Implementing and Maintaining Effective Cybersecurity Controls
Understanding the Criticality of Supply Chain Cybersecurity
Protecting your organization's supply chain from cyber threats is paramount in today's interconnected digital landscape. A breach in a supplier's system can have cascading effects, compromising sensitive data, disrupting operations, and eroding public trust. The interconnected nature of modern supply chains means that vulnerabilities in one part of the chain can quickly propagate throughout, making proactive cybersecurity measures essential for mitigating risks and ensuring business continuity.
A robust cybersecurity strategy for your supply chain must go beyond simply securing your own systems. It necessitates understanding and assessing the security posture of your vendors, partners, and other stakeholders. This includes evaluating their security protocols, assessing their vulnerability to various threats, and implementing processes to monitor and respond to potential incidents.
Identifying and Assessing Supply Chain Vulnerabilities
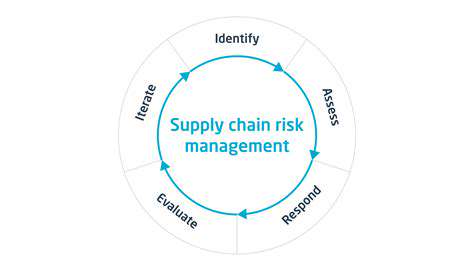
Proactively identifying potential vulnerabilities within your supply chain requires a thorough risk assessment process. This involves mapping out the entire supply chain, identifying critical components and dependencies, and assessing the security controls employed by each entity. Consider the potential impact of a security breach at each stage, from raw materials to finished products, and evaluate the potential damage to your organization's reputation and financial stability.
Regular audits and penetration testing of your supply chain partners' systems can help uncover vulnerabilities that might otherwise go unnoticed. These assessments should also consider the human element, including employee training and awareness programs to minimize the risk of social engineering attacks.
Implementing Secure Supply Chain Management Practices
Implementing a comprehensive set of secure supply chain management practices is crucial for reducing vulnerabilities. This includes establishing clear security requirements for all vendors and partners, ensuring that they adhere to industry best practices, and implementing secure communication protocols. It's important to enforce consistent security standards across the entire supply chain, fostering a culture of security vigilance.
Contractual agreements with suppliers should explicitly outline security responsibilities and expectations. This ensures shared accountability and promotes a collaborative approach to supply chain security. Regular communication and collaboration with supply chain partners are essential for identifying and addressing potential security risks in a timely manner.
Developing and Implementing Security Controls
Developing and implementing robust security controls is critical to protecting your supply chain from cyberattacks. These controls should include multi-factor authentication, data encryption, intrusion detection systems, and regular security updates. Implementing these controls across the entire supply chain, from your own systems to those of your partners, is essential for a layered defense strategy.
Regular security awareness training for employees throughout the supply chain, including vendors and partners, can help prevent phishing attacks and other social engineering tactics. A well-defined incident response plan is also critical to quickly contain and mitigate the impact of any security incidents.
Monitoring and Evaluating Security Controls
Effective cybersecurity requires continuous monitoring and evaluation of implemented controls. Regular security audits, penetration testing, and vulnerability assessments can help identify and address weaknesses in your supply chain's security posture. Metrics and key performance indicators (KPIs) should be established to measure the effectiveness of security controls and identify areas for improvement.
Continuous monitoring allows for proactive identification and response to emerging threats. This includes regularly reviewing and updating security policies and procedures to adapt to evolving threats and technologies. This proactive approach helps maintain a strong security posture and minimizes the risk of breaches.
Building a Culture of Cybersecurity
Building a culture of cybersecurity throughout your entire supply chain is vital for long-term success. This involves fostering a shared understanding of cybersecurity risks, responsibilities, and best practices amongst all stakeholders. Encouraging open communication, transparency, and collaboration is essential for identifying vulnerabilities and responding effectively to security incidents.
Providing regular security training and awareness programs to employees throughout the supply chain can significantly improve their ability to recognize and respond to potential threats. This empowers individuals to act as the first line of defense against cyberattacks, fostering a proactive security mindset.
Measuring Success and Continuous Improvement
Defining Success Metrics
Success in any endeavor, be it personal or professional, requires a clear understanding of what constitutes success. This involves identifying key performance indicators (KPIs) that accurately reflect progress towards desired outcomes. Defining these metrics upfront allows for objective evaluation and tracking of progress, enabling adjustments to strategies as needed. Without clear metrics, success remains nebulous and difficult to measure, potentially leading to wasted effort and frustration.
A crucial aspect of defining success metrics is to ensure they align with overall strategic objectives. This alignment guarantees that efforts are focused on achieving the desired results. Furthermore, the metrics must be measurable and quantifiable to facilitate accurate tracking and analysis.
Establishing Baseline Performance
Before implementing any new strategy or initiative, establishing a baseline is essential to measure success. This baseline serves as a reference point against which future performance can be compared. Understanding the current state of affairs allows for a more accurate assessment of progress and the effectiveness of implemented solutions. Without a baseline, it's difficult to determine if improvements are genuine or simply represent natural fluctuations.
This process involves collecting data on relevant metrics from the current period. This data can be gathered through various methods, such as surveys, performance reports, or existing data repositories. Analysis of this data provides insights into the current performance levels.
Tracking Key Performance Indicators (KPIs)
Continuous monitoring of KPIs is crucial for assessing progress towards success. Regular tracking provides valuable insights into trends and patterns, enabling proactive adjustments to strategies. By closely monitoring KPIs, organizations can identify areas where improvements are needed and make data-driven decisions. This proactive approach enhances efficiency and effectiveness, ultimately driving better results.
Implementing a robust tracking system ensures that data is collected, analyzed, and reported on a consistent schedule. This systematic approach ensures that important data points are not overlooked, facilitating a more comprehensive understanding of performance.
Analyzing Data and Identifying Trends
Analyzing collected data is essential for identifying trends and patterns that impact performance. By identifying these trends, organizations can make informed decisions about future strategies and resource allocation. Understanding these patterns allows for more effective allocation of resources and a more targeted approach to achieving success. This proactive approach fosters a culture of continuous improvement and optimization.
Tools and technologies designed for data analysis can greatly assist in this process. These tools can identify correlations and relationships between various factors, providing valuable insights into the driving forces behind performance fluctuations.
Adapting Strategies Based on Data Insights
Data analysis should inform strategic adjustments to ensure continuous improvement. By identifying areas requiring improvement, organizations can adapt strategies to better align with goals and objectives. Adapting strategies based on data insights is a key component of continuous improvement, leading to better outcomes over time. This approach fosters a culture of learning and innovation, driving long-term success.
Implementing changes based on data insights involves careful consideration of potential risks and benefits. Thorough planning and communication are essential for successful implementation.
Implementing Feedback Mechanisms
Implementing feedback mechanisms is crucial for gathering insights from various stakeholders. This feedback can be used to further refine strategies and ensure they are aligned with the needs and expectations of stakeholders. Open communication channels, through surveys or focus groups, ensure that the voices of stakeholders are heard and considered in the decision-making process. This approach fosters a collaborative environment and promotes a shared vision for success.
Regular feedback loops provide opportunities to address issues promptly and make necessary adjustments to strategies. This proactive approach ensures that initiatives remain relevant and effective over time.
Celebrating Milestones and Recognizing Achievements
Recognizing and celebrating milestones along the journey to success is crucial for maintaining motivation and fostering a positive work environment. Acknowledging achievements reinforces positive behaviors and encourages continued effort. This recognition fosters a sense of accomplishment and boosts morale, which in turn contributes to a more productive and engaged workforce.
Celebrating milestones can take various forms, from public acknowledgment to small rewards. The key is to find ways to make the recognition meaningful and impactful. This fosters a positive and productive work environment.