The Transformative Potential of AI in Identity and Access Management (IAM)
Artificial intelligence (AI) is rapidly revolutionizing various sectors, and Identity and Access Management (IAM) is no exception. AI's ability to analyze vast amounts of data and learn patterns offers unprecedented opportunities to enhance security, improve user experience, and streamline administrative tasks. This shift towards AI-powered IAM is poised to redefine how organizations manage user identities and access privileges in the digital age, leading to more efficient and secure operations.
Enhanced Security Through AI-Driven Threat Detection
AI algorithms can identify subtle anomalies and patterns in user behavior that might indicate a security breach, long before traditional methods could detect them. By continuously monitoring user activity and comparing it to established baselines, AI systems can flag suspicious actions, such as unusual login attempts or unauthorized access requests. This proactive approach to threat detection allows organizations to respond swiftly and effectively to potential security threats, minimizing potential damage and downtime.
AI-powered systems can also analyze and classify threats, providing insights into the nature and source of security events. This detailed analysis facilitates the development of targeted security measures, reinforcing the organization's overall security posture.
Improved User Experience Through Personalized Services
AI can personalize the user experience in IAM systems, tailoring services to individual needs and preferences. This leads to a more intuitive and user-friendly experience for employees. AI-powered self-service portals can guide users through complex tasks, providing instant access to information and support, reducing the need for manual intervention.
Automation of Repetitive Tasks and Increased Efficiency
One of the significant benefits of AI in IAM is the automation of repetitive tasks. AI can automate tasks such as user provisioning, deprovisioning, and access management, freeing up valuable time for IT staff to focus on more strategic initiatives. This automation not only boosts efficiency but also reduces the risk of human error, leading to a more secure and reliable IAM process. Furthermore, the automated nature of AI-driven IAM systems facilitates faster response times to user requests, enhancing operational efficiency.
Future Implications and Challenges in AI-Powered IAM
The integration of AI into IAM systems presents both exciting opportunities and potential challenges. While AI can significantly improve security and efficiency, concerns about data privacy and algorithmic bias must be carefully addressed. Careful consideration of ethical implications and responsible development practices are crucial for ensuring fairness and transparency in AI-driven IAM systems. Furthermore, the need for robust data governance and security measures to protect sensitive user data becomes paramount in this evolving landscape.
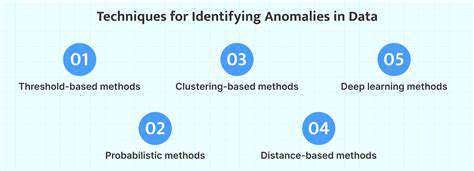
AI-Driven Anomaly Detection for Enhanced Threat Response
AI-Powered Anomaly Detection: A Comprehensive Overview
AI-driven anomaly detection is revolutionizing various industries by automating the process of identifying unusual patterns in data. This technology leverages machine learning algorithms to learn normal operating parameters and flag deviations from these established norms. By automating this process, companies can significantly reduce the time and resources spent on manual anomaly detection, allowing for quicker response times and improved efficiency.
Anomaly detection is no longer a niche technology but a critical component of modern data management. Its ability to identify outliers and unusual events is invaluable in a variety of applications, from fraud prevention to predictive maintenance. This automated approach to identifying anomalies is often more effective than traditional methods, particularly when dealing with large volumes of complex data.
Key Applications of AI Anomaly Detection
AI-powered anomaly detection finds wide application across numerous sectors. In finance, it can detect fraudulent transactions in real-time, minimizing financial losses. In healthcare, it can identify potential patient health risks, enabling early interventions and potentially saving lives. Furthermore, anomaly detection is crucial in manufacturing, where it can detect equipment malfunctions before they lead to costly downtime.
The potential of this technology extends to fields like cybersecurity, where it can identify suspicious activities and prevent breaches. By constantly monitoring systems for deviations from normal behavior, AI-powered anomaly detection systems provide a critical layer of defense against various threats.
Benefits of Implementing AI Anomaly Detection
Implementing AI-driven anomaly detection systems offers a multitude of benefits. Firstly, it enhances operational efficiency by automating a traditionally labor-intensive process. Secondly, it significantly reduces response times to critical events, enabling faster resolutions and minimizing potential damage. This proactive approach to identifying and addressing issues leads to significant cost savings and improved overall performance.
Beyond cost savings, it also improves data quality by identifying outliers and ensuring that data is more reliable. This enhanced data quality, in turn, empowers informed decision-making.
Challenges in Implementing AI Anomaly Detection
While AI-driven anomaly detection offers significant advantages, implementing such systems poses certain challenges. One key challenge is the need for high-quality data to train the algorithms effectively. Another challenge is the complexity of interpreting the results generated by the algorithms. Understanding the reasons behind flagged anomalies is vital for effective action, and sometimes this requires specialized expertise.
Additionally, ensuring the system's accuracy and reliability is crucial, especially in critical applications. Robust testing and validation are essential to ensure that the system performs as intended and can accurately distinguish between true anomalies and false positives.
Future Trends in AI Anomaly Detection
The future of AI-driven anomaly detection promises even greater advancements. We can anticipate the integration of more sophisticated machine learning models, leading to improved accuracy and efficiency in identifying anomalies. The development of explainable AI (XAI) will also be crucial, allowing for better understanding of the decision-making processes of the algorithms and fostering trust in their outputs.
Furthermore, advancements in cloud computing and edge computing will enable the deployment of these systems in more distributed and real-time environments. This will lead to even more widespread adoption and a wider range of applications for anomaly detection.
Enhancing User Experience with Personalized Access
Personalized Authentication Flows
AI-powered systems can tailor authentication experiences to individual users, significantly enhancing convenience and security. Instead of a one-size-fits-all approach, AI can analyze user behavior patterns, device characteristics, and even location to create dynamic and personalized authentication flows. This might involve streamlining the login process for frequent users, prompting multi-factor authentication only when necessary, or even anticipating potential security threats based on unusual activity and proactively blocking them. This personalized approach not only improves user satisfaction but also strengthens overall security posture by adapting to individual needs and risks.
Imagine a scenario where a user frequently logs in from their home network. The AI system could recognize this pattern and significantly reduce the complexity of the login process, perhaps even allowing single-click access. Conversely, if a login attempt originates from an unfamiliar location, the AI system can immediately flag the attempt as potentially suspicious, prompting multi-factor authentication or even blocking the access entirely, thereby minimizing the risk of unauthorized access.
Adaptive Access Control Policies
Traditional access control policies are often static and inflexible. AI can revolutionize this by creating adaptive access control policies that dynamically adjust based on real-time data. This means that access privileges can be granted or revoked based on factors such as time of day, user role, context of the request, and even current business conditions. For example, an employee might have access to sensitive data during business hours but not after hours. An AI system can automatically enforce this policy, ensuring that access is granted only when appropriate.
Furthermore, AI can identify anomalies in access patterns. If a user suddenly requests access to resources they typically do not use, the AI system can flag this activity as potentially suspicious and trigger an investigation. This proactive approach to security helps identify and mitigate potential threats before they can cause significant damage, ultimately safeguarding sensitive data and maintaining business continuity.
Proactive User Onboarding and Training
AI can greatly streamline the user onboarding process by providing personalized training and support tailored to individual needs. Rather than a generic onboarding program, AI can analyze user behavior and learning styles to create customized training materials and recommendations. This approach ensures that users understand and effectively utilize the available resources, maximizing their productivity and minimizing support requests. This personalized training can also adapt to user progress, providing additional guidance where needed and allowing users to focus on areas where they require further development.
Further, AI can identify potential issues or roadblocks in the user journey and proactively suggest solutions or provide assistance. For example, if an AI system detects that a user is struggling with a particular task, it can offer targeted help through tutorials, interactive guides, or direct assistance from support staff. This proactive approach minimizes user frustration and maximizes user adoption of the new system or application.