The Growing Threat Landscape of Smart Home Devices
The Rise of Smart Home Devices
The proliferation of smart home devices has revolutionized how we interact with our living spaces, offering convenience and automation previously unimaginable. From smart thermostats and lighting systems to security cameras and voice assistants, these interconnected devices promise a seamless and intelligent home environment. However, this interconnectedness comes with a significant security risk, as these devices often collect and transmit sensitive data about our daily lives.
This rapid adoption of smart home technologies has outpaced the development of robust security measures, creating a significant vulnerability for consumers.
Security Vulnerabilities in Smart Home Ecosystems
Smart home devices, despite their convenience, are often vulnerable to various security breaches. These vulnerabilities arise from a combination of factors, including weak default passwords, outdated firmware, lack of encryption protocols, and insufficient data protection measures. Attackers can exploit these flaws to gain unauthorized access to user data, control devices, and even compromise entire home networks.
Furthermore, the interconnected nature of smart home devices creates a cascading effect. If one device is compromised, it could potentially expose other linked devices and systems to security risks, creating a domino effect that threatens the entire home network.
The Potential for Data Breaches
Smart home devices collect and transmit vast amounts of data about our habits, preferences, and routines. This data can include information about our location, schedules, routines, and interactions within the home. This data, if compromised, could have serious consequences, from identity theft to financial fraud, and even the potential for physical harm if the device controls critical home systems, like security systems.
The potential for data breaches is particularly concerning given the sensitive nature of the data collected by smart home devices.
The Impact on User Privacy
The collection and transmission of personal data by smart home devices raise significant privacy concerns. Users often have limited understanding of how their data is being collected, used, and shared. Without clear privacy policies and transparent data handling practices, consumers may be unknowingly exposing their personal information to potential risks.
The lack of user control over data collection practices and the potential for data misuse highlight the urgent need for stronger privacy safeguards in the smart home ecosystem.
The Role of Manufacturers in Security
Manufacturers play a crucial role in mitigating the security risks associated with smart home devices. Implementing robust security protocols, including strong encryption, secure authentication methods, and regular firmware updates, is essential to protect user data and prevent unauthorized access. Manufacturers also have a responsibility to educate consumers about the security risks and provide clear guidelines for safe device usage.
A proactive approach to security on the part of manufacturers is critical in ensuring the safety and privacy of consumers.
Consumer Responsibilities in Security
While manufacturers bear a significant responsibility, consumers also have a critical role to play in ensuring the security of their smart home devices. Taking proactive steps, such as choosing strong and unique passwords, keeping firmware updated, and being cautious about sharing personal information with devices, can significantly reduce the risk of a security breach. Furthermore, consumers should thoroughly research the security protocols of any smart home device they intend to purchase.
Addressing the Growing Threat Landscape
The expanding threat landscape surrounding smart home devices demands a multi-pronged approach to security. This includes collaboration between manufacturers, governments, and consumers to establish and enforce robust security standards, develop effective cybersecurity measures, and educate users about the risks and best practices for safe device use. Continuous monitoring and adaptation to evolving threats are essential to keep pace with the rapidly changing technological landscape.
Ultimately, a coordinated effort is needed to address this growing security concern and safeguard the privacy and security of consumers' smart home environments.
Strengthening Your Smart Home Network Security Posture
Understanding the Risks
Smart home devices, while convenient, often introduce vulnerabilities to your network. These devices frequently lack robust security features, making them attractive targets for hackers. Their inherent connectivity to your home network exposes your entire system to potential breaches if one device is compromised. This risk extends beyond simple data theft, potentially allowing unauthorized access to your home's critical systems.
Furthermore, outdated firmware and weak default passwords on these devices significantly increase the risk. Failing to update your smart home devices leaves them susceptible to known exploits, making them easy prey for malicious actors. This lack of proactive security measures can have serious consequences.
Choosing Secure Devices
Prioritize devices with strong security protocols like WPA2 or WPA3 encryption. Look for certifications from reputable security organizations that validate the device's security posture. Reading reviews and comparisons can provide valuable insights into the security features of different smart home devices. A thorough investigation into the device's security protocols before purchase can significantly reduce the risk of a compromised system.
Consider the device's privacy policy and how it handles your data. A transparent and robust privacy policy offers reassurance that your data is handled responsibly. Understanding the device's data handling practices is crucial for maintaining your overall security posture.
Implementing Strong Passwords
Creating and using unique, complex passwords for each smart home device is essential. Avoid using easily guessed passwords, such as birthdates or names. Utilize a password manager to generate and store these complex passwords securely, ensuring you don't have to rely on memorization and reducing the risk of compromised credentials.
Utilizing Network Segmentation
Segmenting your network can help isolate vulnerable smart home devices from critical systems. This isolates potential threats, preventing widespread damage if one device is compromised. By creating separate networks for your smart home devices, you can significantly limit the impact of a security breach.
Actively Monitoring Your Network
Regularly monitor your network for unusual activity. Utilize network monitoring tools to detect suspicious traffic patterns or unauthorized access attempts. Implementing these proactive measures can help you identify and respond to potential threats quickly, preventing significant damage.
Set up alerts for suspicious login attempts or unauthorized device connections. This proactive approach can help you identify and contain security breaches early on, minimizing the potential impact on your smart home system.
Regular Firmware Updates
Keeping your smart home devices' firmware up to date is critical for patching security vulnerabilities. Manufacturers frequently release updates that address known exploits, significantly strengthening your network's security posture. Regular firmware updates are a crucial part of maintaining a secure smart home environment.
Failure to update your devices can create significant security gaps that malicious actors can exploit. Proactively updating firmware is an essential step in mitigating these risks and maintaining a secure smart home setup.
Protecting Your Personal Data and Privacy
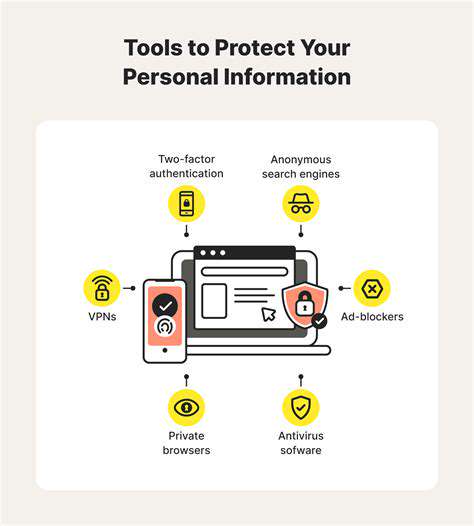
Protecting Your Personal Data Online
In today's digital age, safeguarding your personal data is paramount. With increasing reliance on online services, the risk of data breaches and unauthorized access is ever-present. Understanding the risks and taking proactive steps to protect your information is crucial for maintaining your privacy and security. This includes being aware of the different types of personal data that are collected and how they might be used.
Protecting your personal information online requires a multifaceted approach. This includes not just being cautious about what you share but also understanding how companies collect and use your data. This awareness allows you to make informed decisions about the level of risk you are willing to accept when using online services.
Identifying Potential Threats
Cybercriminals employ various tactics to gain access to personal data. Phishing scams, malware infections, and social engineering are just a few examples of the threats you might encounter. Phishing attempts, in particular, often appear legitimate, making it crucial to verify the authenticity of any email or message requesting sensitive information. Careful scrutiny and awareness of common red flags are vital in avoiding these threats.
Data breaches, often caused by vulnerabilities in online systems, can expose vast amounts of personal information. These breaches can have significant consequences, including identity theft, financial loss, and reputational damage. Being aware of these potential threats is essential to take preventive measures.
Strong Passwords and Account Security
Strong passwords are the first line of defense against unauthorized access. Using unique and complex passwords for each online account is essential to prevent hackers from gaining access to multiple accounts with a single compromised password. Employing password managers can greatly simplify this process while enhancing security.
Regularly updating your passwords and enabling two-factor authentication adds an extra layer of security. This combination of measures significantly reduces the risk of unauthorized access to your accounts and personal information.
Safe Browsing Practices
Practicing safe browsing habits is crucial for protecting your personal data. Avoiding suspicious websites and downloads can prevent malware infections and data breaches. Always double-check the legitimacy of websites before entering any personal information. Be wary of links or attachments from unknown senders.
Social Media Privacy Settings
Social media platforms collect significant amounts of personal data. Understanding and adjusting your privacy settings on these platforms is essential to control who can access your information. Carefully review and modify your privacy settings to limit the visibility of your personal information to those you want to share with. This proactive approach can help to minimize the risk of unauthorized access.
Data Encryption and Security Software
Data encryption plays a vital role in protecting sensitive information. Using encryption software for your personal files and communications ensures that even if data is intercepted, it remains unreadable to unauthorized individuals. Investing in reliable security software and keeping it updated can provide an extra layer of protection against malware and other threats. It's important to regularly scan for and remove any threats.
Staying Informed and Educated
Staying informed about the latest cybersecurity threats and best practices is crucial. Following reputable cybersecurity blogs and news sources can keep you up-to-date on emerging threats and recommended safety measures. Proactively seeking out and applying this knowledge will help you stay ahead of the curve in protecting your personal information online. This continuous learning process will equip you with the necessary tools and knowledge to mitigate risks effectively.