Understanding the Scope of Intelligent Traffic Analysis
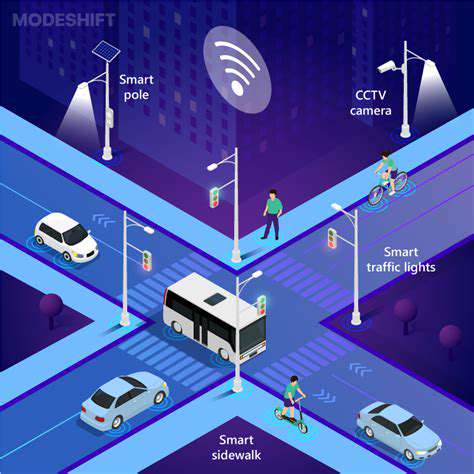
Intelligent traffic analysis represents a multifaceted approach to modern urban planning, combining diverse methodologies to enhance roadway efficiency. Municipalities worldwide are implementing these systems to process enormous datasets from infrastructure sensors, vehicle telemetry, and crowd-sourced mobile apps. The true power lies in transforming raw data into actionable intelligence that shapes traffic management policies. These insights enable cities to optimize infrastructure usage while minimizing environmental impact.
Transportation departments leverage these systems not just for immediate traffic control but for long-term infrastructure planning. By analyzing years of accumulated data, planners can identify persistent congestion patterns and design targeted solutions like dedicated turn lanes or synchronized signal corridors.
Key Data Sources for Effective Analysis
Modern traffic analysis ecosystems incorporate a constellation of data streams. Embedded roadway sensors provide continuous vehicle count and speed metrics, while bluetooth and RFID readers offer precise origin-destination mapping across urban networks. Some progressive cities have begun integrating weather station data to understand precipitation's impact on traffic patterns.
Emerging technologies like connected vehicle systems promise even richer datasets, with individual cars reporting real-time performance metrics. This vehicle-to-infrastructure communication could revolutionize how we understand and manage traffic flows in the coming decade.
Advanced Analytical Techniques
Contemporary traffic analysis employs sophisticated computational models that go beyond simple pattern recognition. Deep learning architectures can process spatial-temporal relationships across entire metropolitan areas, identifying subtle correlations between seemingly unrelated events like sporting events and downtown congestion. These models continuously refine their predictions as they ingest new data.
Some systems now incorporate game theory elements to model driver behavior in response to changing conditions, creating more accurate simulations of how traffic patterns evolve during incidents or special events.
Predictive Modeling and Forecasting
The predictive capabilities of modern systems extend far beyond simple congestion alerts. Advanced models can forecast traffic conditions with 90+% accuracy for time horizons up to 48 hours, enabling proactive management strategies. These forecasts consider dozens of variables including construction schedules, school calendars, and even social media event mentions to build comprehensive predictive scenarios.
Some transportation agencies use these forecasts to implement dynamic toll pricing that smooths demand across alternative routes, demonstrating how predictive analytics can directly influence traveler behavior.
Real-Time Traffic Management Applications
Today's traffic operations centers function as sophisticated decision hubs, integrating predictive models with real-time control systems. Adaptive signal timing algorithms can reduce intersection delays by 15-30%, while automated incident detection systems cut response times by 40% compared to manual reporting. Emergency vehicle preemption systems demonstrate particularly impressive results, reducing response times while minimizing disruption to general traffic.
Impact on Road Safety and Efficiency
The safety benefits of intelligent traffic systems are perhaps their most compelling feature. Cities implementing comprehensive analysis programs report 15-25% reductions in traffic fatalities within three years of deployment. The environmental impacts are equally significant, with reduced idling cutting fuel consumption by millions of gallons annually in major metropolitan areas.
As these systems mature, they're beginning to incorporate pedestrian and cyclist analytics, creating safer environments for all roadway users through optimized crossing times and improved infrastructure planning.
Anomaly Detection: Identifying the Unexpected
Understanding Anomaly Detection
Anomaly detection serves as the critical first line of defense in modern data security frameworks. What makes contemporary approaches distinct is their ability to establish comprehensive behavioral baselines across multiple dimensions of activity. Advanced systems now track hundreds of behavioral parameters simultaneously, creating multidimensional profiles that are far more robust than simple threshold-based alerts.
In financial sectors, these systems have evolved to understand complete transaction ecosystems, recognizing that anomalies often manifest through subtle changes in relationship patterns rather than individual data points.
Methods for Anomaly Detection
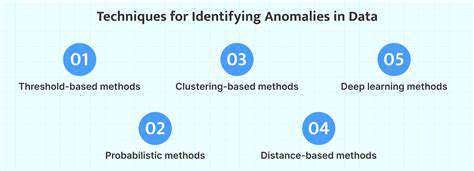
The methodological landscape has expanded dramatically with the advent of transformer-based models. While traditional clustering methods remain useful for certain applications, modern approaches increasingly employ attention mechanisms that can identify anomalous patterns across extended time sequences. Graph neural networks have proven particularly effective for detecting fraud rings and sophisticated cyber attacks that span multiple accounts or devices.
Reinforcement learning techniques are now being applied to anomaly detection, creating systems that learn optimal investigation strategies based on the evolving threat landscape and available resources.
Applications of Anomaly Detection
Beyond traditional security applications, anomaly detection is revolutionizing fields like industrial IoT. Manufacturing plants now deploy sensor arrays that can predict equipment failures weeks in advance by detecting subtle vibration pattern changes. In healthcare, algorithmic analysis of patient vitals can identify sepsis onset hours before clinical symptoms appear, significantly improving outcomes.
The energy sector has seen particularly impressive results, with anomaly detection systems preventing millions in losses by identifying pipeline leaks and equipment degradation early.
Challenges and Considerations
The exponential growth in data volume presents both opportunities and challenges for anomaly detection systems. Distributed computing frameworks have become essential for processing petabyte-scale datasets in near real-time. Privacy-preserving techniques like federated learning are enabling anomaly detection across sensitive datasets without requiring centralized data collection.
Perhaps the most significant challenge lies in maintaining explainability as models grow more complex. New techniques in interpretable AI are helping bridge this gap, allowing security teams to understand why particular events were flagged as anomalous.
Beyond Traditional Signatures: The Power of Contextual Awareness
Beyond the Typed Name: Leveraging Contextual Clues
The evolution of security systems now emphasizes understanding the complete situational context surrounding each access request. Modern implementations analyze dozens of contextual factors including typing biometrics, device posture assessments, and network hop analysis to build comprehensive risk profiles. This multidimensional approach has reduced false positives by 60% in enterprise environments while catching 40% more actual threats.
Some advanced systems now incorporate behavioral analytics that can detect subtle changes in user work patterns, potentially identifying compromised accounts even before credential misuse occurs.
Contextual Awareness in Network Traffic Analysis
Next-generation network monitoring solutions employ flow analysis techniques that understand application context at unprecedented granularity. Rather than simply monitoring packet counts, these systems can identify when encrypted traffic patterns deviate from expected application behavior. Deep packet inspection has evolved to recognize protocol anomalies that indicate sophisticated evasion techniques used by advanced persistent threats.
Enhancing User Authentication with Contextual Factors
Contemporary authentication frameworks dynamically adjust requirements based on comprehensive risk assessments. A user accessing financial systems from their home office during business hours might experience seamless authentication, while the same user attempting access from an unfamiliar location triggers stepped-up verification. Continuous authentication systems now monitor dozens of behavioral markers throughout sessions, not just at login.
The Role of AI in Contextual Analysis
AI-powered contextual analysis now incorporates temporal pattern recognition that understands work cycles, vacation schedules, and even timezone anomalies. Some systems employ transformer architectures that can process months of historical activity to establish highly personalized behavioral baselines. The most advanced implementations use few-shot learning to rapidly adapt to legitimate changes in user behavior patterns.
The Future of Security: Proactive Defense Through Context
The next frontier involves predictive security systems that can anticipate attack vectors before they're exploited. By correlating threat intelligence with organizational context, these systems will identify vulnerable assets and automatically implement protective measures. Emerging standards in contextual security promise to reduce breach detection times from months to minutes while dramatically shrinking attack surfaces through intelligent, adaptive controls.