Building a Comprehensive Incident Response Plan

Defining Incident Response
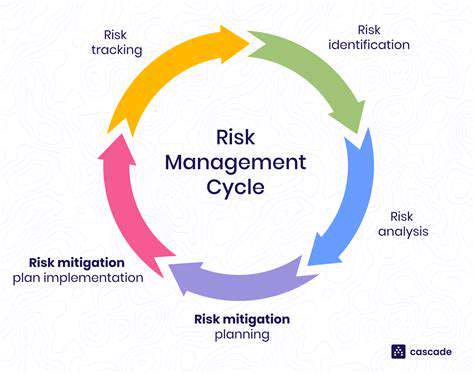
A comprehensive incident response plan is crucial for any organization, outlining the steps to be taken when a security incident occurs. This plan should clearly define roles and responsibilities for individuals and teams involved. Effective incident response minimizes damage, maintains business continuity, and helps organizations learn from experiences. It should cover all potential threats and vulnerabilities, from simple data breaches to large-scale cyberattacks.
This structured approach to handling security incidents ensures a coordinated and efficient response, minimizing potential downtime and negative consequences. A well-defined procedure for reporting, investigating, and resolving incidents is paramount to mitigating risks and maintaining stakeholder trust.
Planning for Incident Prevention
Proactive measures are essential for preventing incidents in the first place. Organizations should implement robust security controls, including firewalls, intrusion detection systems, and access controls, to safeguard against potential threats. Regular security audits and vulnerability assessments are vital to identifying and patching weaknesses in systems and applications. This proactive approach reduces the likelihood of incidents and minimizes the potential impact if an incident does occur.
Implementing security awareness training for employees is also a significant part of prevention. Educating staff about common threats and safe practices significantly reduces the risk of human error leading to incidents. Strong password policies and multi-factor authentication are critical elements of a robust security posture.
Developing an Incident Response Team
Establishing a dedicated incident response team is critical for effective incident management. This team should consist of individuals with specialized skills in areas like network security, digital forensics, and communications. Clear communication channels and protocols within the team are essential for quick and coordinated action.
Establishing Communication Protocols
Effective communication is paramount during an incident. Clear communication channels and procedures must be established to ensure timely and accurate information sharing with stakeholders, including employees, customers, and regulatory bodies. Prompt communication helps maintain trust and minimizes reputational damage. This includes procedures for external communication, such as notifying law enforcement or regulatory agencies as appropriate.
Executing the Incident Response Plan
When an incident occurs, the incident response plan should be executed swiftly and methodically. This involves identifying the scope of the incident, containing the threat, and then remediating the damage. Each step should be documented thoroughly for analysis and future improvements. Prompt and accurate documentation is critical for post-incident analysis.
Post-Incident Analysis and Improvement
After resolving an incident, a thorough post-incident analysis is essential. This analysis should review the effectiveness of the response plan, identify areas for improvement, and implement changes to prevent future incidents. Learning from past experiences is vital to refining the incident response process. Regular updates and revisions to the plan are critical to adapt to evolving threats and vulnerabilities. This cyclical process of analysis, improvement, and refinement ensures the continued effectiveness of the incident response plan.