Traditional virtual private networks (VPNs) have long been a cornerstone of online security, providing a secure tunnel for data transmission. They encrypt internet traffic, masking users' IP addresses, and effectively creating a private network connection. However, their effectiveness in today's complex and rapidly evolving threat landscape is increasingly called into question. This reliance on a single point of encryption can leave users vulnerable in a multi-faceted threat environment.
While VPNs offer a basic layer of protection, they are often insufficient to address the sophisticated attacks and vulnerabilities that modern hackers employ. This reliance on a single point of encryption can leave users vulnerable in a multi-faceted threat environment.
Limited Security Features
Traditional VPNs typically focus on encrypting data in transit. While this is crucial, it often fails to address security concerns arising from malicious software, phishing attempts, or compromised devices. The lack of comprehensive endpoint protection leaves a significant gap in securing the entire user experience.
A significant limitation is the potential for vulnerabilities within the VPN server infrastructure itself. Compromised servers can expose users to a variety of attacks, including data breaches and unauthorized access. This highlights a fundamental weakness in relying solely on a centralized VPN service.
Lack of Endpoint Security
Traditional VPNs primarily protect data during transmission. This leaves the endpoint devices, whether computers, smartphones, or tablets, vulnerable to malware, viruses, and other threats. Without robust endpoint security, VPNs fail to provide a comprehensive defense against the growing sophistication of cyberattacks.
This lack of endpoint security is a critical flaw. A compromised device can expose the entire VPN connection and potentially allow malicious actors to access sensitive data even when the VPN is active.
Inability to Address Zero-Day Exploits
Zero-day exploits are vulnerabilities in software that are unknown to the developer or security community. Traditional VPNs are ill-equipped to defend against these exploits, as they rely on known vulnerabilities and signatures. This leaves users exposed to attacks that exploit previously unknown weaknesses in their devices or applications.
The constant emergence of new exploits highlights the limitations of traditional VPN approaches. Traditional VPNs often lack the dynamic adaptation needed to counter these rapidly evolving threats.
Scalability and Management Challenges
Managing a large number of VPN connections can be complex and resource-intensive. This scalability issue is often a major concern for businesses and organizations with numerous employees and remote workers. Traditional VPNs can struggle to keep pace with the ever-increasing demand for secure access across a dispersed workforce.
The complexities of managing and maintaining VPN infrastructure can create significant overhead costs and operational difficulties. The need for constant updates and maintenance can prove challenging for smaller organizations or those with limited IT resources.
Limited Integration with Modern Security Tools
Traditional VPNs often operate in isolation from other security tools, such as intrusion detection systems or endpoint protection software. This lack of integration can create security silos and hinder the comprehensive protection of sensitive data. Modern security architectures require a more holistic and integrated approach.
The fragmented nature of security tools and the lack of seamless integration with traditional VPNs can lead to gaps in security coverage and a reduced overall effectiveness in protecting against advanced threats. A more unified approach is essential for addressing the complexities of today's threat landscape.
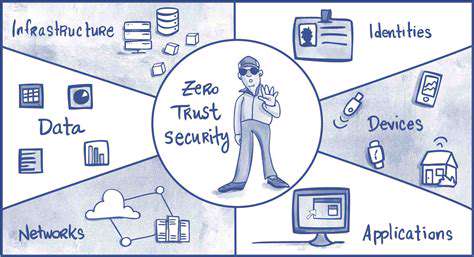
Zero Trust: Shifting from Perimeter-Based Security to Micro-segmentation
Understanding the Zero Trust Model
Zero Trust security operates on the principle that no user or device should be automatically trusted within an organization's network. This contrasts sharply with traditional perimeter-based security, which relies on a secure network boundary to protect internal resources. Instead of assuming trust, Zero Trust verifies every user and device attempting access, regardless of their location or prior access history. This granular approach significantly reduces the attack surface and enhances security posture.
Essentially, Zero Trust mandates continuous verification and authentication for all users and devices. This means that even if a user is authenticated and granted initial access, their access to specific resources or applications will still be subject to further verification and authorization.
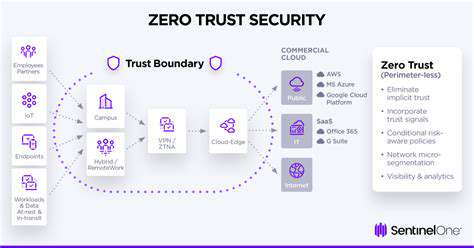
The Shift from Perimeter Security
Traditional perimeter-based security models often rely on a firewall as the primary defense mechanism. This approach assumes that anything outside the firewall is inherently untrusted, and anything inside is trusted. This strategy, while effective in some cases, becomes increasingly vulnerable in today's complex and dynamic threat landscape.
The reliance on a fixed perimeter is no longer sufficient. Modern threats, including sophisticated malware and insider threats, can easily bypass traditional security measures. Zero Trust security proactively addresses this by eliminating the implicit trust assumption, requiring continuous verification of every access request.
Micro-segmentation: A Key Component of Zero Trust
Micro-segmentation is a crucial component of a Zero Trust security strategy. It involves dividing the network into smaller, isolated segments, further limiting the potential impact of a breach. By segmenting the network, administrators can restrict access to specific resources and applications based on the user's role and needs.
This granular control allows organizations to minimize the scope of a compromise if an attacker gains access to a particular segment. Instead of having a large, interconnected network where a breach in one area can quickly escalate, micro-segmentation creates smaller, isolated zones, thus containing the damage.
Enhancing Security Posture with Zero Trust
Zero Trust security significantly enhances an organization's overall security posture by drastically reducing the attack surface. By verifying every user and device, organizations can identify and mitigate potential threats in real-time.
This proactive approach to security allows for faster incident response, minimizes the time a threat actor has to exploit vulnerabilities, and ultimately, reduces the potential for data breaches and other security incidents. This proactive approach to security is vital in today's increasingly complex threat landscape.
Beyond VPN: A New Approach to Access
Zero Trust represents a paradigm shift beyond traditional VPN-based access. VPNs often rely on establishing a secure tunnel between a user and the network, which can create a single point of failure. In a Zero Trust environment, access is granted on a granular level, based on the individual user's needs and permissions.
This granular control eliminates the need for a broad VPN connection, enhancing security and improving network performance. Zero Trust ensures that access to sensitive data and resources is rigorously controlled, even when users are outside the corporate network.
Precision irrigation systems, often powered by satellite data, allow farmers to precisely target water application to specific plant needs. This sophisticated approach avoids overwatering, a common culprit in water waste. By analyzing real-time satellite imagery, these systems can identify areas of the field that require more or less water, adjusting irrigation schedules accordingly. This level of granular control significantly reduces water consumption without compromising crop yields, a critical aspect for sustainable agricultural practices in the face of increasing water scarcity.
The Benefits of Zero Trust for Modern Organizations
Enhanced Security Posture
Zero Trust security fundamentally shifts the paradigm from a perimeter-based approach to a continuous verification model. Instead of assuming trust based on location, every user, device, and application is continuously assessed and authorized. This granular control drastically reduces the attack surface, significantly mitigating the risk of breaches. By verifying every access request, even from within the organization's network, Zero Trust creates a more secure environment, effectively preventing lateral movement of threats should a malicious actor gain initial access.
This proactive approach to security is crucial in today's complex threat landscape, where cyberattacks are becoming increasingly sophisticated and targeted. Zero Trust's emphasis on micro-segmentation and least privilege access principles ensures that even if a compromised device or user account is exploited, the damage is contained within a defined perimeter, minimizing the potential for widespread damage and data breaches. Furthermore, the continuous monitoring and verification built into the Zero Trust model provide immediate alerts and response mechanisms, enabling organizations to proactively address threats and recover from incidents more effectively.
Improved Operational Efficiency
While security is paramount, Zero Trust also brings operational efficiencies. By automating access policies and leveraging advanced analytics, organizations can reduce manual intervention and streamline workflows. This allows IT teams to focus on strategic initiatives rather than being bogged down in routine tasks. Furthermore, the ability to dynamically adapt access based on context and user behavior reduces friction for legitimate users while maintaining a high level of security.
The improved visibility into network activity provided by Zero Trust solutions allows IT teams to better understand and manage their resources. This deeper understanding can lead to optimized resource allocation and the identification of potential bottlenecks, ultimately contributing to overall operational efficiency. In addition, the centralized management capabilities of a Zero Trust architecture can simplify administration and reduce the complexity of managing diverse security tools and policies.
Increased Agility and Adaptability
In today's rapidly evolving technological landscape, organizations need to be agile and adaptable to remain competitive. Zero Trust architecture enables this agility by providing the flexibility to adjust access policies and security measures quickly in response to changing business needs and evolving threats. This dynamic approach allows organizations to respond to new threats and challenges in a timely manner, maintaining a resilient security posture.
Zero Trust architecture fosters a more flexible and scalable approach to IT infrastructure. The ability to quickly provision and de-provision access rights, based on real-time conditions, enables organizations to adjust to changing business requirements and scale operations efficiently. This adaptability is essential for supporting modern business models and fostering innovation.
The Transition to Zero Trust: A Phased Approach

The Foundation of Zero Trust
Zero Trust security is a paradigm shift from traditional network security models. Instead of trusting users and devices based on their location within a network perimeter, Zero Trust assumes no implicit trust. This means every user and device attempting to access resources needs to be verified and authenticated before gaining any access. This fundamentally redefines the security posture of an organization, moving away from a perimeter-based approach towards a more granular and dynamic system of access control.
This fundamental shift is crucial for mitigating the increasing sophistication and frequency of cyber threats. Traditional network security methods are often insufficient in today's complex threat landscape, where attackers can easily bypass perimeter defenses and gain access to sensitive data. Zero Trust addresses this vulnerability by implementing a robust and layered security strategy that minimizes the attack surface.
Implementing Zero Trust Principles
Implementing Zero Trust principles involves a multifaceted approach that goes beyond simply deploying new technologies. It requires a complete re-evaluation of existing security policies, processes, and infrastructure. Organizations need to identify all resources that require access control, and then implement granular policies governing who can access what, when, and how.
A key aspect of implementation is the use of strong authentication methods. Multi-factor authentication (MFA) is essential to verify the identity of users and devices. Implementing robust identity and access management (IAM) systems is vital to ensure only authorized users can access sensitive data.
Zero Trust and the Cloud
The rise of cloud computing further necessitates the adoption of Zero Trust principles. Cloud environments, by their very nature, often lack traditional network boundaries. This distributed nature of cloud resources creates a significant attack surface that traditional security methods struggle to address effectively. Zero Trust provides a framework for managing access to cloud resources in a secure and controlled manner.
Benefits and Challenges of Zero Trust
Implementing Zero Trust security offers significant benefits, including improved security posture, reduced attack surface, and enhanced data protection. By verifying every user and device, Zero Trust significantly reduces the risk of unauthorized access and data breaches. However, implementing Zero Trust can present challenges, including the need for significant infrastructure changes, potential increased operational costs, and complexities in managing a large and dynamic system of access control.
These challenges must be carefully considered and addressed during the transition process, but the potential gains in security and data protection are well worth the effort, especially in today’s cyberthreat environment. Investing in robust Zero Trust security infrastructure is a strategic investment in the long-term security and success of any organization.