The Unforeseen Consequences of NotPetya
NotPetya, unlike many ransomware attacks that primarily target financial gain, operated with a different, and arguably more devastating, objective. It wasn't about encrypting files and demanding payment; it was about causing widespread disruption and damage. This unique approach, while seemingly less focused on profit, had a profound impact on global supply chains and infrastructure. Understanding this shift in ransomware tactics is crucial to comprehending the evolution of the threat and the increasing sophistication of modern cyberattacks.
The attack's destructive nature extended far beyond the immediate targets, demonstrating the potential for ransomware to cause significant ripple effects throughout interconnected systems. The sheer scale of the disruption, coupled with the lack of a clear ransom demand, highlighted a new level of malicious intent and a calculated strategy to inflict maximum damage rather than solely focusing on financial gain.
Beyond Encryption: The Rise of Disruption
NotPetya's actions dramatically illustrated a crucial shift in ransomware tactics – moving beyond simple file encryption to encompass broader system disruption. This approach, characterized by its destructive potential, was a turning point in the evolution of ransomware, showcasing the attackers' willingness to prioritize widespread damage over immediate financial gain. The long-term consequences for businesses and critical infrastructure were significant and underscored the evolving nature of cyber threats.
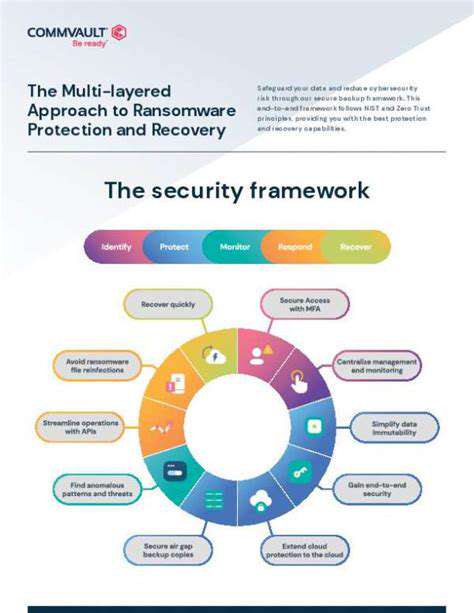
This shift from purely financial motivations to a more destructive agenda, exemplified by NotPetya, has profound implications for cybersecurity strategies. Organizations need to move beyond a reactive approach that focuses solely on recovering encrypted files and begin to anticipate and mitigate the potential for broader system disruption. Proactive measures that emphasize robust system security and disaster recovery planning are more critical than ever.
The Legacy of NotPetya: Shaping Future Threats
The widespread disruption caused by NotPetya had a lasting impact on the cybersecurity landscape, prompting a reassessment of vulnerabilities and the need for enhanced security measures. The attack exposed the critical need for robust defenses across supply chains and emphasized the interconnectedness of modern systems, where a single point of failure can have cascading effects. This realization has led to increased emphasis on proactive security measures and the development of more sophisticated incident response strategies.
NotPetya's legacy extends beyond its immediate impact. The attack served as a wake-up call, prompting organizations to adopt more resilient and adaptable security strategies. Understanding the evolution of ransomware threats, including the shift from pure financial gain to broader disruption, is vital for creating effective defenses and mitigating the potential damage that modern attacks can inflict.
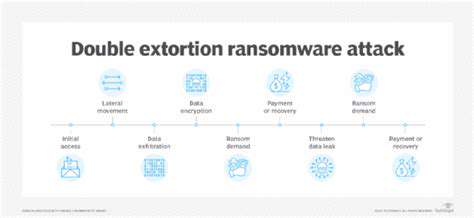

The Ongoing Threat: Adapting to Evolving Tactics

The Evolving Landscape of Ev
The threat landscape surrounding evolutions is constantly shifting, demanding a proactive and adaptable approach. Technological advancements, coupled with evolving societal needs, are creating new vulnerabilities and opportunities. Understanding these dynamics is crucial for effective mitigation and adaptation. We must not only anticipate future challenges but also remain vigilant to emerging threats.
Governments, businesses, and individuals must collaborate to create a robust framework for addressing the evolving challenges associated with evolutions. This includes fostering innovation in security measures, promoting awareness and education, and developing comprehensive response plans.
The Impact of Ev on Global Economies
The impact of evolutions on global economies is multifaceted and significant. Positive impacts include the creation of new markets, job opportunities, and technological advancements. However, negative impacts such as disruptions to supply chains, economic instability, and social unrest must also be considered.
Understanding the potential economic consequences of evolutions is critical for policymakers and businesses alike. Careful planning, diversification strategies, and international cooperation are crucial to navigate the complex economic terrain that evolutions may create.
The Role of International Cooperation in Addressing Ev
International cooperation is essential for effectively addressing the challenges posed by evolutions. Sharing knowledge, resources, and best practices across borders is crucial for developing comprehensive solutions. This includes fostering dialogue and collaboration between nations, organizations, and experts.
Collaborative initiatives can accelerate the development of effective mitigation strategies, promote global stability, and reduce the potential for widespread damage. Open communication and information sharing are key components of any successful international response to evolutions.
Adapting to the Unpredictability of Ev
The unpredictability of evolutions necessitates a flexible and adaptable approach. Proactive measures are essential to anticipate and mitigate potential risks. This includes developing contingency plans, fostering resilience, and maintaining a focus on ongoing monitoring and evaluation.
Security Implications of Ev
Evolutions raise significant security implications, affecting both physical and digital landscapes. Protecting critical infrastructure, maintaining data integrity, and safeguarding intellectual property are paramount concerns. Strong cybersecurity measures and robust physical security protocols are necessary to prevent exploitation and disruption.
Moreover, the evolving nature of evolutions requires continuous adaptation of existing security measures and the development of innovative solutions to emerging threats. This includes educating the public about potential risks and promoting responsible behavior online and offline.
The Ethical Considerations Surrounding Ev
The ethical implications of evolutions are complex and multifaceted. Questions surrounding equitable access, responsible use, and potential biases must be addressed proactively. Promoting transparency, accountability, and ethical guidelines is essential.
Furthermore, fostering public dialogue and engagement is critical to navigating the ethical complexities associated with evolutions. This includes establishing clear guidelines, promoting responsible innovation, and ensuring that the benefits of evolutions are shared equitably.