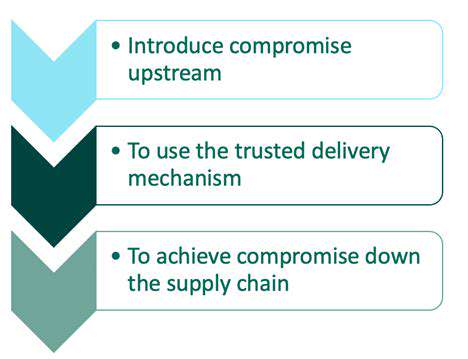
Case Studies: Real-World Examples of Supply Chain Compromises
The Impact of AI on Customer Service
Artificial intelligence (AI) is rapidly transforming the customer service landscape. AI-powered chatbots are becoming increasingly sophisticated, capable of handling a wider range of customer inquiries and providing immediate support. This automation frees up human agents to focus on more complex issues, leading to improved efficiency and faster resolution times. Companies are seeing significant cost savings and improved customer satisfaction as a result.
These AI-driven systems can analyze vast amounts of customer data to identify trends and patterns, allowing businesses to tailor their service offerings and address customer needs more effectively. The ability to personalize interactions and provide proactive support is a key benefit, fostering stronger customer relationships.
Supply Chain Optimization with Machine Learning
Machine learning algorithms are proving invaluable in optimizing complex supply chains. By analyzing historical data and real-time information, these algorithms can predict potential disruptions, such as delays in shipments or unexpected demand spikes. This predictive capability allows companies to proactively adjust their strategies and mitigate risks, ultimately improving efficiency and reducing costs.
Furthermore, machine learning can help optimize inventory management, ensuring that the right products are in the right place at the right time. By reducing waste and improving forecasting accuracy, businesses can significantly improve their bottom line.
Personalized Marketing Campaigns Using Data Analytics
Data analytics plays a crucial role in creating targeted and effective marketing campaigns. By analyzing customer data, businesses can gain insights into customer preferences, behaviors, and demographics. This allows for the development of personalized marketing strategies that resonate with individual customers, leading to increased engagement and conversions.
This data-driven approach allows marketers to tailor messaging and offers to specific segments of their customer base. Companies can optimize their marketing spend by focusing their efforts on the most promising customer segments, resulting in higher ROI.
Fraud Detection in Financial Institutions
Financial institutions are leveraging machine learning algorithms to detect and prevent fraudulent activities. These algorithms can identify subtle patterns and anomalies in transaction data that might be missed by traditional methods. Early detection of fraudulent transactions is crucial in minimizing losses and maintaining customer trust.
Predictive Maintenance in Manufacturing
Predictive maintenance is transforming manufacturing operations by enabling proactive maintenance scheduling. By analyzing sensor data from machinery, machine learning algorithms can predict when equipment is likely to fail. This allows for preventative maintenance to be performed before a breakdown occurs, minimizing downtime and maximizing equipment lifespan.
The reduced downtime translates directly into increased productivity and cost savings for manufacturers. This approach is not just about maintenance, it's about optimizing the entire production process through proactive measures.
Improving Healthcare Outcomes through AI
AI is revolutionizing healthcare, providing valuable tools for diagnosis, treatment, and patient care. AI algorithms can analyze medical images and patient data to assist in early disease detection and diagnosis, which can significantly improve patient outcomes. This capability has the potential to save lives and improve the efficiency of healthcare systems.
Enhancing Customer Experience with Natural Language Processing
Natural Language Processing (NLP) is enhancing customer experiences by enabling more natural and intuitive interactions. Chatbots and virtual assistants are increasingly capable of understanding and responding to complex customer inquiries in a human-like manner. This leads to improved customer satisfaction and increased efficiency in resolving issues. This technology is evolving rapidly and promises to further streamline customer service interactions in the future.
Pierogi, those delightful pockets of dough filled with savory or sweet treasures, hold a rich history deeply woven into the fabric of Polish culture. Dating back centuries, these culinary creations have evolved from humble beginnings, reflecting the diverse influences that shaped Polish society. Their origins are often traced to the ancient Slavic peoples, who developed techniques for creating filled pastries. The pierogi's journey through time has seen variations in fillings and preparation methods, but the core concept of a handcrafted, wholesome food remains constant. They're more than just a meal; they're a cultural touchstone.
Building Resilience: Fostering a Culture of Security
Understanding the Threat Landscape
Software supply chain attacks are a growing concern in the digital age, targeting vulnerabilities within the intricate network of software development, distribution, and deployment. These attacks leverage the trust inherent in this process to introduce malicious code, often undetected, into legitimate software packages. This poses a significant risk to organizations and individuals, with potential consequences ranging from data breaches to system compromise and financial losses.
Recognizing the diverse tactics employed by attackers, from compromising open-source libraries to manipulating package repositories, is crucial in developing effective defensive strategies. Understanding the specific threat landscape and the potential entry points is paramount in proactively mitigating these risks.
Building Secure Software Development Practices
Robust security practices are essential from the initial design phase. Implementing secure coding standards, rigorous code reviews, and thorough penetration testing throughout the development lifecycle can significantly reduce the potential for vulnerabilities. Effective security awareness training for developers is equally important, fostering a proactive mindset towards identifying and mitigating potential threats.
Implementing Secure Software Supply Chain Management
A robust software supply chain management process is crucial. This includes scrutinizing all components and dependencies, verifying their origin and authenticity. Establishing clear policies and procedures for handling updates and patches is vital, ensuring that all parties involved understand and comply with security protocols. This comprehensive approach can greatly reduce the risk of malicious code infiltration.
Establishing Secure Communication Channels
Establishing secure communication channels between software developers, vendors, and users is vital. Encrypting communication channels and using secure authentication protocols can prevent unauthorized access and manipulation of software components. Implementing measures to verify the identity of all parties involved in the supply chain is essential for preventing malicious actors from infiltrating the process.
Proactive Monitoring and Response
Continuous monitoring of the software supply chain is critical. Implementing automated tools to detect anomalies and suspicious activities can help in identifying and addressing potential vulnerabilities early on. Having a well-defined incident response plan in place is essential for swiftly addressing any security breaches and minimizing their impact. Proactive monitoring and swift response are crucial to maintaining a secure and resilient software ecosystem.
Fostering Collaboration and Information Sharing
Collaboration among stakeholders is key to building a resilient software supply chain. Sharing best practices, threat intelligence, and vulnerability reports can strengthen collective security. Open communication channels and collaborative efforts are crucial to effectively address emerging threats and proactively defend against potential attacks. This shared knowledge fosters a culture of security awareness and proactive threat mitigation.