Proactive Security Monitoring and Threat Intelligence

Proactive Threat Detection
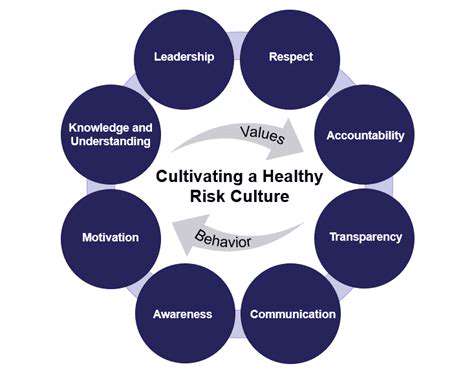
Proactive security monitoring goes beyond simply reacting to security incidents. It involves implementing strategies and technologies to identify potential threats before they can cause significant damage. This proactive approach often uses advanced analytics and machine learning algorithms to detect anomalies and patterns that might indicate malicious activity. By anticipating and mitigating threats, organizations can significantly reduce the risk of costly breaches and downtime.
This proactive approach is crucial in today's complex threat landscape. Criminals are constantly developing new methods to exploit vulnerabilities, and reactive security measures are often insufficient to keep pace. Proactive monitoring provides a critical layer of defense, allowing organizations to stay ahead of the curve and protect sensitive data.
Implementing a Robust Security Framework
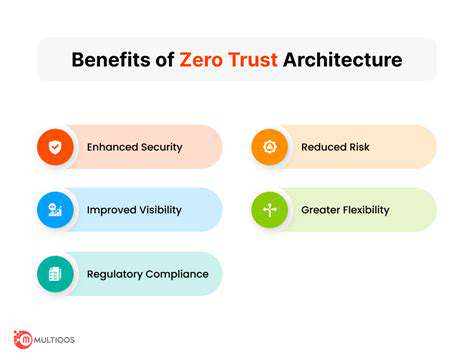
A robust security framework is the foundation of any effective proactive security monitoring program. This framework should encompass a variety of security controls, including firewalls, intrusion detection systems (IDS), and antivirus software. It should also include policies and procedures for user access, data handling, and incident response.
Furthermore, the security framework must be regularly reviewed and updated to adapt to evolving threats and vulnerabilities. Regular security audits and penetration testing are essential components of a strong framework.
Leveraging Advanced Analytics and Machine Learning
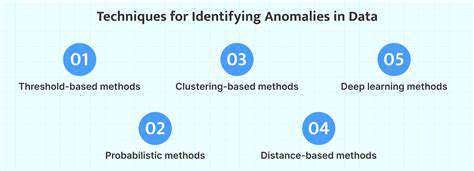
Advanced analytics and machine learning are critical for identifying subtle anomalies that might indicate malicious activity. These techniques can analyze vast amounts of security data to identify patterns and behaviors that traditional security tools might miss.
For example, machine learning algorithms can be trained to recognize the unique characteristics of malicious software and network traffic, enabling early detection and prevention of attacks.
Enhancing Security Awareness Training
Employee training is a vital component of any proactive security strategy. Educating employees about common security threats and best practices can help prevent human error, which is often a significant factor in security breaches. Regular awareness training programs can significantly reduce the risk of employees unknowingly falling victim to phishing scams or other social engineering attacks.
Continuous Monitoring and Improvement
Security monitoring is not a one-time task; it's an ongoing process. Security teams must continuously monitor systems, analyze data, and adjust strategies based on emerging threats and vulnerabilities. This continuous improvement cycle ensures the security posture remains strong and adaptable. Regular performance evaluations and feedback mechanisms are essential to identify areas for improvement and refine the security monitoring strategy.
Incident Response Planning and Execution
Having a well-defined incident response plan is essential for handling security breaches effectively. This plan should outline the procedures for detecting, containing, and recovering from security incidents. A comprehensive incident response plan ensures that organizations can effectively manage and mitigate the impact of security breaches, minimizing disruption and data loss.
Regularly testing and practicing the incident response plan is crucial for ensuring its effectiveness and improving response times.