Defining Zero Trust in the Cloud Context

Defining Zero Trust in the Cloud Context
Zero Trust, in the context of cloud security, represents a fundamental shift in how organizations approach access control. Instead of relying on traditional network perimeters, Zero Trust assumes no implicit trust, either for users or devices, regardless of their location within or outside the corporate network. This approach mandates continuous verification and authorization of any user or device attempting to access cloud resources. This is crucial because the traditional perimeter-based security model is no longer sufficient in today's dynamic and increasingly distributed cloud environments.
A key aspect of Zero Trust in the cloud is the implementation of micro-segmentation. This involves dividing the cloud environment into smaller, isolated segments, limiting the potential impact of a security breach. By segmenting resources, an attacker's ability to move laterally across the network and access sensitive data is significantly reduced. This granular control is vital for maintaining security in a cloud environment where resources are often shared and interconnected. This micro-segmentation also enables fine-grained access controls, allowing administrators to precisely define who can access specific resources and under what conditions.
Key Principles and Implementation Considerations
The cornerstone of Zero Trust in the cloud is the principle of never trust, always verify. This principle mandates that all users and devices, regardless of their location or network affiliation, must undergo rigorous authentication and authorization processes before being granted access to cloud resources. This proactive approach to security significantly reduces the attack surface and ensures that only authorized individuals and devices can access sensitive data.
Implementing Zero Trust in a cloud environment requires a comprehensive security strategy that encompasses multiple layers of defense. This includes strong authentication methods, like multi-factor authentication (MFA), robust access control policies, and continuous monitoring of user and device activity. Furthermore, organizations must invest in security information and event management (SIEM) tools to detect and respond to potential threats in real-time. This layered approach is essential to maintain a secure and resilient cloud infrastructure.
Another crucial component is the ability to adapt to dynamic cloud environments. As cloud deployments evolve, security policies must be able to scale and adapt to new users, devices, and resources. This requires a flexible security architecture that can be easily configured and managed. This is important to ensure continuous security and to prevent vulnerabilities from being exploited.
Finally, effective communication and collaboration between security teams and application development teams are essential. Zero Trust security principles must be integrated into the design and development lifecycle of cloud applications to ensure that security is built into every aspect of the system, from the initial design phase to ongoing maintenance.
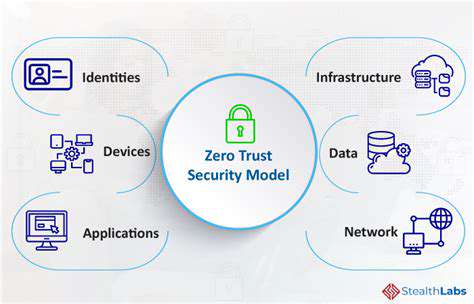
Implementing Zero Trust in Cloud Infrastructure

Understanding the Foundation of Zero Trust
Zero Trust security is a security model that assumes no implicit trust, regardless of whether the user or device is inside or outside the organization's network perimeter. It's a significant shift from traditional network security approaches that often rely on a trusted network. This approach demands continuous verification and authorization of every user and device attempting to access resources, regardless of location. This requires a robust authentication and authorization system that verifies every request, ensuring that only authorized users and devices can access sensitive data and applications.
Crucially, Zero Trust recognizes that a compromised device or user can lead to a breach of the entire network. By implementing strict access controls and continuous monitoring, organizations can reduce the risk of unauthorized access and data breaches. This methodology necessitates a shift in thinking from a perimeter-based security model to one that prioritizes continuous validation of user and device identities and access requests.
Key Components of a Zero Trust Architecture
A robust Zero Trust architecture comprises several essential components. These include a strong identity and access management (IAM) system, which ensures that users and devices are properly authenticated and authorized. Furthermore, a comprehensive network segmentation strategy is paramount to limit the impact of a breach. This involves dividing the network into smaller, isolated segments to contain any potential attacks.
Another crucial component is continuous monitoring and threat detection. This involves using advanced security tools to constantly monitor network traffic and identify suspicious activities. This proactive approach allows organizations to detect and respond to threats in real-time. This continuous monitoring should include user activity, device behavior, and application usage, all of which can help in identifying potential malicious activities.
Implementing Zero Trust in Cloud Environments
Implementing Zero Trust in cloud environments presents unique challenges, but also opportunities. Cloud environments, by their very nature, often lack a clearly defined perimeter. Therefore, organizations must implement robust access controls that extend beyond traditional network boundaries. This requires a shift to a cloud-native security approach that incorporates micro-segmentation and other advanced security techniques.
Security information and event management (SIEM) solutions are essential for cloud environments, enabling comprehensive visibility into user and device activities. Integrating security analytics and threat intelligence capabilities into the Zero Trust framework provides an additional layer of protection against advanced threats. This proactive approach enables organizations to proactively identify and mitigate potential risks in a cloud environment.