Understanding Your Current Financial Situation
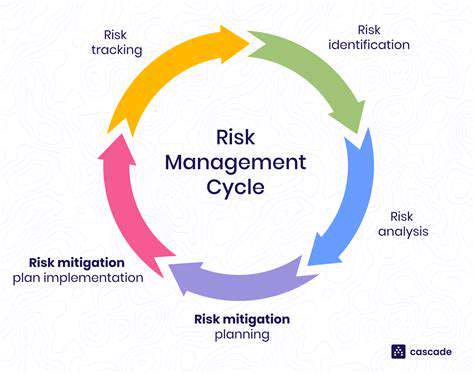
A crucial first step in any financial improvement journey is a thorough assessment of your current financial state. This involves meticulously reviewing all income sources, including salary, investments, and any other forms of revenue. Accurately documenting these sources is essential for understanding your overall financial capacity. Furthermore, a detailed analysis of your expenses is necessary. This includes categorizing expenditures into essential needs, discretionary spending, and debt obligations. Identifying areas where you can potentially cut back on spending is a critical component of this process.
Understanding your current financial situation is not just about the numbers; it's about understanding the patterns and habits that have led to your current state. Are you living paycheck to paycheck? Do you have significant debt burdens? Identifying these patterns is the first step toward developing a sustainable financial plan. This self-assessment will provide a clear picture of your financial health, which can be used to guide your future financial decisions.
Identifying Key Financial Goals
Once you have a clear understanding of your current financial state, it's time to define your financial goals. These goals should be specific, measurable, achievable, relevant, and time-bound (SMART). For example, instead of a vague goal like save more money, a SMART goal would be save $5,000 in savings by the end of the year. Setting tangible goals provides a roadmap and motivation for your financial journey. These goals should align with your personal values and aspirations, whether it's purchasing a home, funding your children's education, or retiring comfortably.
Consider both short-term and long-term goals. Short-term goals, such as paying off high-interest debt, can provide immediate relief and build confidence. Long-term goals, such as retirement planning or wealth building, require a more strategic approach and long-term commitment.
Evaluating Your Income Sources and Streams
A thorough assessment of your income sources is crucial for understanding your financial capacity. Review all salary, wages, investment income, side hustles, and any other sources of revenue. Documenting these sources helps you gain a complete picture of your financial inflows. Accurate income tracking is essential for budgeting and financial planning. This evaluation will allow you to identify potential gaps or areas where you can potentially increase your income streams.
Analyzing Your Spending Habits
A critical component of assessing your current state is examining your spending habits. Detailed tracking of your expenses, including necessities like rent, food, and utilities, as well as discretionary spending, is essential. Categorizing your expenditures into various categories, such as housing, transportation, food, entertainment, and debt payments, can reveal areas where you may be overspending. Understanding where your money is going is a crucial part of managing your finances effectively. This analysis is vital for identifying patterns and areas where you can reduce unnecessary spending.
Reviewing Your Debt Obligations
Evaluating your debt obligations is an integral part of assessing your current financial state. This includes reviewing the amounts owed, interest rates, and repayment schedules for all outstanding loans, credit cards, and other debts. Analyzing your debt burden provides insights into your potential financial risks and the impact of debt on your overall financial health. A critical step is understanding the implications of each debt obligation to prioritize repayment strategies.
Mitigating Risks: Implementing Security Controls
Implementing Robust Access Controls
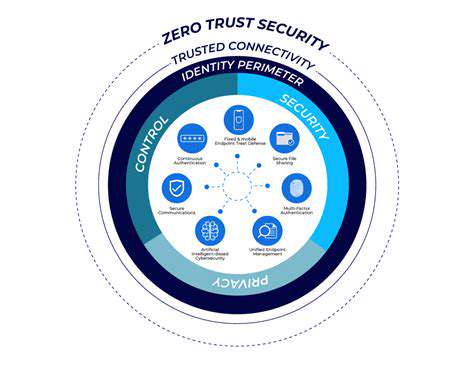
Effective access controls are paramount to mitigating risks within your digital supply chain. These controls dictate who has permission to access sensitive data, systems, and resources. Implementing a strong access control matrix, employing least privilege principles, and regularly reviewing and updating access permissions are crucial steps. This approach not only reduces the potential for unauthorized access but also helps maintain compliance with industry regulations and internal policies, ultimately safeguarding your organization's sensitive information.
Multi-factor authentication (MFA) should be a mandatory requirement for all users accessing critical systems and data. This added layer of security significantly reduces the risk of unauthorized access even if a password is compromised.
Employing Secure Configuration Management
Maintaining consistent and secure configurations across all systems within the supply chain is vital. This includes servers, workstations, and network devices. Automated tools and processes can help ensure that configurations adhere to defined security policies and standards. Regular audits and updates are essential to detect and address any deviations from the secure baseline, minimizing vulnerabilities.
Using predefined templates and scripts for system deployment and configuration can significantly reduce the risk of human error and ensure consistency in security posture across all components.
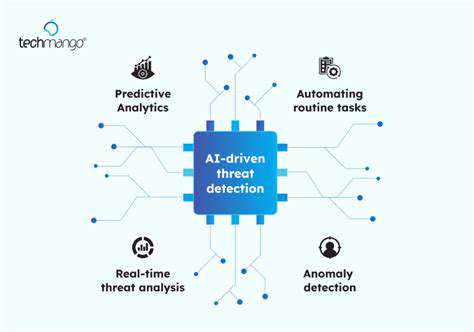
Regular Vulnerability Assessments and Penetration Testing
Proactive identification and remediation of vulnerabilities are critical for a robust security posture. Regular vulnerability assessments and penetration testing help uncover potential weaknesses in your systems and applications. These assessments should cover not only your internal systems but also those of your suppliers and partners, ensuring a comprehensive view of the entire supply chain.
The results of these assessments should be meticulously analyzed, and appropriate remediation actions implemented promptly. This continuous process helps to proactively address security threats before they can be exploited.
Enhancing Data Loss Prevention (DLP) Measures
Data loss prevention (DLP) is crucial for safeguarding sensitive data throughout the entire digital supply chain. Implementing DLP technologies can help detect and prevent sensitive data from leaving the organization's control, whether through accidental disclosure or malicious intent. This includes controlling data access, encryption, and monitoring for unusual data movement.
Implementing Secure Software Development Practices
Security should be integrated into every stage of the software development lifecycle (SDLC). This includes incorporating security considerations into requirements gathering, design, development, testing, and deployment. Employing secure coding practices and performing regular code reviews can help identify and address potential vulnerabilities early on.
This proactive approach minimizes the risk of introducing vulnerabilities during the software development process and ensures that software delivered into the supply chain is secure and robust.
Establishing Incident Response Plans
A well-defined incident response plan is essential for handling security incidents effectively. This plan should outline procedures for detecting, containing, responding to, and recovering from security breaches. Regularly testing and updating the incident response plan ensures that the organization is prepared to handle any potential security incidents that may arise throughout the supply chain.
Collaboration between internal teams and external partners is critical during an incident response. This collaborative approach enhances the effectiveness of the response and minimizes the impact of the incident.
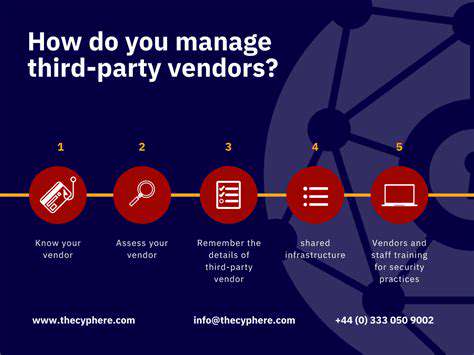
Strengthening Supplier Security Requirements
A strong security posture extends beyond your organization's walls; it must encompass your entire supply chain. Implementing stringent security requirements for all suppliers is crucial. This includes conducting thorough due diligence on potential suppliers, establishing clear security expectations, and regularly monitoring their security practices.
Requiring suppliers to adhere to specific security standards and certifications can help ensure that they maintain a strong security posture, thereby reducing vulnerabilities within the supply chain. This proactive approach ensures a more secure and reliable environment for your organization.