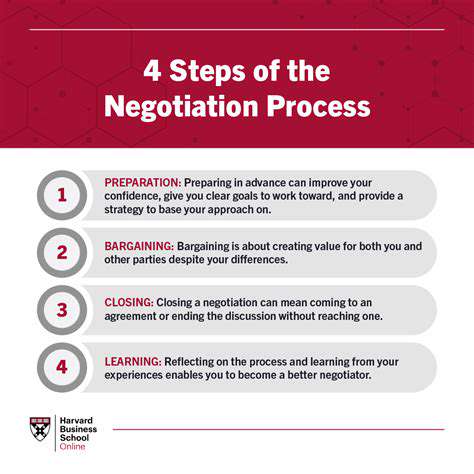
Understanding the Negotiation Process
Negotiation is a crucial aspect of any successful business transaction. It involves a give-and-take process where both parties aim to reach a mutually beneficial agreement. Understanding the dynamics of negotiation, from initial contact to final agreement, is essential for achieving favorable outcomes. This process requires active listening, clear communication, and a willingness to compromise.
Effective negotiation strategies often involve anticipating potential objections and developing counterarguments. Understanding the needs and motivations of the other party is equally important for building rapport and finding common ground. It's not just about winning, but about finding a solution that works for everyone involved.
Payment Terms and Conditions
Defining clear payment terms and conditions is critical for managing financial risks and ensuring smooth transactions. This includes specifying the payment method, due dates, and any penalties for late payments. Failing to establish these clearly can lead to disputes and delays, impacting the overall success of the deal.
Detailed payment schedules and documentation are vital for maintaining accurate records and preventing misunderstandings. Thoroughly reviewing and understanding these terms before signing any agreement is paramount for avoiding future complications.
Factors Influencing Negotiation Outcomes
Several factors can influence the outcome of a negotiation, including the relative power of each party, the urgency of the situation, and the emotional climate. Understanding these dynamics allows for a more strategic approach, enabling negotiators to better navigate challenging situations.
Market conditions, economic trends, and prevailing industry practices also play a significant role. Keeping abreast of these factors can provide valuable insight into the potential challenges and opportunities presented during the negotiation process.
Strategies for Effective Payment Collection
Establishing a robust payment collection strategy is vital for maintaining financial stability and ensuring timely receipt of funds. This involves proactive communication with clients, clearly outlining payment expectations, and following up on outstanding payments in a professional manner.
Implementing a system for tracking payments and managing outstanding balances is crucial for minimizing risk and maximizing efficiency. Utilizing technology to streamline this process can significantly improve the overall efficiency of payment collection.
Legal Considerations in Negotiation
Navigating legal considerations during negotiation is essential to avoid potential legal issues down the road. Thorough review of contracts and agreements ensures understanding of all terms and conditions, mitigating risk and protecting your interests.
Understanding legal implications related to payment terms and contract obligations is important. Seeking legal counsel when necessary can provide crucial guidance and help prevent costly mistakes.
Risk Management in Payment Transactions
Identifying and mitigating risks associated with payment transactions is crucial for protecting financial interests. Implementing secure payment processing systems and maintaining detailed records are important steps in risk management.
Employing fraud prevention measures and adhering to industry best practices can help safeguard against potential financial losses. Regularly reviewing and updating risk management strategies is essential for adapting to changing circumstances and maintaining a secure financial environment.
Alternative Dispute Resolution
Having a plan for resolving disputes is crucial in business dealings. Exploring alternative dispute resolution methods, such as mediation or arbitration, can be a cost-effective and less adversarial way to address disagreements and reach mutually acceptable solutions.
These methods often provide a faster and more efficient way to resolve issues than traditional litigation, minimizing time and resource expenditure. Understanding the benefits and limitations of each approach is essential for making informed decisions.
Insects, often overlooked as a food source, are increasingly being recognized for their significant protein content and sustainability advantages. They require far less land and water to produce compared to traditional livestock, making them a potentially crucial component of a more sustainable food system. Furthermore, insect farming can reduce greenhouse gas emissions, contributing to a more environmentally friendly approach to protein production.
Preventing Future Attacks: Implementing Robust Security Measures
Strengthening Defenses Against Ransomware
A proactive approach to ransomware prevention is crucial. This involves implementing multiple layers of security controls that extend beyond simple antivirus software. A comprehensive strategy should include regular security audits, vulnerability assessments, and penetration testing to identify and address potential weaknesses in the system. This proactive approach can significantly reduce the likelihood of a successful attack.
Regular security awareness training for employees is also essential. Phishing attacks are a common vector for ransomware infections, and educating employees on how to recognize and avoid suspicious emails, links, and attachments can create a strong human firewall. Equipping employees with the knowledge and tools to identify potential threats is critical to preventing successful ransomware intrusions.
Developing a Robust Backup and Recovery Plan
A well-defined backup and recovery plan is a cornerstone of ransomware resilience. This plan should encompass regular, automated backups of critical data, stored offline and preferably in a geographically separate location. Regular testing of the recovery process is vital to ensure that data can be restored quickly and efficiently in the event of an attack.
Implementing a robust backup strategy involves more than just creating backups. It also entails carefully considering where to store them, how frequently to update them, and how to verify their integrity. A comprehensive backup strategy will ensure that data loss is minimized or, ideally, eliminated in the event of a ransomware attack.
Implementing Multi-Factor Authentication (MFA)
Implementing multi-factor authentication (MFA) adds an extra layer of security to accounts, significantly reducing the risk of unauthorized access. MFA requires users to provide more than one form of verification, such as a password and a code from a mobile device. This makes it much harder for attackers to gain access even if they compromise a password.
MFA significantly enhances the security posture of an organization, especially in light of the growing sophistication and frequency of cyberattacks. By requiring multiple forms of identification, MFA mitigates the risk of unauthorized access and protects sensitive data from breaches.
Enhancing Endpoint Security
Protecting endpoints, such as computers and mobile devices, is vital in preventing ransomware attacks. Employing strong endpoint detection and response (EDR) solutions can help identify and contain malicious activity before it spreads throughout the network. Regular software updates and patches for operating systems and applications are also crucial to address known vulnerabilities.
Regularly monitoring endpoint security logs and proactively addressing any detected anomalies can help prevent ransomware infections. A layered approach that integrates various security tools and strategies will strengthen the defense against potential threats, thereby minimizing the damage caused by a ransomware attack.
Utilizing Security Information and Event Management (SIEM)
Implementing a Security Information and Event Management (SIEM) system allows organizations to collect and analyze security logs from various sources, providing a centralized view of security events. This system can detect unusual patterns and activities that might indicate a ransomware attack is underway.
SIEM systems provide a comprehensive picture of security events, facilitating early detection of suspicious activities. By analyzing logs and identifying anomalies, SIEM can help prevent ransomware attacks by enabling timely response and containment. This proactive measure significantly reduces the potential for widespread data breaches.
Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are essential for identifying vulnerabilities in systems and networks. These assessments help organizations understand their current security posture and prioritize remediation efforts. Penetration testing simulates real-world attacks to assess the effectiveness of security controls.
Regularly evaluating security measures ensures that defenses remain up-to-date and effective against emerging threats. This proactive approach minimizes the risk of successful ransomware attacks by identifying and addressing weaknesses in the system architecture and processes. By identifying vulnerabilities, organizations can proactively mitigate potential risks and strengthen their security posture.