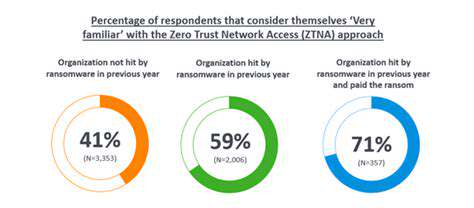
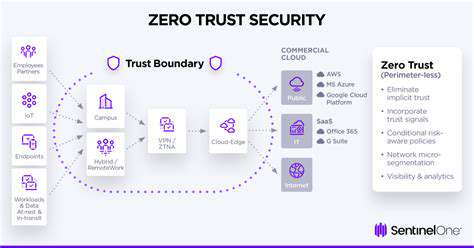
Identifying and Mitigating Potential Vulnerabilities
Identifying Potential Vulnerabilities in the Supply Chain
A critical aspect of robust supply chain security is the proactive identification of potential vulnerabilities. This involves a comprehensive assessment of all stages of the supply chain, from raw material sourcing to final product delivery. This includes scrutinizing the processes, procedures, and security measures employed by each supplier and partner throughout the chain. A thorough risk assessment should consider factors such as geographical location, political instability, and the potential for natural disasters, which can all disrupt operations and expose sensitive data or materials. Proactive identification of these potential weaknesses is paramount for creating a resilient and secure supply chain.
Identifying vulnerabilities also necessitates a deep dive into potential threats. This includes evaluating the likelihood of malicious actors targeting specific stages of the supply chain. From theft of intellectual property to the introduction of counterfeit or harmful components, understanding the potential threats is crucial in developing effective countermeasures. This requires meticulous analysis of emerging threats, including evolving cyberattacks and criminal activity, along with understanding the specific vulnerabilities each stage of the supply chain presents.
Mitigating Vulnerabilities Through Enhanced Security Measures
Once vulnerabilities have been identified, the next step is implementing robust security measures to mitigate the risk. This involves a multi-faceted approach incorporating strong encryption protocols, secure data transfer methods, and strict access controls. Furthermore, implementing robust supplier vetting processes is essential. This includes background checks, security audits, and adherence to industry standards, which can help ensure that only trusted and secure partners are included in the supply chain. Establishing clear communication channels and escalation procedures within the supply chain is also critical to quickly identify and address potential issues or security breaches.
Implementing advanced security technologies like intrusion detection systems and firewalls can significantly reduce the risk of cyberattacks. Regular security audits and penetration testing are also crucial to identify and address vulnerabilities before they can be exploited. Training employees on security protocols and best practices is another key component of mitigation. A dedicated security team can also monitor the supply chain for suspicious activity and ensure the implementation and enforcement of security policies.
Implementing a Culture of Security Throughout the Supply Chain
A robust supply chain security strategy requires a fundamental shift toward a culture of security. This means fostering a collaborative environment where all stakeholders understand their role in maintaining security. Transparent communication and collaboration with suppliers and partners are essential to build trust and ensure everyone is aligned on security protocols. This includes fostering open communication channels for reporting potential security breaches or concerns. Regular training sessions and awareness campaigns can educate all members of the supply chain about potential risks and best practices.
Establishing clear lines of accountability and responsibility for security measures is vital. Every member of the supply chain must understand their specific security obligations and the consequences of non-compliance. This ensures that everyone is actively involved in maintaining the security of the entire system. Regular security audits and reviews, combined with a commitment to continuous improvement, will strengthen the overall resilience of the supply chain.
Implementing Robust Supplier Risk Assessment Strategies
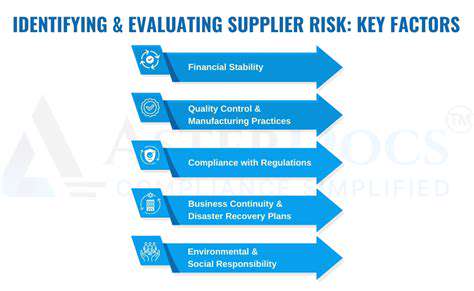
Identifying Potential Risks
A crucial first step in implementing robust supplier risk management is to proactively identify potential risks associated with your supply chain. This involves a thorough assessment of each supplier's operational capabilities, financial stability, and compliance with relevant regulations. Understanding the potential vulnerabilities within your supply chain is paramount to mitigating potential disruptions and safeguarding your business interests. Consider factors such as geographic location, political instability, and potential natural disasters. These factors can all contribute to disruptions and negatively impact your operations.
Evaluating Supplier Performance
Regularly evaluating supplier performance is essential for identifying emerging risks and trends. This evaluation should encompass a variety of metrics, including on-time delivery rates, quality control records, and adherence to agreed-upon contracts. By closely monitoring these key performance indicators, you can gain valuable insights into the reliability and resilience of your suppliers. Monitoring supplier performance allows for proactive adjustments and mitigation strategies to prevent or minimize potential disruptions.
Developing Mitigation Strategies
Once potential risks are identified and supplier performance is evaluated, developing effective mitigation strategies is critical. These strategies should address various scenarios, from natural disasters to economic downturns. Developing contingency plans for potential disruptions is essential for maintaining business continuity. Having a well-defined plan and clear communication channels for response during critical events will significantly reduce the impact of unforeseen circumstances.
Implementing Due Diligence Procedures
Implementing comprehensive due diligence procedures is a vital component of robust supplier risk management. This process should involve thorough background checks on suppliers, including financial audits and compliance reviews. These checks will provide valuable insights into the stability and reliability of your suppliers.
Thorough due diligence will greatly reduce the probability of working with unreliable suppliers. This careful review of potential partners is crucial to long-term business success.
Establishing Clear Communication Channels
Establishing clear communication channels with suppliers is essential for maintaining transparency and responsiveness. This includes regular meetings, clear reporting procedures, and a system for escalating issues. Open communication facilitates timely issue resolution and fosters trust between your organization and your suppliers. This will help to build stronger relationships and identify potential problems early.
Implementing Contingency Plans
Developing comprehensive contingency plans for potential disruptions is an integral part of supplier risk management. These plans should outline procedures for handling various scenarios, such as natural disasters, economic downturns, or political instability. Having a clear and well-rehearsed contingency plan is crucial for maintaining business continuity and minimizing the impact of unforeseen events. These plans should be regularly reviewed and updated to ensure their effectiveness.
Monitoring and Reviewing Performance
Regularly monitoring and reviewing the performance of your supplier risk management program is crucial for its long-term effectiveness. This process should involve analyzing data, identifying trends, and making adjustments to your strategies as needed. Continuous monitoring and evaluation of your supplier risk management program will help to identify areas for improvement and maintain a proactive approach to mitigating potential disruptions. This will help to ensure that your supplier risk management program remains aligned with your business goals.
Strengthening Security Protocols Across the Entire Chain
Improving Supplier Due Diligence
Thorough supplier due diligence is crucial for identifying and mitigating potential security risks within the supply chain. This involves conducting comprehensive background checks, verifying certifications, and assessing the supplier's security posture. A robust due diligence process should extend beyond just verifying compliance with regulations; it should also evaluate the supplier's internal controls, procedures, and potential vulnerabilities. This proactive approach helps to identify weaknesses early on, preventing potential breaches and safeguarding sensitive data throughout the supply chain.
Regular assessments of suppliers' security practices are essential. This includes evaluating their incident response plans, their ability to handle security breaches, and their compliance with industry best practices. This continuous monitoring process allows businesses to adapt to evolving threats and maintain a strong security posture.
Implementing Robust Access Control Measures
Implementing strict access control measures across the entire supply chain is critical. This involves limiting access to sensitive information and resources to only authorized personnel, both within the company and among its partners. Implementing multi-factor authentication and regularly reviewing access privileges can significantly reduce the risk of unauthorized access and data breaches.
Clear and well-defined roles and responsibilities should be established for all individuals involved in the supply chain, from procurement to delivery. This clear definition of roles and responsibilities will help prevent confusion and ensure accountability in case of security incidents.
Enhancing Data Encryption and Protection
Data encryption is paramount for safeguarding sensitive information transmitted throughout the supply chain. Implementing strong encryption protocols for data at rest and in transit will protect sensitive data from unauthorized access, even if a breach occurs. This includes utilizing industry-standard encryption algorithms and regularly reviewing and updating encryption keys.
Establishing and Maintaining Secure Communication Channels
Secure communication channels are essential for maintaining confidentiality and integrity throughout the supply chain. Using encrypted communication protocols for all internal and external communications, including emails, instant messaging, and file sharing, is critical. Regularly auditing and updating these channels helps to ensure security against evolving threats and vulnerabilities.
Implementing Secure Software Development Practices
Incorporating secure software development practices into the entire software development lifecycle is essential for building secure applications used throughout the supply chain. Developers should be trained in secure coding practices, and security testing should be incorporated into each stage of the development process. Using secure coding standards and performing regular vulnerability assessments can help to prevent vulnerabilities from being introduced into applications.
Promoting Collaboration and Information Sharing
Promoting collaboration and information sharing among all stakeholders in the supply chain is vital for a comprehensive security approach. Establishing clear communication channels and protocols for sharing information about potential threats, vulnerabilities, and security incidents is paramount. This collaborative approach enables faster incident response and allows for continuous improvement of security practices.