The Growing Threat Landscape in Modern Supply Chains
Vulnerabilities in Globalized Networks
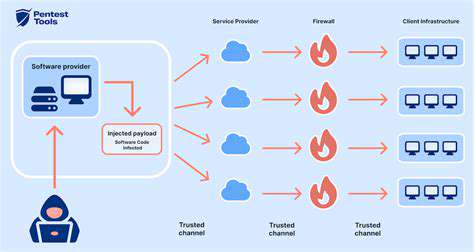
Globalization has undeniably boosted efficiency in modern supply chains, but it has also created complex and interconnected networks that are susceptible to disruptions. The intricate web of suppliers, manufacturers, and distributors across continents introduces numerous potential vulnerabilities. These range from natural disasters impacting critical transportation routes to geopolitical instability affecting raw material access, and even cyberattacks targeting sensitive data or operational systems. Understanding and mitigating these vulnerabilities is crucial for maintaining resilience and stability within the supply chain.
The Rise of Cyber Threats
Cyberattacks are rapidly evolving and becoming more sophisticated, posing a significant threat to supply chains. Malicious actors can target various points along the chain, from stealing sensitive intellectual property to disrupting manufacturing processes or even manipulating product quality. The increasing reliance on digital systems and interconnected technologies makes supply chains more exposed to cyberattacks, necessitating robust cybersecurity measures and proactive threat detection strategies.
This includes not only protecting internal systems but also ensuring that the security protocols of all partners and suppliers are up to par, a significant challenge in a globalized environment. The interconnected nature of modern supply chains necessitates a collaborative approach to security.
The Impact of Geopolitical Instability
Geopolitical events, such as trade wars, sanctions, and political unrest, can disrupt supply chains by affecting the availability of raw materials, transportation routes, and labor resources. These disruptions can lead to significant delays, increased costs, and even complete shutdowns of production lines. The unpredictability and potential severity of these events highlight the need for supply chain resilience strategies that include diversification of sourcing and alternative transportation options.
The Importance of Data Security and Transparency
Maintaining the confidentiality, integrity, and availability of sensitive data is paramount in modern supply chains. Data breaches can compromise intellectual property, customer information, and financial records, leading to significant financial losses and reputational damage. Implementing robust data security measures and fostering transparency throughout the supply chain are crucial to minimizing these risks. This includes establishing clear data governance policies and promoting secure data sharing practices among all stakeholders.
The Need for Enhanced Risk Management
Proactive risk management is essential to navigating the evolving threat landscape. Companies need to identify potential risks, assess their likelihood and impact, and implement mitigation strategies. This involves analyzing various factors, from natural disasters and geopolitical events to cybersecurity threats and supply chain disruptions. A robust risk management framework, combined with continuous monitoring and adaptation, is critical for building a resilient and secure supply chain. Regular audits and assessments of the entire supply chain are essential to identify weak points and proactively address emerging threats.
Implementing SBOMs for Effective Cybersecurity

Implementing SBOMs for Improved Supply Chain Security
Software Bill of Materials (SBOMs) are becoming increasingly crucial for organizations aiming to enhance the security posture of their software supply chains. An SBOM is a comprehensive list of all the software components that make up a piece of software, including their versions and licenses. This detailed inventory provides a clear understanding of the software's dependencies and potential vulnerabilities, enabling proactive risk mitigation strategies. By having a complete and accurate SBOM, organizations can better identify and address security risks earlier in the development lifecycle.
The growing prevalence of open-source components in modern software development has significantly increased the complexity of managing software dependencies. This complexity leads to a higher risk of introducing vulnerabilities from unknown or unpatched components. SBOMs empower organizations to effectively manage this complexity, enabling a more secure and reliable software development process. Organizations can effectively track the versions of all the components used in their software, facilitating a more structured and proactive approach to security.
Benefits of Implementing SBOMs in Software Development
Implementing SBOMs offers numerous benefits beyond simply improving security. These benefits encompass enhanced visibility into the software supply chain, enabling organizations to understand the components making up a software product, and proactively identify potential vulnerabilities before they are exploited. This proactive approach helps prevent breaches and reduces the overall risk profile associated with software development. Moreover, having an accurate SBOM allows for more efficient vulnerability management by providing a clear picture of the software's components and their associated risks.
Improved collaboration and communication within the software development lifecycle are also key advantages of using SBOMs. Developers and security teams can more effectively collaborate by having a common understanding of the software's components and potential vulnerabilities. Sharing this information facilitates the identification and resolution of vulnerabilities throughout the development lifecycle. This collaborative approach strengthens the overall security posture of the organization.
Key Considerations for Implementing SBOMs
Implementing SBOMs requires careful consideration of several factors to ensure successful adoption. One critical aspect is defining clear processes for generating SBOMs throughout the software development lifecycle. The processes should be automated and integrated with existing development tools and workflows to ensure consistent and reliable data generation. This will reduce the manual effort and improve accuracy.
Another crucial consideration is choosing appropriate tools and technologies to support SBOM generation and analysis. The tools should be capable of handling a wide range of software components and providing comprehensive vulnerability analysis capabilities. Organizations should also consider the need for ongoing training and development to ensure that their teams are equipped to effectively utilize SBOMs in their daily workflows.